BOOK THIS SPACE FOR AD
ARTICLE ADKraken has already spread like wildfire, but in the past few months, the malware’s author has been tinkering away, adding more infostealers and backdoors.
There’s a new, still-under-development, Golang-based botnet called Kraken with a level of brawn that belies its youth: It’s using the SmokeLoader malware loader to spread like wildfire and is already raking in a tidy USD $3,000/month for its operators, researchers report.
Though its name may sound familiar, Kraken has little to do with the 2008 botnet of the same name, wrote ZeroFox threat researcher Stephan Simon in a Wednesday post.
Using SmokeLoader to install yet more malicious software on targeted machines, Kraken is picking up hundreds of new bots each time a new command-and-control (C2) server is deployed, according to Simon’s post.
ZeroFox came upon the previously unknown botnet, which was still under active development, in late October 2021. Even though it was still being developed, it already had the ability to siphon sensitive data from Windows hosts, being able to to download and execute secondary payloads, run shell commands, and take screenshots of the victim’s system, ZeroFox said.
Simple, But Multi-Tentacled
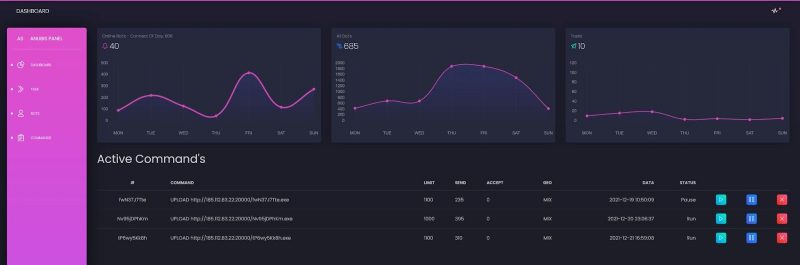
ZeroFox shared a screen capture of the initial version of Kraken’s panel – shown below, the C2 was named “Kraken Panel” – that’s lean in features. It offered basic statistics, links to download payloads, an option to upload new payloads, and a way to interact with a specific number of bots.
“This version did not appear to allow the operator(s) to choose which victims to interact with,” Simon noted.
But the current version of Kraken’s C2 panel, shown below, has been completely redesigned and renamed as Anubis. “The Anubis Panel provides far more information to the operator(s) than the original Kraken Panel,” according to Simon. “In addition to the previously provided statistics, it is now possible to view command history and information about the victim.”
Grabbing Cryptocurrency
Kraken’s author has been tinkering, adding and deleting capabilities. At this point, Kraken can maintain persistence, collect information about the host, download and execute files, run shell commands, take screenshots, and steal various cryptocurrency wallets, including Zcash, Armory, Atomic, Bytecoin, Electrum, Ethereum, Exodus, Guarda and Jaxx Liberty.
Later iterations have gotten yet more replete, with the author having added selective choosing of targets for commands (individually or by group, as opposed to the earlier version having only allowed a bot operator to choose how many victims they’re targeting), task and command history, task ID, command being sent, how many victims the command should be sent to, the targeted geolocation, and a timestamp of when the task was initiated.
At first, from October to December 2021, the RedLine infostealer was inflicted on victims’ machines every time Kraken struck. RedLine, an increasingly prevalent infostealer, swipes data from browsers, such as saved credentials, autocomplete data and credit card information.
The malware has since spread its tentacles, though, both in terms of adding other infostealers to the mix and making its operators a boatload of dough. “As the operator(s) behind Kraken continued to expand and gather more victims, ZeroFox began observing other generic information stealers and cryptocurrency miners being deployed,” according to Simon’s writeup.
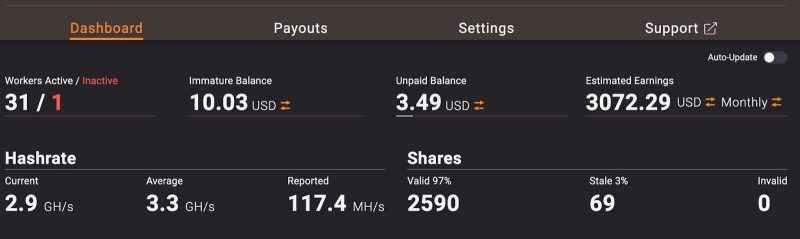
As of Wednesday, the botnet was pulling in around USD $3,000 every month, as shown in the screen capture below from Ethermine.
What does the operator plan to do with the new bot and all the data its infostealers are sucking up? It’s unknown at this point, ZeroFox researchers concluded: “It is currently unknown what the operator intends to do with the stolen credentials that have been collected or what the end goal is for creating this new botnet.”
Steering Clear
ZeroFox passed on these recommendations to keep Kraken from tangling up your systems:
Ensure antivirus and intrusion detection software is up to date with all patches and rule sets. Enable two-factor authentication for all organizational accounts to help mitigate phishing and credential stuffing attacks. Maintain regularly scheduled backup routines, including off-site storage and integrity checks. Avoid opening unsolicited attachments and never click suspicious links. Log and monitor all administrative actions as much as possible. Alert on any suspicious activity. Review network logs for potential signs of compromise and data egress.Join Threatpost on Wed. Feb 23 at 2 PM ET for a LIVE roundtable discussion “The Secret to Keeping Secrets,” sponsored by Keeper Security, focused on how to locate and lock down your organization’s most sensitive data. Zane Bond with Keeper Security will join Threatpost’s Becky Bracken to offer concrete steps to protect your organization’s critical information in the cloud, in transit and in storage. REGISTER NOW and please Tweet us your questions ahead of time @Threatpost so they can be included in the discussion.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·