BOOK THIS SPACE FOR AD
ARTICLE AD
A new phishing campaign targets Counter-Strike 2 players utilizing Browser-in-the-Browser (BitB) attacks that display a realistic window that mimics Steam's login page.
The attackers impersonate the Ukrainian e-sports team Navi to bait devoted fans and add legitimacy to the phishing page by using a recognizable brand.
The campaign uses the Browser-in-the-Browser (BitB) phishing technique created by cybersecurity researcher mr. dox in March 2022. This phishing framework allows threat actors to create realistic-looking popup windows with custom address URLs and titles within another browser window.
Basically, this phishing technique creates fake browser windows within real browser windows (Browser in the Browser) to create login pages or other realistic forms to steal users' credentials or one-time MFA passcodes (OTP).
Threat actors adopted Browser-in-the-Browser attacks later that year in large-scale attacks attempting to steal Steam accounts.
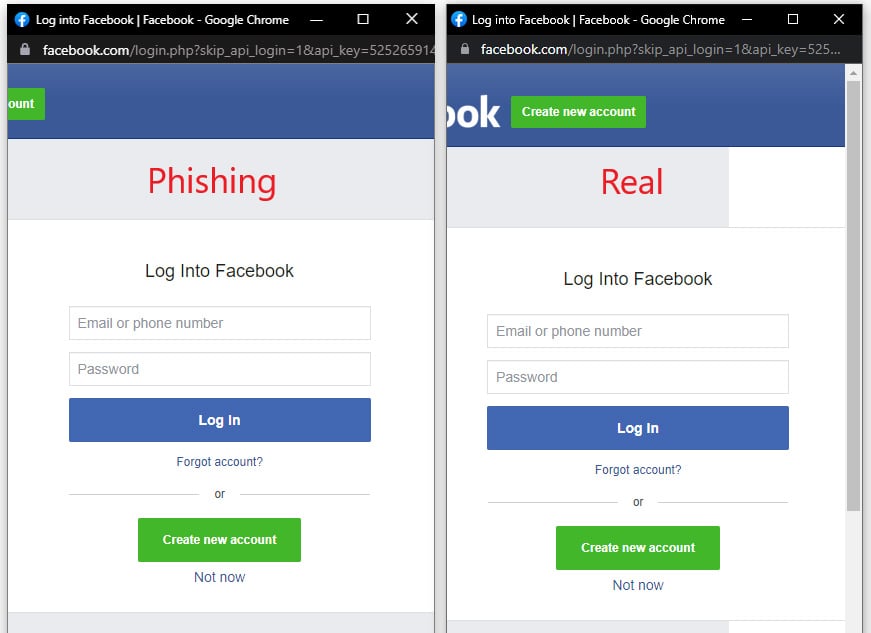 Facebook phishing page using the BitB framework
Facebook phishing page using the BitB frameworkSource: mr.d0x
Targeting Steam accounts
In a campaign observed by Silent Push researchers, threat actors are using YouTube videos and potentially other promotion channels to take prospective victims to phishing sites. These sites all use the same IP address, indicating that a single attacker or group runs the campaign.
These sites promise a free CS2 loot case with new skins.
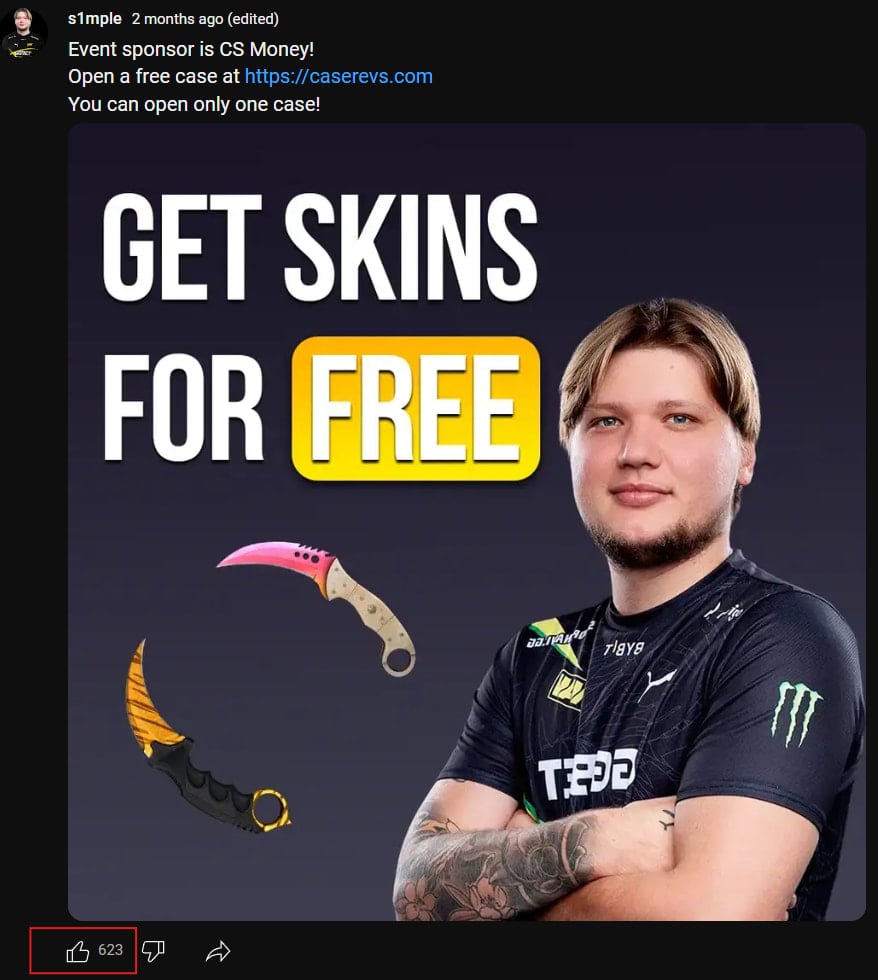 Promotional message on YouTube
Promotional message on YouTubeSource: Silent Push
The malicious websites promising the CS2 in-game items are:
caserevs[.]com caseneiv[.]com casenaps[.]com caseners[.]com caseneiv[.]com simplegive[.]cn caseneus[.]cfdTo claim the gift, users are told to log in to their Steam account using what appears to be a Steam login popup. However, the popup window that opens isn't actually real.
Instead, the attackers are using the BitB technique to show a fake login window mimicking Steam's official URL and interface within the active window, making it appear like a popup, even though it's not.
These fake windows aren't resizable and cannot be dragged outside the active window (like a normal popup), but users who don't attempt to interact with them in these ways may not suspect foul play.
.jpg) Fake Steam login popup on the phishing page
Fake Steam login popup on the phishing pageSource: Silent Push
These attacks aim to steal Steam accounts and resell them on specialized grey markets for tens, sometimes hundreds of thousands, depending on the game collection size and in-game items held by the account.
![Steam accounts for sale on playerauctions[.]com](https://www.bleepstatic.com/images/news/u/1220909/2025/March/accounts.jpg) Steam accounts for sale on playerauctions[.]com
Steam accounts for sale on playerauctions[.]comSource: Silent Push
Despite its age, Counter-Strike 2 remains a very popular game, especially in the e-sports community, and threat actors have been taking advantage of renowned teams and pro-level competition to phish Steam accounts.
Last month, Bitdefender reported about a large-scale campaign that used fake YouTube CS2 livestreams with QR codes taking people to malicious websites promising in-game items and cryptocurrency giveaways.
Users who followed the links to phishing sites were asked to enter their Steam account credentials or connect their cryptocurrency wallets, only to see them hijacked/emptied.
To strengthen Steam account security, activate multi-factor authentication, enable 'Steam Guard Mobile Authenticator,' and regularly review login activity for suspicious sign-ins.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·