BOOK THIS SPACE FOR AD
ARTICLE ADAutomatically add headers to all Burp requests to bypass basic WAF rules

Some web applications implement IP-based protection rules that restrict users from accessing particular pages of an application like an admin page if their IP addresses are not in the allowed list. These rules are used as an access control mechanism.
It relies on having a proxy between the client and the server for forwarding requests. The Proxy forwards the client’s IP to the server; if it allowed or whitelisted list, the server will respond with the requested page; otherwise, it will block the request.
The Proxy does that by adding an X-Forwarded-For header that contains the client’s IP address to the request before sending it to the server. The application then checks the X-Forwarded-For header to determine whether the IP address of the client is in the allowed list.
📌 The X-Forwarded header accepts two directives a client IP and proxy IP. It is possible to include multiple proxy IPs to send the requests; the traffic will bounce through the IPs successively before reaching the server.
📎 Syntax: X-Forwarded-For: <client>,<proxy1>,<proxy2>,<proxy3>
The attackers can take advantage of this and test the restriction rules by spoofing a different IP that they know is allowed by the application, like localhost address 127.0.0.1. Tricking the application into thinking the requests comes from a trusted source, even though the original requests are coming from a different blocked IP.

Since it is a pain to modify requests manually in attempts to bypass these WAF restriction rules, Burp can help automatically insert the required headers into each request sent to the application.🌋
There are 2 methods to achieve our goal through Burp Suite, either through the match and replace rules, which actually what I use all the time before discovering the Bypass WAF extension.
I was unaware of the extension before working on the Control machine on HTB, and I came across the extension when researching for better ways to automate forwarding requests.
Even though I liked using the extension, I am going to include both methods for reference 😃 .
Let’s begin !!
1- Navigate to the Proxy tab and click on Options. Scroll down to the Match and Replace section and click Add.

2- Specify the details needed for the matched Rule. We start first with specifying the Type of Rule; in our case, it is a Request Header since we want Burp to insert the modified header into all client requests.
Next, in the Match field, leave it blank to match all requests.
In the Replace field, we will enter the X-Forwarded-For header with the IP address we want to send requests from.
📍 Adding a comment is optional but helpful if you are using multiple rules at the time.
When done, click Ok to save the rule.

3- Check the Enabled box to enable the new Rule.

Now, we have the Rule configured, let’s test it out. Turn Foxy Proxy On or add the proxy setting to the browser, and refresh the page.

If we intercept the request with Proxy, we see Burp added the X-forwarded header in all the sent requests.

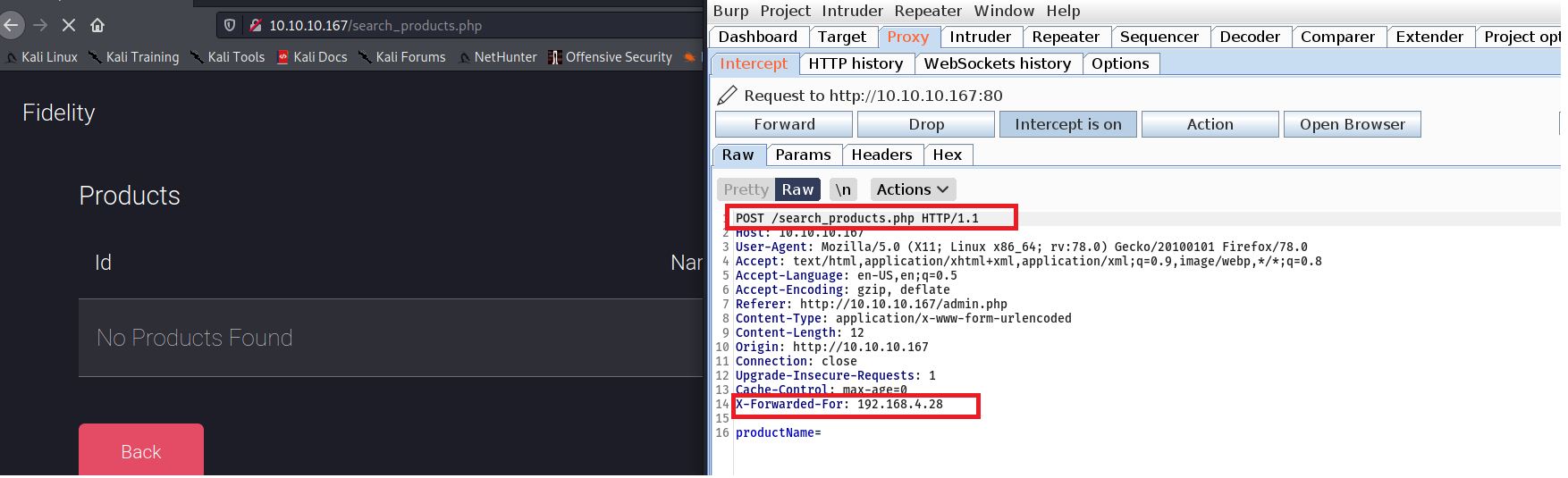
The extension can be installed and configured to send X-forwarded headers automatically each time you navigate the application.
1- Go to the Extender tab and click Burp Store BApp Store. Scroll down to the right pane and click on the Install Button.


When the extension is installed, it will be added in the Extensions tab, and a new tab will be added in Burp Suite Tabs.
As we see below, the Bypass WAF extension tab is added to Burp Tabs.

💡Remove Extension: You can remove an extension by going to the Extensions Tab and click on Remove.
2- Next, we need to add a session handling rule to make Burp perform the required actions when making the HTTP requests.
Go to Project options and click on Sessions, then click Add.

Insert the name of the Rule in the Rule Description and the action needed in Rule Actions. In our case, we want to Invoke Burp Extension that will allow us to use the Bypass WAF extension.

Click Ok and choose the Bypass WAF extension. Then click Ok.

4- In the Scope tab, check the Proxy box to enable it.
For the URL scope, we can either choose to Include all URLs or Use a Targeted scope “User suite scope [defined in Target tab].

5- Next, we configure the extension, click on the Bypass WAF, add the IP address in the Header field and click on Set Configuration to enable the bypass configuration.

6- Refresh the page, and test the extension.

Great!! The extension works. The downside is when intercepting the requests, I don’t see the source IP headers are added like with the Match & Replace rule.

With a bit of research, I found that I can install the Flow extension to monitor the requests I send to the proxy and see how the Bypass WAF injects the x-forwarded header.
7- Go back to the BApp Store and install Flow.

In the extension tab, make sure the Flow extension is added under the Bypass WAF extension. (🔔 order matters when monitoring requests).

8- Now refresh the page and go to the Flow tab. We can see the headers Bypass WAF injects to the requests we send to the server.

That’s all for today, Thanks reading.
.png)
 3 years ago
309
3 years ago
309 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·