BOOK THIS SPACE FOR AD
ARTICLE AD
Apple has rolled out security updates to address dozens of iOS and macOS vulnerabilities, including a severe iOS bug dubbed WiFiDemon that could lead to denial of service or arbitrary code execution.
The vulnerability, tracked as CVE-2021-30800 and a zero-day bug when security researcher Carl Schou publicly disclosed it, was fixed by Apple with the release of iOS 14.7 earlier this week.
Successful exploitation would make it possible to break an iPhone's Wi-Fi functionality on joining hotspots with SSIDs containing the "%" character (i.e., %p%s%s%s%s%n).
Once triggered on a vulnerable iPhone, iPad, or iPod, the bug would render it unable to establish Wi-Fi connections, even after rebooting or renaming the Wi-Fi hotspot.
Fixing the Wi-Fi breaking issue requires resetting network settings to remove the names of all Wi-Fi networks, including the rogue ones, from the lists of known SSIDs.
Zero-click RCE risks on older iOS versions
As ZecOps later found, threat actors could also execute arbitrary code without user interaction when unpatched devices joined a rogue Wi-Fi hotspot with a maliciously crafted SSID containing the "%@" character (i.e., DDDD%x%x%x%@)
Luckily, as mobile security startup ZecOps revealed, the zero-click remote code execution component of WiFiDemon was only present starting with iOS 14.0 and was silently addressed by Apple with the release of iOS 14.4.
Attackers could exploit this bug by planting malicious Wi-Fi hotspots in popular and highly circulated areas to attack iPhone devices configured to auto-join new Wi-Fi networks.
If you don't want to or cannot immediately update your iOS device to iOS 14.7 to secure it from WiFiDemon attacks, you are advised to disable the Wi-Fi Auto-Join feature by choosing 'Never' on the Settings> Wi-Fi>Auto-Join Hotspot option.
The bug impacts iPhone 6s and later, all iPad Pro models, iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation), as Apple revealed in a security advisory published earlier this week.
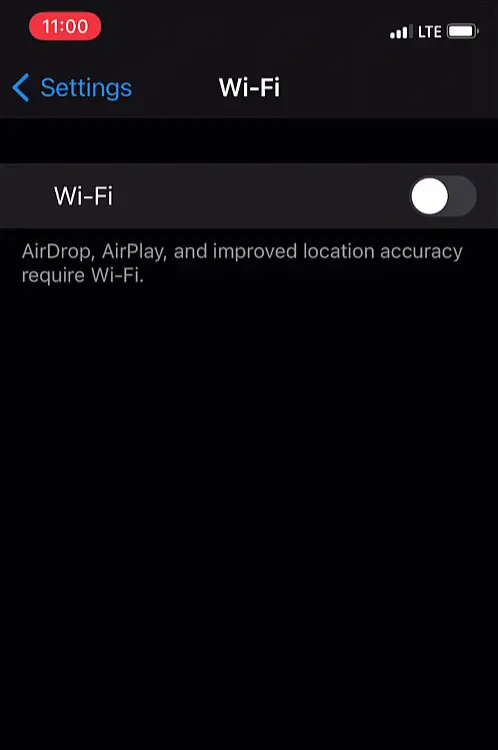 Wi-Fi functionality disabled after joining a "%p%s%s%s%s%n" SSID
Wi-Fi functionality disabled after joining a "%p%s%s%s%s%n" SSIDApple patches stream of zero-days
Since March, Apple has been busy released security updates to address a seemingly endless wave of zero-day bugs—nine of them in total—most of them also exploited in the wild.
Last month, the company fixed two iOS zero-day bugs (CVE-2021-30761 and CVE-2021-30762) that "may have been actively exploited" to hack into older iPhone, iPad, and iPod devices.
Apple patched a macOS zero-day (CVE-2021-30713) in May, a vulnerability abused by the XCSSET malware to bypass Apple's TCC protections designed to safeguard users' privacy.
The same month, Apple also fixed three other zero-days (CVE-2021-30663, CVE-2021-30665, and CVE-2021-30666), bugs allowing for arbitrary remote code execution (RCE) on vulnerable devices simply by visiting malicious websites.
The company addressed one more iOS zero-day (CVE-2021-1879) in March and zero-days in iOS (CVE-2021-30661) and macOS (CVE-2021-30657) in April.
The Shlayer macOS malware exploited the latter to bypass Apple's File Quarantine, Gatekeeper, and Notarization security checks and deliver second-stage malicious payloads on compromised Macs.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·