BOOK THIS SPACE FOR AD
ARTICLE AD
Hello people, it’s me again. I apologize for being late about the second part. I had some examinations going on and have been busy for the past 3 days.
So, here I am and let’s dive right in…
I see, we covered up to Session Management in the previous article, we will be continuing from there.
9. Authorization
People would often confuse security controls such as Authentication and Authorization.
Authentication is the one which verifies user’s identity, like the apps everyone uses such as “Microsoft Authenticator” and other 2 factory authorizations.
Authorization is more like giving access to a third party. Often, you would observe when you sign-up for new services and the third party service or app will be asking access for their respective google drive permissions.
Given below are some of the test cases:

10. Data Validation
As the name suggests, Data Validation is checking whether the information entered is not manipulated; whether it may be in a database, servers or on personal computers.

11. Denial-Of-Service(DOS)
I think most of you are aware of DOS attacks. Simply put, it’s about exhausting the system resources leading to shutdown a network or a system.
These are some of the things to test:

12. Business Logic
These are the custom rules or algorithms that carry or exchange the information between a business logic layer or database and user interface.
You will probably come across different terms like database management softwares, different workflows involved, triggers, modifications check, and participant controls.
Well, here’s the checklist:

13. Crytographic Failures
The process of designing new algorithms in order to practice and implement secure communication protocols, thus protecting information in the process is termed to be cryptography.
But very often, these algorithms may retire. For example, In 2018, NIST officially retired 3DES. Google it and you can find more examples.
The checklist is mentioned below:

14. Risky Functionalities
Risky functionalities is about testing file uploads, bypassing administrator accounts, and testing payment methods.
It’s divided into two parts. I made a checklist for testing of file uploads and checking of test cases while manipulating card payment information.
Here goes the 1st one:

Second Checklist:

15. Miscellaneous
Here goes the list:
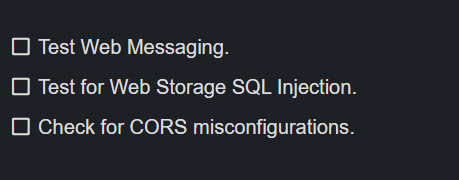
I know it’s a small list but I will work on expanding it.
Seems like this is it. As always, see you on the flip side. If you want me to write about particular topics, please do mention it in the comments.
.png)
 2 years ago
102
2 years ago
102 












 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·