The operators behind BRATA have once again added more capabilities to the Android mobile malware in an attempt to make their attacks against financial apps more stealthy.
"In fact, the modus operandi now fits into an Advanced Persistent Threat (APT) activity pattern," Italian cybersecurity firm Cleafy said in a report last week. "This term is used to describe an attack campaign in which criminals establish a long-term presence on a targeted network to steal sensitive information."
An acronym for "Brazilian Remote Access Tool Android," BRATA was first detected in the wild in Brazil in late 2018, before making its first appearance in Europe last April, while masquerading as antivirus software and other common productivity tools to trick users into downloading them.
The change in the attack pattern, which scaled new highs in early April 2022, involves tailoring the malware to strike a specific financial institution at a time, switching to a different bank only after the victim begins implementing countermeasures against the threat.
Also incorporated in the rogue apps are new features that enable it to impersonate the login page of the financial institution to harvest credentials, access SMS messages, and sideload a second-stage payload ("unrar.jar") from a remote server to log events on the compromised device.
"The combination of the phishing page with the possibility to receive and read the victim's sms could be used to perform a complete Account Takeover (ATO) attack," the researchers said.
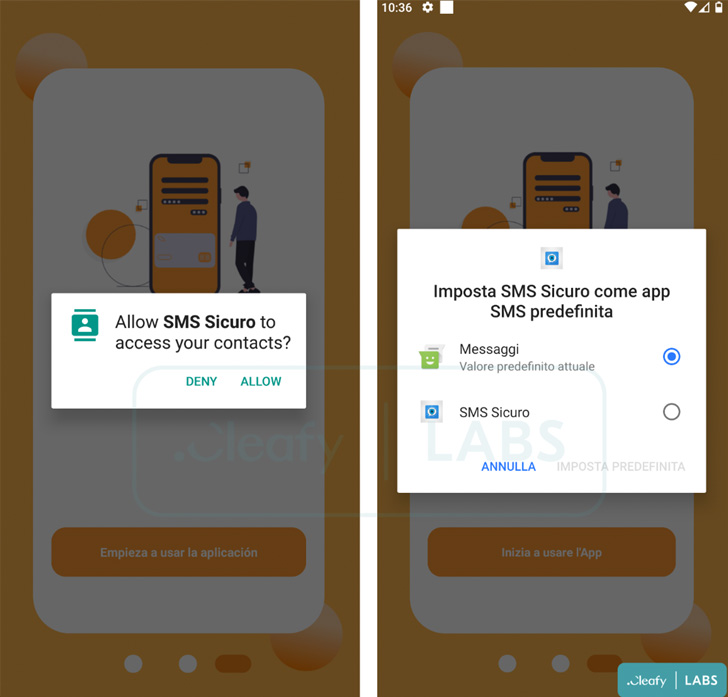
Additionally, Cleafy said it found a separate Android app package sample ("SMSAppSicura.apk") that used the same command-and-control (C2) infrastructure as BRATA to siphon SMS messages, indicating that the threat actors are testing out different methods to expand their reach.
The SMS stealer app is said to be specifically singling out users in the U.K., Italy, and Spain, its goal being able to intercept and exfiltrate all incoming messages related to one-time passwords sent by banks.
"The first campaigns of malware were distributed through fake antivirus or other common apps, while during the campaigns the malware is taking the turn of an APT attack against the customer of a specific Italian bank," the researchers said.
"They usually focus on delivering malicious applications targeted to a specific bank for a couple of months, and then moving to another target."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
156
2 years ago
156 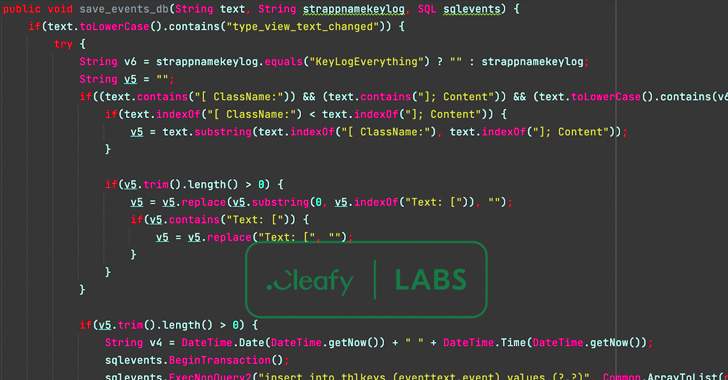

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·