BOOK THIS SPACE FOR AD
ARTICLE ADHours before the Superbowl and two days after the FBI warned about the ransomware gang, BlackByte leaked what are purportedly the NFL team’s files.
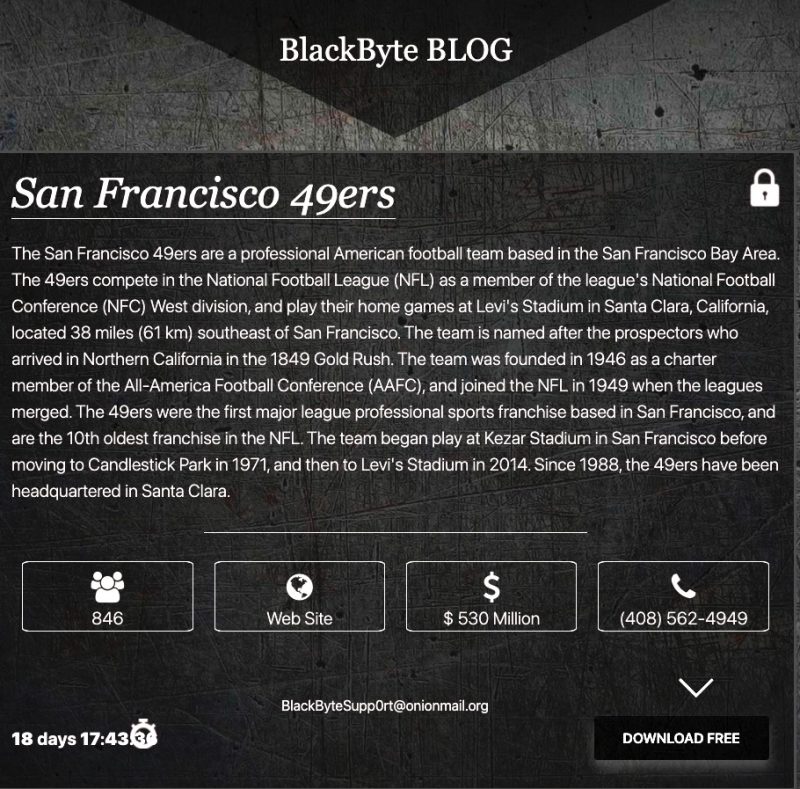
The San Francisco 49ers were recently kneecapped by a BlackByte ransomware attack that temporarily discombobulated the NFL team’s corporate IT network on the Big Buffalo Wing-Snarfing Day itself: Superbowl Sunday.
BlackByte – a ransomware-as-a-service (RaaS) gang that leases its ransomware to affiliates who cut it in on a share of ransom profits – claimed responsibility for the attack by leaking files purportedly stolen in the cyber assault.
The 49ers confirmed the attack to Threatpost on Monday. The team’s statement:
“We recently became aware of a network security incident that resulted in temporary disruption to certain systems on our corporate IT network. Upon learning of the incident, we immediately initiated an investigation and took steps to contain the incident.”
The 49ers brought in third-party cybersecurity firms to assist and notified law enforcement. The team was still investigating as of Monday, but so far, it looks like the intrusion was limited to its corporate IT network and didn’t affect ticket systems or systems at the team’s home base, Levi’s Stadium..
“To date, we have no indication that this incident involves systems outside of our corporate network, such as those connected to Levi’s Stadium operations or ticket holders,” its statement said. “As the investigation continues, we are working diligently to restore involved systems as quickly and as safely as possible.”
Joseph Carson, chief security scientist and advisory CISO at provider of privileged access management (PAM) solutions provider Delinea, suggested to Threatpost that it’s likely that an affiliate hacked the 49ers, as opposed to the authors behind the ransomware, given that BlackByte is an RaaS.
BlackByte recently posted some files purportedly stolen from the team on a dark web site in a file marked “2020 Invoices.” The gang hasn’t made its ransom demands public. Nor has the group specified how much data it stole or encrypted.
Carson said that the Superbowl timing makes this one a classic case of cyber pests milking a major event: the kind of situation where they can get unsuspecting victims “to click on links, download and execute malicious software or give over their credentials, thinking they are accessing a legitimate internet services, resulting in cybercriminals gaining initial access to networks and services. Once access is compromised, it is only a matter of time before ransomware is deployed.”
Attack Follows Fast on Heels of Feds’ Warning
The attack on the 49ers came two days after the FBI and Secret Service jointly announced (PDF) that BlackByte ransomware has breached the networks of at least three organizations from U.S. critical infrastructure sectors in the last three months.
“As of November 2021, BlackByte ransomware had compromised multiple US and foreign businesses, including entities in at least three US critical infrastructure sectors (government facilities, financial, and food & agriculture),” the Feds said in a TLP:WHITE joint cybersecurity advisory released on Friday.
BlackByte’s Back
The gang emerged in July 2021, when it started preying on organizations by exploiting known Microsoft Exchange vulnerabilities – such as ProxyShell – to claw its way into environments.
It worked for a while: BlackByte scored wins against manufacturing, healthcare and construction industries in the United States, Europe and Australia. But the gang hit a wall when, months later, Trustwave released a free decryption tool that allowed BlackByte victims to unsnarl their files.
As Trustwave said in October, the security firm found BlackByte to be a ransomware weirdo, for these reasons:
Same as other notorious ransomware variants like REvil, BlackByte also avoids systems with Russian and ex-USSR languages. It has a worm functionality similar to RYUK ransomware. It creates a wake-on-LAN magic packet and sends it to the target host – making sure they are alive when infecting them. The author hosted the encryption key in a remote HTTP server and in a hidden file with .PNG extension. The author lets the program crash if it fails to download the encryption key. The RSA public key embedded in the body is only used once, to encrypt the raw key to display in the ransom note – that’s it. The ransomware uses only one symmetric key to encrypt the files.As far as BlackByte’s auction site for selling victims’ data goes, it’s apparently a house of mirrors. While the site claims to contain exfiltrated data from victims, the ransomware itself doesn’t have the ability to exfiltrate data, Trustwave’s Rodel Mendrez and Lloyd Macrohon wrote. “This claim is probably designed to scare their victims into complying,” they said.
As the Trustwave analysts pointed out in October, the group uses simplistic encryption techniques, using just one symmetric key to encrypt files in AES, as opposed to using unique keys for each session.
But despite the setback of Trustwave’s decryptor and what experts think of as its simplistic encryption, BlackByte is clearly doing just fine, given the FBI/Secret Service alert on Friday.
Matthew Warner, CTO and co-founder at Blumira, a provider of automated threat detection and response technology, called BlackByte a “growing ransomware operator” that’s benefited from following successful patterns implemented by previous groups.
“Similar to Conti ransomware, BlackByte has been identified using Exchange vulnerabilities such as ProxyShell to gain a foothold in environments,” Warner observed to Threatpost on Monday. “Additionally, BlackByte utilizes well-proven tactics such as Powershell exploitation of obfuscated base64 content to perform all encryption on hosts once exploited.
“In the end, BlackByte is by no means more sophisticated than other actors in the ransomware universe but rather are the next up-and-coming player to exploit organizations and their data,” Warner added via email.
Critical Infrastructure
Erich Kron, security awareness advocate at KnowBe4, focused on the FBI warning about BlackByte’s success in penetrating the critical infrastructure sector: a sector that’s been “plagued” by ransomware attacks, he said.
“The criticality of the systems makes quick recovery vital, which increases the likelihood that the victims will pay the ransom,” Kron said in a Monday email. “This same criticality also makes law enforcement attention much more likely. However, given the low success rate of law enforcement busts, this is often a chance the groups are willing to take.”
Kron blamed limited budgets, aging equipment and shortages in cybersecurity staff for making critical infrastructure and many government entities especially vulnerable to ransomware attacks.
“These groups must focus on the top attack vectors used in ransomware attacks, usually email phishing and attacks on remote access portals,” he advised. “Training the users to spot and report phishing emails and improving the organizational security culture, along with ensuring remote access portals are monitored for brute force attacks and that credentials being used have Multi-Factor Authentication (MFA) enabled are some top ways to counter these threats.”
Join Threatpost on Wed. Feb 23 at 2 PM ET for a LIVE roundtable discussion “The Secret to Keeping Secrets,” sponsored by Keeper Security, focused on how to locate and lock down your organization’s most sensitive data. Zane Bond with Keeper Security will join Threatpost’s Becky Bracken to offer concrete steps to protect your organization’s critical information in the cloud, in transit and in storage. REGISTER NOW and please Tweet us your questions ahead of time @Threatpost so they can be included in the discussion.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·