BOOK THIS SPACE FOR AD
ARTICLE ADA phishing campaign uses overlay screens and email ‘quarantine’ policies to steal targets’ Microsoft Outlook credentials.
Attackers are on the prowl for enterprise Microsoft Outlook credentials, with a new phishing campaign that leverages email-quarantine policies and uses an overlay screen tactic — on top of legitimate company webpages — to lure in victims.
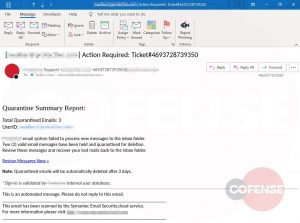
The campaign was discovered after successfully targeting an unnamed company, Cofense researchers told Threatpost. The emails imitated the technical-support team of the employee’s company (with “Support” in the sender title and “Action Required” in the subject line) and claimed that the company’s email-security service had quarantined three valid email messages, blocking them from entering the inbox.
The quarantine location on an email server is where messages are stored temporarily that are suspected to be spam. They can then be reviewed and retrieved if necessary. While not a new lure for attackers, this proves to be effective, particularly in an enterprise environment where employees fear the impact of missed communications, researchers said.
“Potential loss of important documents or emails could make the employee more inclined to interact with this email,” said Dylan Main, researcher with Cofense, in a Friday post.
The initial email said, the company’s email system “failed to process new messages in the inbox folder,” and “two valid email messages have been held and quarantined for deletion.” It asked the target to review the messages and recover their lost mail in the inbox folder – or they will be automatically deleted after three days.
“This could potentially lead the employee to believe that the messages could be import to the company and entice the employee to review the held emails,” said Main.
The email has one big red flag: When a target hovers the mouse over the link in the email, “Review Messages Now,” it shows a suspiciously long URL.
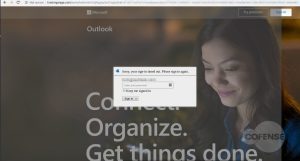
If a target should ignore such a warning sign, and click on the link in the email, it redirects to the employee’s legitimate company website with an Outlook email login screen.
While the company webpage is legitimate, researchers found that attackers had added on an overlay screen with the credential request. The fake login panel said the employee’s Outlook sign-in timed out and asked them to input their credentials.
Upon further analysis, researchers found that the phishing links used specific parameters to determine which webpage pull to use, and then deployed the fake login panel overlay on top. Depending on what company the threat actor is targeting, the link populates the address of the original recipient of the email, researchers said.
Researchers told Threatpost that the use of the overlay screen increases the appearance of legitimacy, because the target is able to view and interact with their company webpage.
“This gives the employee a greater comfort level, by displaying to a familiar page. It is also possible to interact with this page by moving outside of the overlay, showing that it is the actual page they have seen and used before,” said researchers. “The overlay itself is attempting to prompt the user to sign in to access the company account. The entered credentials are then sent to the threat actor, giving them access to the target’s company account.”
This campaign shows that phishing attackers will use any resource available to compromise business accounts, researchers warned.
Earlier this summer, for instance, researchers discovered a sophisticated new phishing campaign that used recognized brand names to bypass security filters as well as to trick victims into giving up Microsoft Office 365 credentials to gain access to corporate networks. And this past week, Turkish-speaking cybercriminals sent Instagram users seemingly legitimate messages from the social media company, with the aim of stealing their Instagram and email credentials.
In this most recent campaign, “using an overlay tactic to disguise itself, this attack is an example of how threat actors are using more advanced techniques to make these malicious emails appear as though they are from a trusted source,” they said.
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Register today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·