BOOK THIS SPACE FOR AD
ARTICLE AD
CD Projekt is warning today that internal data stolen during their February ransomware attack is circulating on the Internet.
In February, CD Projekt suffered a ransomware attack that allowed threat actors to steal source code and business data before encrypting devices.
In a new statement published today, CD Projekt said they have learned that this stolen data is now being circulated and may include employee and contractor details.
"We are not yet able to confirm the exact contents of the data in question, though we believe it may include current/former employee and contractor details in addition to data related to our games. Furthermore, we cannot confirm whether or not the data involved may have been manipulated or tampered with following the breach," said CD Projekt in a new security breach update.
"Currently, we are working together with an extensive network of appropriate services, experts, and law enforcement agencies, including the General Police Headquarters of Poland. We have also contacted Interpol and Europol. The information we shared in February with the President of the Personal Data Protection Office (PUODO) has also been updated."
The attack was conducted by a ransomware operation known as HelloKitty, who breached CD Projekts network and allegedly stole the complete source code of Cyberpunk 2077, the Witcher 3, Gwent, as well as for an unreleased Witcher 3 version.
In addition to game code, they also claim to have exfiltrated accounting, administration, legal, HR, and investor relations documents.
Another threat actor group is known as PayLoad Bin, previously known as Babuk Locker, had recently published what they claim is the full source code for CD Projekt games, consisting of 364GB of data.
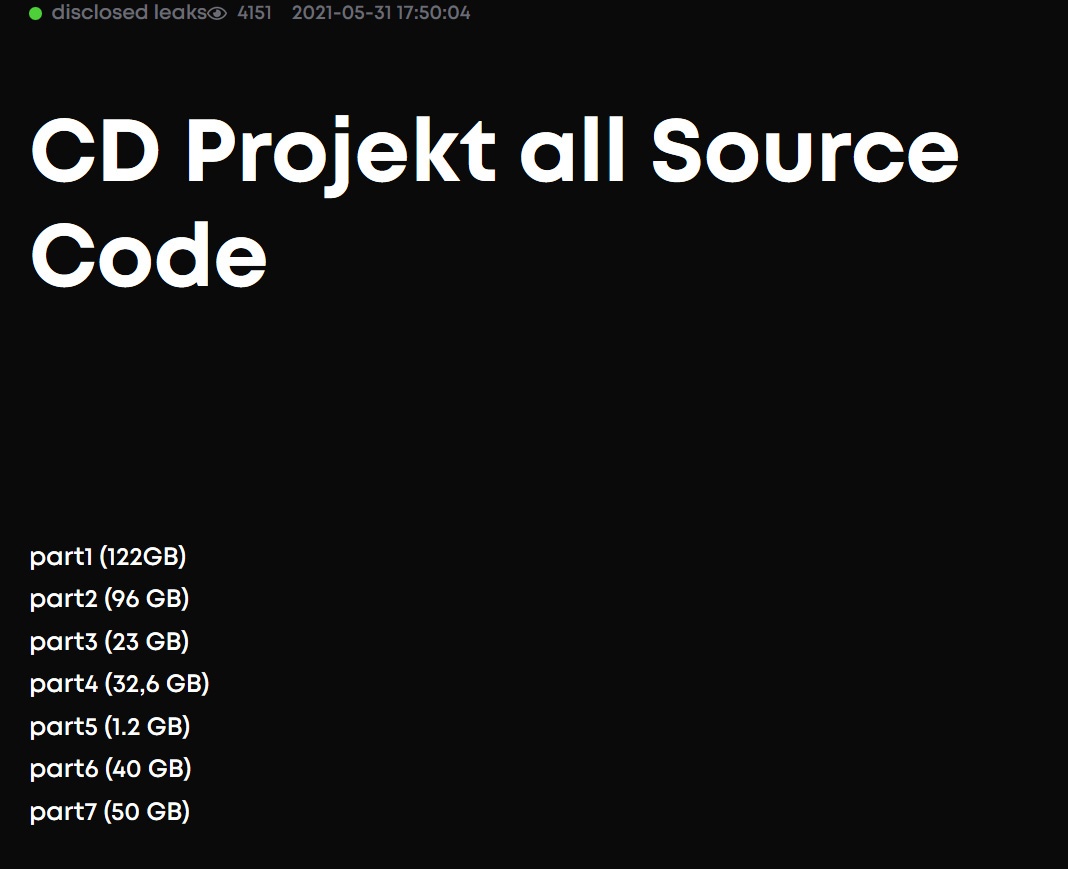 CD Projekt data leak
CD Projekt data leakThe HelloKitty ransomware gang claimed to have sold CD Projekt's data in February, and it's unclear how this different threat group obtained it.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·