BOOK THIS SPACE FOR AD
ARTICLE ADThe researcher found that he could gain unauthorized camera access via a shared iCloud document that could also “hack every website you’ve ever visited.”
A researcher who showed Apple how its webcams can be hijacked via a universal cross-site scripting bug (UXSS) Safari bug has been awarded what is reportedly a record $100,500 bug bounty. The bug could be used by an adversary as part of an attack to gain full access to every website ever visited by the victim.
The bug-finder is Ryan Pickren, founder of proof-of-concept sharing platform BugPoC and a former Amazon Web Services security engineer. This isn’t the first time he’s found bugs that let him hoodwink Apple’s cameras: In 2020, he discovered vulnerabilities in the Safari browser that could be used to snoop on iPhones, iPads and Mac computers using their microphones and cameras, just by convincing a target to click one malicious link.
Great research once again from Ryan Pickren for those looking for Apple bugs: Gaining unauthorized camera access via Safari UXSShttps://t.co/SP8duGpq8T
— Jon Bottarini (@jon_bottarini) January 25, 2022
This time around, according to Pickren, he found a series of flaws – in Safari 15 and iCloud Sharing – that could again lead to unauthorized camera access, which would again allow an attack to be launched from a malicious site.
But his more recent find is worse: It could also enable a shared iCloud document to “hack every website you’ve ever visited,” he said, and could steal permissions to use multimedia – in other words, the microphone, camera and screensharing.
Pickren reported that the same hack could result in an attacker gaining full access to a device’s entire filesystem, y exploiting Safari’s webarchive files, which are the files Safari creates as an alternative to HTML when it saves a website locally.
Pickren submitted the bugs to Apple last July. The iPhone-maker patched the issues earlier this month and subsequently awarded the $100,500 bug bounty to Pickren.
The Bugs
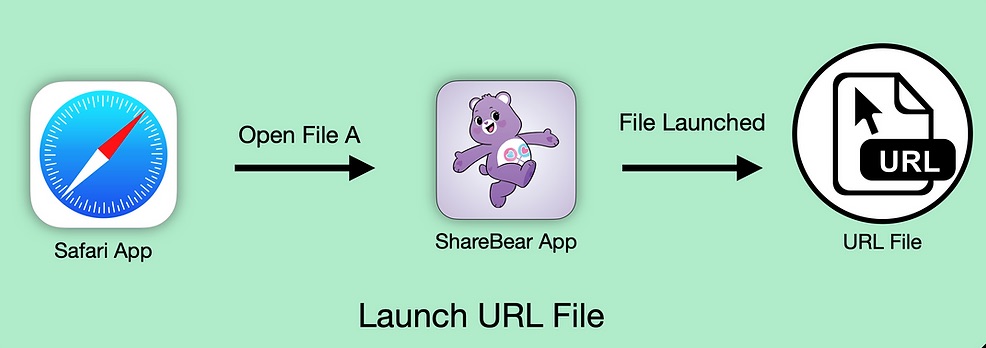
The issues are found in ShareBear, a behind-the-scenes iCloud file-sharing app that prompts users when they try to open a shared document for the first time – and only the first time. Since users aren’t presented with the display again once they’ve accepted the prompt to open the file, Pickren found that anyone who has access to the file can alter the file’s content after that occurs.
“ShareBear will then download and update the file on the victim’s machine without any user interaction or notification,” Pickren explained in his technical write-up. “In essence, the victim has given the attacker permission to plant a polymorphic file onto their machine and the permission to remotely launch it at any moment.”
These three steps are involved in using ShareBear to download and open a webarchive file:
Trick the victim into giving permission to plant the polymorphic file; Turn an image file with a .PNG format – he gave the example of puppies.png – into an executable binary (“evil.dmg) after a user has agreed to open it and then to open it; The binary triggers an exploit chain that leverages other flaws discovered in Safari in order to take over the machine’s microphone or webcam, or even to steal local files.Stages of ShareBear attack. Source: Ryan Pickren.
Pickren identified four zero-day bugs, the following of which have received CVE tracking numbers:
CVE-2021-30861: A logic issue in Webkit, rated at 5.5 in criticality, that Apple addressed with improved state management in macOS Monterey 12.0.1. The bug could allow a malicious application to bypass checks done by Gatekeeper: a macOS security feature that attempts to reduce the likelihood of inadvertently executing malware by enforcing code signing and verifying downloaded applications before allowing them to run. CVE-2021-30975: An issue in macOS Monterey’s Script Editor with a base criticality score of High – 8.6 – that may allow a malicious OSAX scripting addition to bypass Gatekeeper checks and circumvent sandbox restrictions. Apple addressed the issue by disabling execution of JavaScript when viewing a scripting dictionary.“This project was an interesting exploration of how a design flaw in one application can enable a variety of other, unrelated, bugs to become more dangerous,” Pickren concluded. “It was also a great example of how even with macOS Gatekeeper enabled, an attacker can still achieve a lot of mischief by tricking approved apps into doing malicious things.”
Check out our free upcoming live and on-demand online town halls – unique, dynamic discussions with cybersecurity experts and the Threatpost community.
.png)


















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·