BOOK THIS SPACE FOR AD
ARTICLE AD
Hackers are increasingly moving towards hybrid forms of phishing attacks that combine email and voice social engineering calls as a way to breach corporate networks for ransomware and data extortion attacks.
According to Agari's Q2 2022 cyber-intelligence report, phishing volumes have only increased by 6% compared to Q1 2022. However, the use of 'hybrid vishing' is seeing a massive 625% growth.
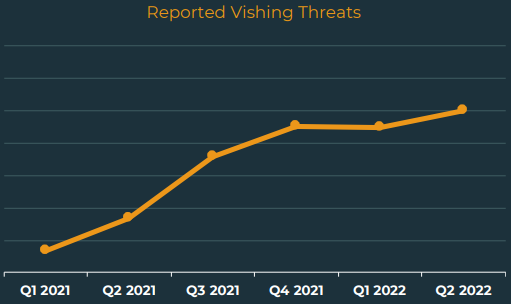 The gradual growth of vishing since Q1 2021 (Agari)
The gradual growth of vishing since Q1 2021 (Agari)Vishing, "voice phishing," involves some form of a phone call to perform social engineering on the victim.
Its hybrid form, called "callback phishing," also includes an email before the call, typically presenting the victim with a fake subscription/invoice notice.
The recipient is advised to call on the provided phone number to resolve any issues with the charge, but instead of a real customer support agent, the call is answered by phishing actors.
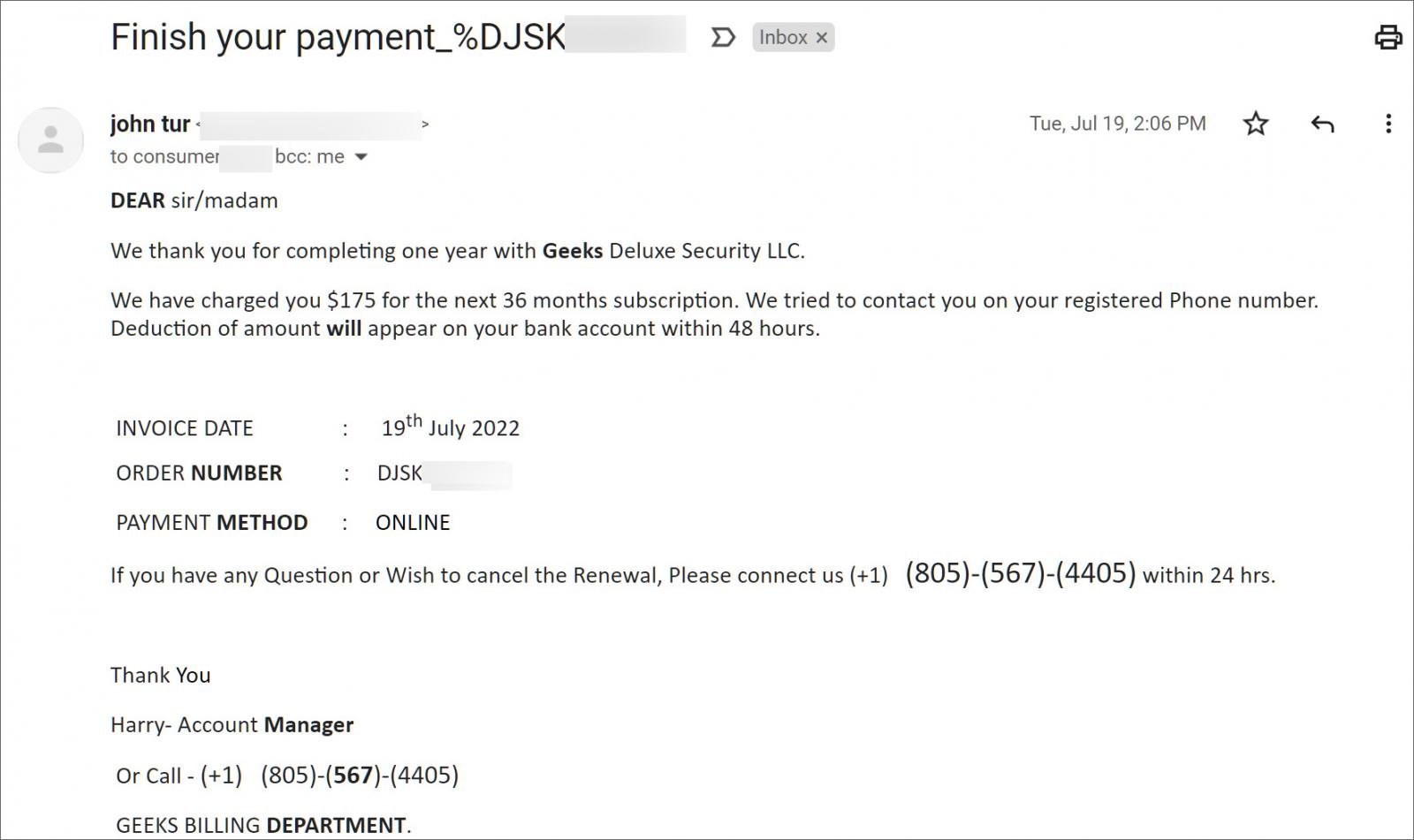 Example of a callback phishing email
Example of a callback phishing emailSource: BleepingComputer
The scammers then offer to resolve the presented problem by tricking the victim into disclosing sensitive information or installing remote desktop tools on their system. The threat actors then connect to the victim's device remotely to install further backdoors or spread to other machines.
These callback phishing attacks were first introduced by the 'BazarCall/BazaCall' campaigns that appeared in March 2021 to gain initial access to corporate networks for ransomware attacks.
The attacks work so well that multiple ransomware and extortion gangs, such as Quantum, Zeon, and Silent Ransom Group, have adopted the same technique today to gain initial network access through an unsuspecting employee.
"Hybrid Vishing attacks reached a six-quarter high in Q2, increasing 625% from Q1 2021. This threat type also contributed to 24.6% of the overall share of Response-Based threats," details the Agari report.
"While this is the second quarter hybrid vishing attacks have declined in share due to the overall increase of response-based threats, vishing volume has steadily increased in count over the course of the year."
Emotet surged and then died again
The Emotet botnet has a habit of surging and then taking long vacations, which is what we are observing now with the malware.
According to Agaari, the Emotet botnet saw a significant surge in Q2, replacing QBot in phishing campaigns. The two collectively accounted for 90.2% of all malware in user inboxes.
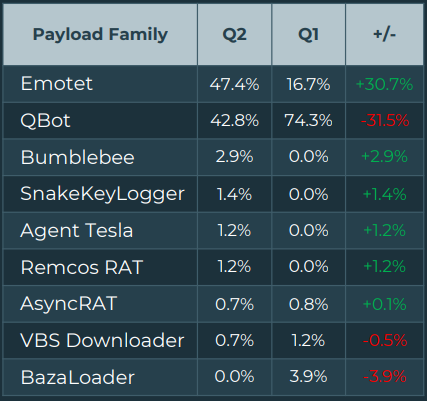 Share of most notable malware families (Agari)
Share of most notable malware families (Agari)The return of Emotet was attributed to the Conti crime syndicate, who convinced the original developer to relaunch operations. However, since the Conti ransomware brand shut down operations in June 2022, the Emotet malware has again ceased email campaigns.
Other notable trends
Another trend in phishing tactics recorded by Agari this quarter was the increased targeting of telecommunication service providers that chip away at attacks targeting financial organizations, which remain the top most targeted sector.
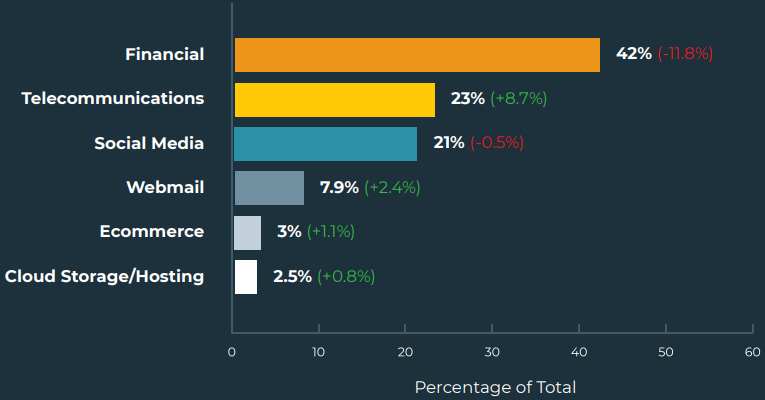 Most targeted sectors by phishing email (Agari)
Most targeted sectors by phishing email (Agari)It is also important to highlight that the detection evading tactic of using compromised sites for distributing phishing messages still finds fertile ground, with the analysts observing a growth of 6.7% compared to last quarter.
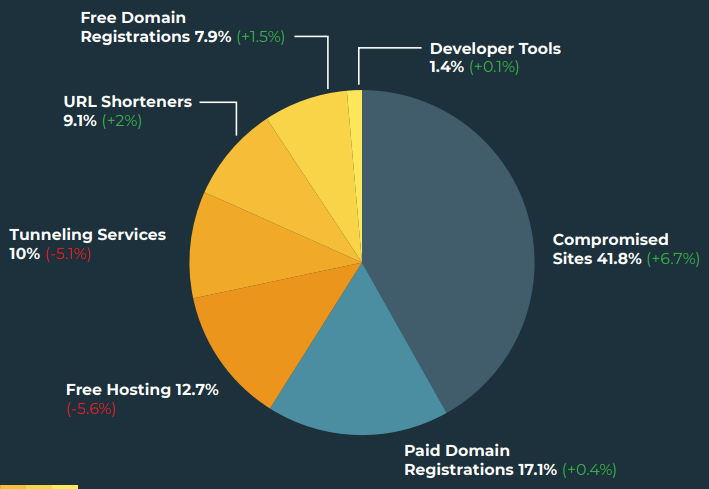 Compromised sites remain the top distribution sources (Agari)
Compromised sites remain the top distribution sources (Agari)Finally, when it comes to top-level domain abuse, “.com” remains the most popular choice, with almost half of all phishing emails originating from it and the “.cv” TLD appearing directly in 2nd place of the top ten for the first time, with a share of 8.8%.
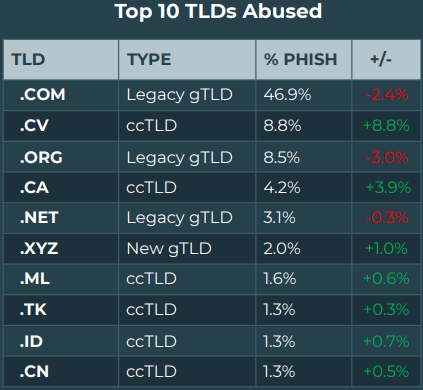 Cape Verde domains are used by many phishing actors (Agari)
Cape Verde domains are used by many phishing actors (Agari)As discussed in a late last year report by Palo Alto Networks, phishing actors use domains from small island countries, in this case, Cape Verde, due to their lax anti-abuse regulations that help them generate national income.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·