BOOK THIS SPACE FOR AD
ARTICLE ADGhostwriter is one of 3 campaigns using war-themed attacks, with cyber-fire coming in from government-backed actors in China, Iran, North Korea & Russia.
Ghostwriter – a threat actor previously linked with the Belarusian Ministry of Defense – has glommed onto the recently disclosed, nearly invisible “Browser-in-the-Browser” (BitB) credential-phishing technique in order to continue its ongoing exploitation of the war in Ukraine.
In a Wednesday post, Google’s Threat Analysis Group (TAG) said that they’d already spotted BitB being used by multiple government-backed actors prior to the media turning a laser eye on BitB earlier this month. The fresh attention was triggered by a penetration tester and security researcher – who goes by the handle mr.d0x – who posted a description of BitB.
Ghostwriter actors quickly picked up on BitB, combining it with another of the advanced persistent threat’s (APT’s) phishing techniques: namely, hosting credential-phishing landing pages on compromised sites.
BitB
The newly disclosed credential-phishing method of BitB takes advantage of third-party single sign-on (SSO) options embedded on websites that issue popup windows for authentication, such as “Sign in with Google,” Facebook, Apple or Microsoft.
These days, SSO popups are a routine way to authenticate when you sign in.
But according to mr.d0x’s post, completely fabricating a malicious version of a popup window is a snap: It’s “quite simple” using basic HTML/CSS, the researcher said a few weeks ago. The concocted popups simulate a browser window within the browser, spoofing a legitimate domain and making it possible to stage convincing phishing attacks.
“Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and [it’s] basically indistinguishable,” mr.d0x wrote at the time.
JavaScript can make the window appear on a link, button click or page loading screen. As well, libraries – such as the popular JQuery JavaScript library – can make the window appear visually appealing.
BitB Credential Phishing on Compromised Sites
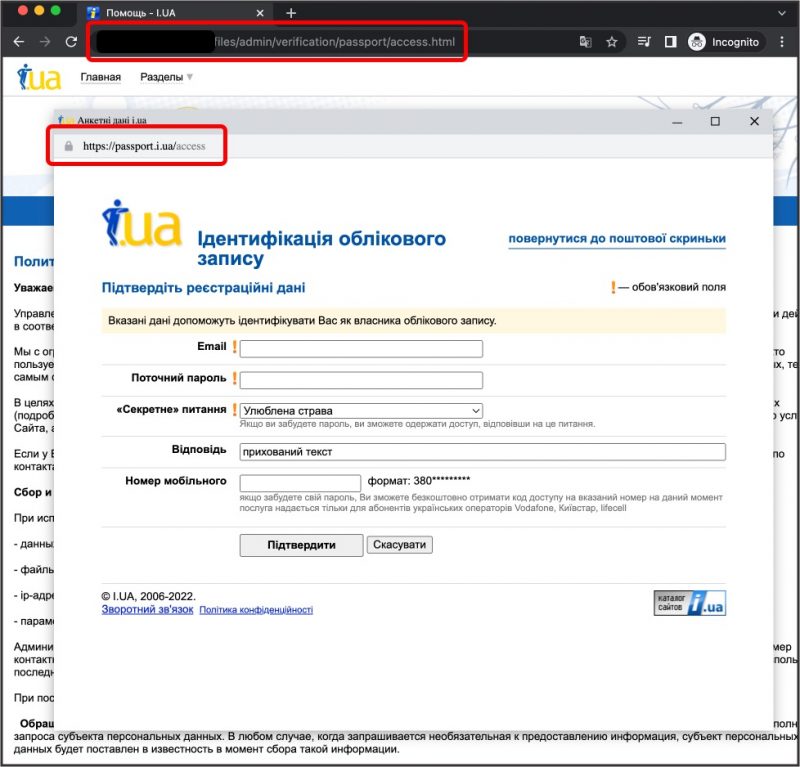
In Wednesday’s post, TAG gave an example, shown below, of how Ghostwriter has taken to hosting credential phishing landing pages on compromised sites:
The BitB technique shown above entails drawing a login page that appears to be on the passport.i.ua domain, over the page hosted on the compromised site. “Once a user provides credentials in the dialog, they are posted to an attacker controlled domain,” TAG researchers said.
TAG has recently observed Ghostwriter credential-phishing on these domains:
login-verification[.]top login-verify[.]top ua-login[.]top secure-ua[.]space secure-ua[.]topOther Campaigns Launched by Government-Backed Actors in China, Iran, North Korea & Russia
Since early March, Ghostwriter’s use of BitB is only one of a trio of cyber aggressions that TAG has been tracking with regards to Russia’s invasion of Ukraine.
The use of the war as a lure in phishing and malware campaigns has continued to grow throughout the month, TAG said, with associated cyber-assaults coming in from government-backed actors from China, Iran, North Korea and Russia, as well as from various unattributed groups, according to TAG’s Wednesday post.
Actors “have used various Ukraine war-related themes in an effort to get targets to open malicious emails or click malicious links,” TAG said.
Curious Gorge
Besides Ghostwriter’s BitB campaigns, TAG has spotted a group it’s calling Curious Gorge that it attributes to China’s PLA SSF conducting campaigns against government and military organizations in Ukraine, Russia, Kazakhstan and Mongolia.
“While this activity largely does not impact Google products, we remain engaged and are providing notifications to victim organizations,” TAG advised.
Below is a list of IPs used in Curious Gorge campaigns that TAG has recently observed:
5.188.108[.]119 91.216.190[.]58 103.27.186[.]23 114.249.31[.]171 45.154.12[.]167COLDRIVER
Finally, TAG has also observed COLDRIVER – a Russia-based threat actor, sometimes referred to as Calisto – that has launched credential-phishing campaigns targeting several United States-based NGOs and think tanks, the military of a Balkans country, and a Ukraine based defense contractor.
Now, however, for the first time, COLDRIVER is targeting the military of multiple Eastern European countries and a NATO Centre of Excellence, TAG reported.
Google doesn’t know how successful these campaigns have been, given that they were issued from newly created Gmail accounts to non-Google accounts. At any rate, Google hasn’t see any Gmail accounts successfully compromised because of these campaigns, TAG said.
Recently observed COLDRIVER credential phishing domains:
protect-link[.]online drive-share[.]live protection-office[.]live proton-viewer[.]comMoving to the cloud? Discover emerging cloud-security threats along with solid advice for how to defend your assets with our FREE downloadable eBook, “Cloud Security: The Forecast for 2022.” We explore organizations’ top risks and challenges, best practices for defense, and advice for security success in such a dynamic computing environment, including handy checklists.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·