Apple on Monday rolled out security updates for iOS, macOS, tvOS, watchOS, and Safari web browser to fix multiple vulnerabilities, including an actively exploited zero-day flaw in macOS Big Sur and expand patches for two previously disclosed zero-day flaws.
Tracked as CVE-2021-30713, the zero-day concerns a permissions issue in Apple's Transparency, Consent, and Control (TCC) framework in macOS that maintains a database of each user's consents. The iPhone maker acknowledged that the issue may have been exploited in the wild but stopped short of sharing specifics.
The company noted that it rectified the problem with improved validation.
However, in a separate report, mobile device management company Jamf said the bypass flaw was being actively exploited by XCSSET, a malware that's been out in the wild since August 2020 and known to propagate via modified Xcode IDE projects hosted on GitHub repositories and plant malicious packages into legitimate apps installed on the target system.
"The exploit in question could allow an attacker to gain Full Disk Access, Screen Recording, or other permissions without requiring the user's explicit consent — which is the default behavior," Jamf researchers Stuart Ashenbrenner, Jaron Bradley, and Ferdous Saljooki said in a write-up.
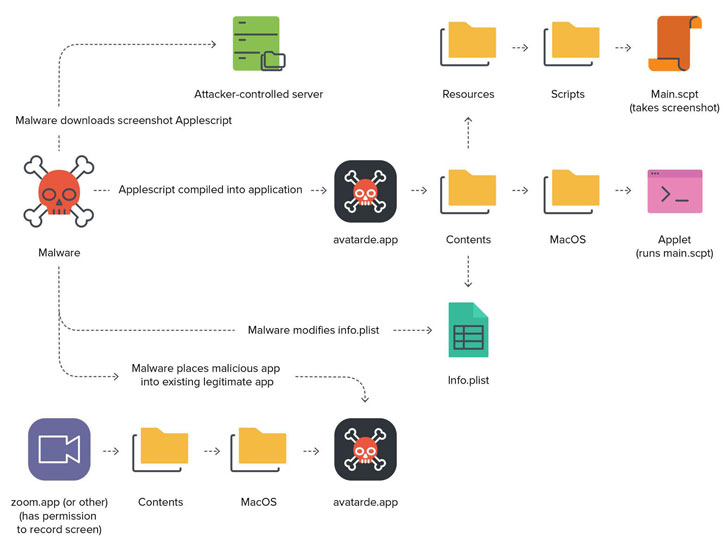
Taking the form of a AppleScript module, the zero-day flaw allowed the hackers to exploit the devices XCSSET was installed to leverage the permissions that have already been provided to the trojanized application to amass and exfiltrate sensitive information.
Specifically, the malware checked for screen capture permissions from a list of installed applications, such as Zoom, Discord, WhatsApp, Slack, TeamViewer, Upwork, Skype, and Parallels Desktop, to inject the malware ("avatarde.app") into the app's folder, thereby inheriting the necessary permissions required to carry out its nefarious tasks.
"By leveraging an installed application with the proper permissions set, the attacker can piggyback off that donor app when creating a malicious app to execute on victim devices, without prompting for user approval," the researchers noted.
XCSSET was also the subject of closer scrutiny last month after a new variant of the malware was detected targeting Macs running on Apple's new M1 chips to steal wallet information from cryptocurrency apps. One of its primary functions is to siphon Safari browser cookies as well as install a developer version of the Safari application to load JavaScript backdoors from its command-and-control server.
Also fixed as part of Monday's updates are two other actively exploited flaws in its WebKit browser engine affecting Safari, Apple TV 4K, and Apple TV HD devices, almost three weeks after Apple addressed the same issues in iOS, macOS, and watchOS earlier this month.
CVE-2021-30663 - An integer overflow issue in WebKit, which could be exploited to achieve arbitrary code execution when processing maliciously crafted web content. CVE-2021-30665 - A memory corruption issue in WebKit that could lead to arbitrary code execution when processing maliciously crafted web content.Users of Apple devices are recommended to update to the latest versions to mitigate the risk associated with the flaws.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
196
3 years ago
196 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·