BOOK THIS SPACE FOR AD
ARTICLE AD
Hello everyone I wanted to share one of my finding related to Blind SSRF on a private program on HackerOne for which they paid me $400.

Summary :
Blind SSRF vulnerabilities occur when an application is making a request to a back-end server due to some reasons but the response is not shown on the front-end.
If we talk about the impact, it is low than that of normal SSRF because of their one way nature. They can be exploited to retrieve sensitive information from back-end systems and in a rare case it can be exploited to achieve remote code execution.
For this finding I used an extension of BurpSuite known as Collaborator Everywhere and I also used Collaborator Client. So I’ll be discussing both of them here.
How to add Collaborator Extension in your BurpSuite ?
Start your BurpSuiteGo to extender and click on BApp StoreFind the extension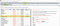
4. Install it to your BurpSuite
One of the easiest way to find Blind SSRF vulnerability is the out-of-band technique which means to use an external server to find blind vulnerabilities. That external server should be under your control which can be used to monitor network interactions with the system.
If you don’t want to setup your own server then you can use Burp Collaborator.
How I found this vulnerability ?
I went to my target website and it was using an API for interaction with the server, so I thought of using the extension Collaborator EverywhereI started BurpSuite, went to Extender and clicked on Extensions. Then I selected the installed extension (Collaborator Everywhere).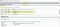
3. Then I changed the browser proxy to manual
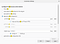
4. I refreshed the page and I went to BurpSuite > Target > Site Map
5. I right clicked on my target and chose the option Add to scope
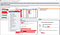
You’ll get this pop-up, select Yes

6. Now just visit the site properly, means open your profile or you can go to your settings etc.
In my case I was having following options on dashboard to visit.
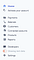
So every request will be captured by BurpSuite (because of Add to Scope) and evaluated by Collaborator Everywhere extension.
7. After sometime I checked the Site map and found this issues
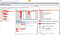
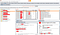
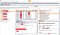
8. So I knew that it is vulnerable to Blind SSRF
9. Now I wanted to confirm it again so I used Burp Collaborator, you’ll find it in the BurpSuite it comes pre-installed
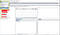
10. Click on Copy to clipboard for copying the payload
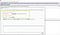
11. I sent the request to repeater and replaced the referrer header URL with the copied payload of Burp Collaborator client
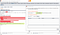
12. Now I clicked on go and waited for 5 to 10 seconds, then I clicked on Poll now and got the response from the server
NOTE : You’ll find different payload in last 3rd image and in last 2nd image, it is because I reproduced the issue 2 times nothing else, so different payload for each time.
Important Points :
When testing for Blind SSRF it is common that you’ll find a DNS lookup for the given Burp Collaborator domain, but no HTTP request. This happens because the application attempted to make an HTTP request to domain, which caused initial DNS lookup but the actual HTTP request was blocked by the network-level filtering.If you find only the DNS lookup or DNS query then it is not a vulnerability, it is mandatory to have the HTTP response which will make it a valid vulnerability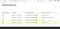
You can see that it is considered as P5 according to bugcrowd’s VRT.

.png)
 4 years ago
317
4 years ago
317 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·