BOOK THIS SPACE FOR AD
ARTICLE ADStolen zero-days are fueling ‘out-of-control’ supply chain attack problem, warns former cyber-spy
 Matt Tait delivered the Black Hat USA 2021 keynote
Matt Tait delivered the Black Hat USA 2021 keynote
Software supply chain attacks are growing at an alarming pace, in a stark development that up-ends the delicate balance cybersecurity relies on, infosec luminary Matt Tait told delegates at the Black Hat USA conference today (August 4).
During his keynote, Tait (@pwnallthethings) warned that supply chain attacks pose a much greater risk than normal data breaches. The frequency of such events over the last year or so – already high – is likely to increase.
Tait cited examples of software supply chain attacks including the Colonial Pipeline breach, the Kaseya ransomware attack, Nobellium (Microsoft Exchange), SolarWinds, and the NSO Pegasus revelations. This can have a "waterfall effect" where a successful supply chain attack can become the entry point to attacking a third party software developer and its customers.
“Offense has taken the gloves off,” according to Tait, who argued that the increase in software supply chain attacks is being fuelled by a massive growth in the exploitation of zero-day vulnerabilities that is “off the charts”.
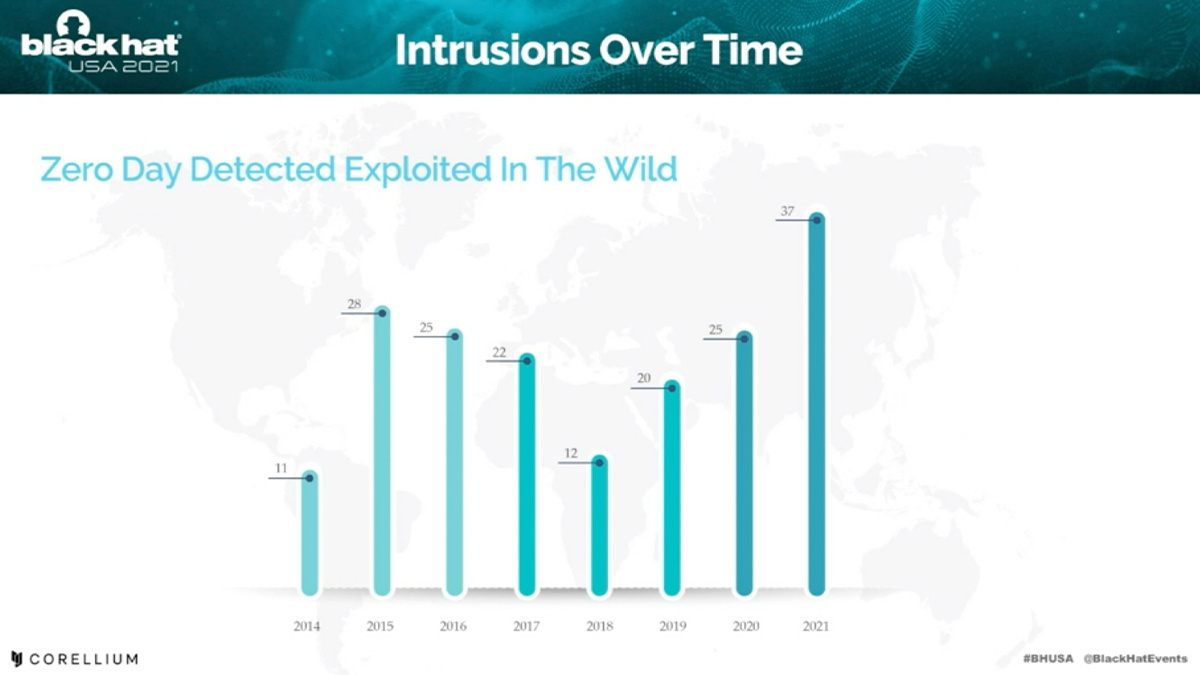 The number of zero-days detected in the wild has rocketed in 2021
The number of zero-days detected in the wild has rocketed in 2021
Money to burn
Mass exploitation with zero-days has historically been infrequent because ‘burning’ through esoteric flaws as a result of their eventual discovery is both financially costly and a big problem if attacks are attributed and C2 infrastructure needs to be taken down and rebuilt.
Tait – whose career includes stints at GCHQ and Google Project Zero – argued that use of stolen zero-days is driving the increase in software supply chain attacks.
Stolen zero-day are changing the economics of mass exploitation. That means anyone who makes or handles zero-day code needs to keep them secure, according to Tait. “You are a target,” he warned his fellow security researchers.
Bug bounties and exploit chains
To help secure the software supply chain, the security expert argued that bug bounty programs need to be rethought so that vulnerabilities are disclosed and patched as soon as possible.
As it stands, according to Tait, researchers are somewhat incentivized to ‘sit on’ high-impact vulnerabilities in the hope that they may develop this into a ‘full chain’ exploits. While these chains bring with them maximum bounty payouts, every day the same zero-day remains open for discovery by another third party.
Strongest links
Fixing the problem of supply chain attacks, whatever its root cause, is not going to be easy.
Supply chain infections can only be fixed by platform vendors, Tait concluded, who argued that government intervention or regulation will do little to address the problem.
The security expert concluded his well-received presentation by citing Certificate Transparency as a promising example of platform vendors tackling a particular issue.
The Daily Swig team will be reporting live from Black Hat and DEF CON all this week. Check back for more of the latest web security research and open source hacking tools.
RELATED Four-fold increase in software supply chain attacks predicted in 2021 – report
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·