BOOK THIS SPACE FOR AD
ARTICLE AD
After just a few months of activity, the operators of Babuk ransomware briefly posted a short message about their intention to quit the extortion business after having achieved their goal.
Unlike other gangs that chose to release decryption keys or even return the collected ransoms, Babuk's final gesture is to pass the torch to others.
Hanging up the encryption keys
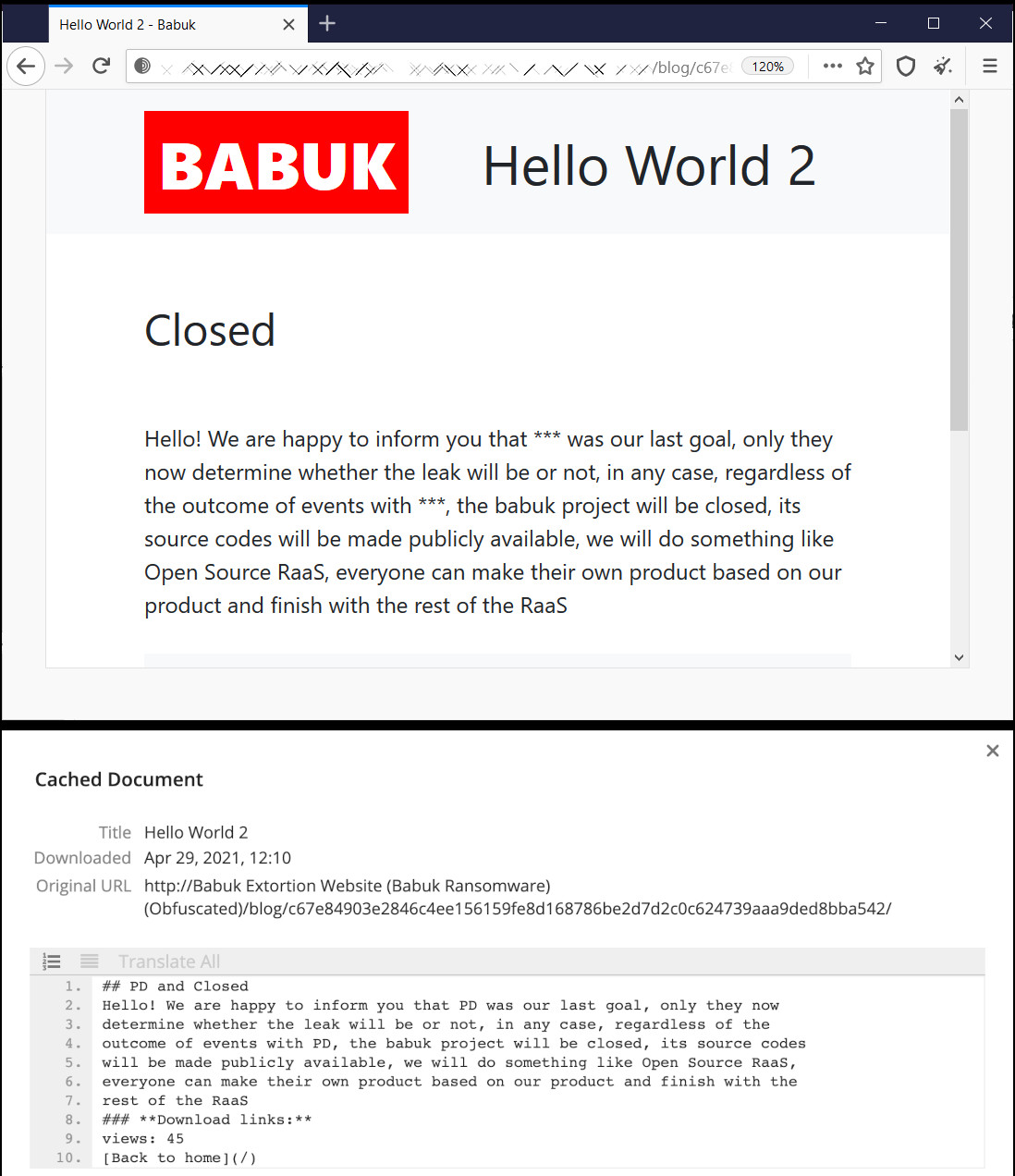
Earlier today, the Babuk ransomware gang said in a message titled "Hello World 2" on their leak site that they had achieved their goal and decided to shut down the operation.
However, they would not leave the stage without a legacy: the source code for Babuk file-encrypting malware would be publicly available once they terminated the “project.”
The message suffered modifications and was visible for a short while on the main page of the site, though. In one version captured by Dmitry Smilyanets of Recorded Future, the cybercriminals said that breaching “PD was our last goal,” a clear reference to their latest victim, the Metropolitan Police Department (MPD). As seen in the screenshot below, "PD" was also in the title.
Another variant of the message, captured by BleepingComputer, did not have "PD" mentioned at all, potentially suggesting that the gang is preparing to end its operations in the foreseeable future, after having compromised a different victim.
Nevertheless, one part of the message is clear in both versions of the message. Whenever the Babuk ransomware gang decides to call it quits, at least under the Babuk name, they would "do something like Open Source RaaS, everyone can make their own product based on our product and finish with the rest of the RaaS.”
Babuk’s latest victim is the Metropolitan Police Department (MPD), the main law enforcement agency in Washington, DC, who confirmed the breach to BleepingComputer.
This came after the cybercriminals said that they had stolen 250GB of data before encrypting MPD’s computers and published screenshots of folders stolen in the attack to prove their claims.
Brief stint, plenty of victims
Babuk ransomware emerged at the beginning of the year. Right from the start it targeted victims all over the world and demanded ransoms between $60,000 to $85,000 in bitcoin cryptocurrency.
Analysis from BleepingComputer showed that every executable of this ransomware strain was customized for each victim with a hardcoded extension, ransom note, and Tor URL for contact.
Initially, Babuk ransomware operators said that they would not target several types of organizations in the healthcare, non-profit, education, small business sector, with some exceptions.
In a subsequent post on their leak site, the gang clarified that their attacks had started since at least mid-October 2020 and removed the previously-mentioned exceptions.
It is unclear how many organizations fell victim to the Babuk ransomware operation but the leak site currently lists well over a dozen companies that did not pay the ransom.
Others may be available on hidden pages, as is now the case of the Metropolitan Police Department, which is no longer listed on the main page but still has its place on the leak site.
Of note, other ransomware gangs in the past trumpeted that they were leaving the ransomware business only to return under a different name. Even if developers retire, affiliates will jump to a different RaaS operation, as was the case when Maze shut down and Egregor ransomware adopted many of the former's affiliates.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·