BOOK THIS SPACE FOR AD
ARTICLE ADOne of the world's biggest cyberinsurance companies, AXA, was hit with a ransomware attack at its offices in Asia this weekend by noted ransomware gang Avaddon.
In a statement to ZDNet, a spokesperson for AXA Partners said a targeted ransomware attack disrupted their IT operations in Thailand, Malaysia, Hong Kong, and the Philippines. Certain data processed by Inter Partners Asia in Thailand has been accessed, the spokesperson explained, but there was no evidence any other data was accessed.
The company has hired a forensic team to investigate the incident and said it notified business partners as well as regulators while it prepares to support all of the clients who may have been impacted.
Members of the Avaddon group wrote on its dark web site that it has already taken three terabytes of data from AXA Group and that the files include information like passports, ID cards, denied reimbursements, contracts, customer claims, payments to customers, bank account information, files from hospitals about fraud investigations and medical reports that had sensitive information about patients. The group even posted samples of the data.
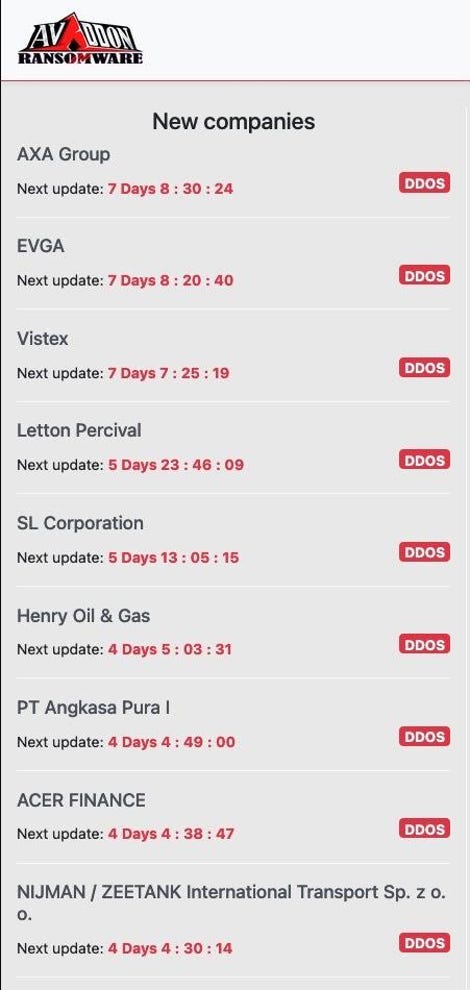
DomainTools researcher Chad Anderson said people behind the ransomware gang Avaddon had posted about their latest victim on a dark web page, sharing a screenshot with ZDNet of the group's list of targets as well as timers for how long each victim has until ransom will be demanded.
 Chad Anderson
Chad Anderson
The companies on the list include AXA Group, computer hardware company EVGA, software company Vistex, insurance broker Letton Percival, Henry Oil & Gas, the Indonesian government's airport company PT Angkasa Pura I, and Acer Finance.
Both the FBI and Australian Cyber Security Centre released warning notices last week about Avaddon's ransomware tactics.
AXA has about three days left, according to Anderson, before Avaddon members have said they will begin leaking the company's documents.
The cyberinsurance company has been in the news recently because they pledged to stop reimbursing customers in France who had been hit by ransomware attacks and decided to pay the ransom. The decision was made after pressure from French regulators who said the insurance payouts were fueling higher ransom payments and making the crimes lucrative for the gangs behind them.
"In total, since their discovery in June 2020, the Avaddon gang has published data on dozens of victims on their dark web site, following the now common double-extortion technique amongst ransomware operators," Anderson said. "Avaddon also maintains an affiliate program where they recruit hackers from underground forums to deploy their ransomware. This most recent intrusion shows that the human operators behind these ransomware families continue to hone their skills and become continually faster at deploying on victim networks."
Cybersecurity experts said it was impossible to ignore the timing of the attack. Chris Clements, vice president of solutions architecture at Cerberus Sentinel, said Avaddon may have been targeting AXA to make an example of companies challenging their business goals.
But on a deeper level, Clements said it was proof that almost all organizations are vulnerable in some way or on some level and that the scale and complexity of modern networks makes it nearly impossible to plug every potential hole.
"Couple this with the fact that ransomware gang's extortion earnings often give them higher budgets than their target teams' defenders and it's no wonder that ransomware is epidemic across the globe," Clements said.
Netenrich security advisor Sean Cordero added that for companies as large as AXA, it is often difficult to have sufficient visibility into the cybersecurity practices and controls across their business partners and subsidiaries.
But the lessons learned from this attack, Cordero explained, may lead to better ways to collaborate for both the insured and insurer as this attack implies a weakness in risk assessment, validation, or execution.
"If an insurer like AXA struggles to validate their cyber capabilities and needs -- what is the chance that they may have incorrectly assessed the risks across their portfolio of cyber insurance clients?" Cordero asked.
"I imagine that the professionals responsible for achieving positive returns on cybersecurity policies may have renewed discussions with assessors and underwriters in the wake of this most recent incident."
.png)
 3 years ago
184
3 years ago
184 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·