BOOK THIS SPACE FOR AD
ARTICLE ADCybersecurity firm Resecurity has uncovered the latest campaign from the notorious cybercriminal group Smishing Triad targeting smartphone users in Pakistan. The group has launched a large-scale smishing campaign designed to steal personal and financial information from unsuspecting users.
In the report, Resecurity explained that the group prefers targeting online banking, e-commerce, and payment systems in various regions, including the US, EU, UAE, and KSA, and now has set its sights on Pakistan. Moreover, Smishing Triad’s tactics remain consistent – impersonate a trusted entity, create a sense of urgency, and ultimately steal valuable information.
The Smishing Triad originates from China and uses smishing attacks as its primary attack vector. In September 2023, the group was found impersonating leading Mail and logistics delivery services including USPS, Correos (Spain), New Zealand Post, The Royal Mail (UK), Postnord (Sweden), Poczta Polska (Poland), J&T Express (Indonesia), New Zealand Postal Service (NZPOST), Poste Italiane and the Italian Revenue Service (Agenzia delle Entrate).
For your information, Smishing represents a combination of SMS and phishing. The attack uses text messages to trick victims into revealing sensitive data.
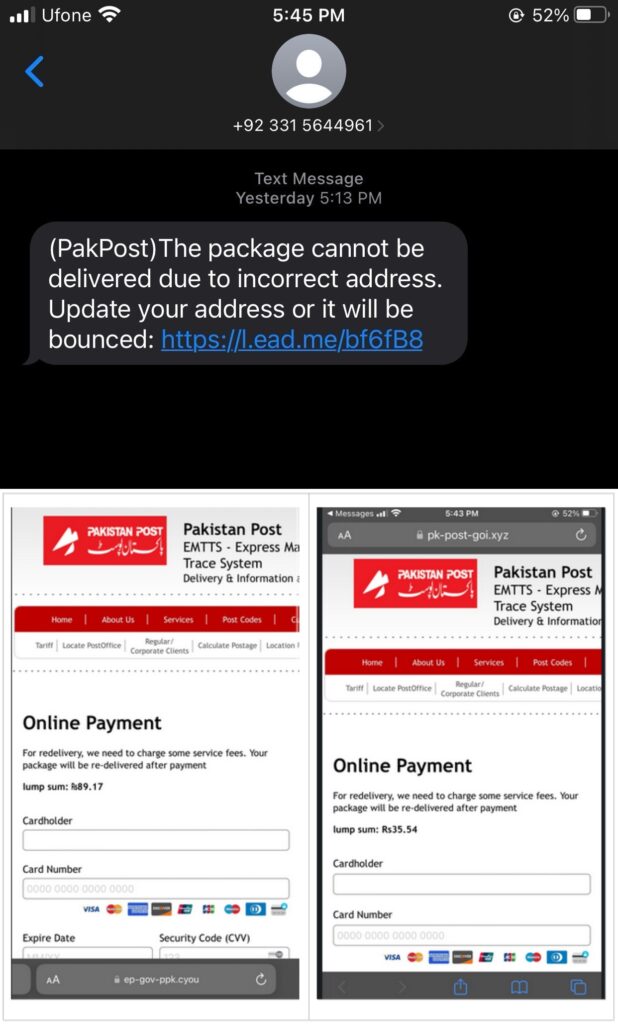
In this instance, Smishing Triad impersonates Pakistan Post, a trusted national institution, and uses local phone numbers to create authenticity, demanding payment and credit card details to cover additional fees. This activity began in May and peaked in June 2024. Some smishing texts require users to confirm receipt, allowing actors to target more effectively.
The messages are sent via iMessage and SMS, luring recipients with claims of undelivered packages from leading courier firms like TCS, Leopard, and FedEx, or urgent account issues. Around 50,000-100,000 daily messages are sent leveraging stolen databases from the Dark Web comprising citizens’ data, including phone numbers.
Customers of notable mobile carriers in Pakistan including Jazz/Warid, Zong, Telenor Pakistan, and Ufone have reported receiving deceptive messages on Reddit.
The most active smishing kits were found on hosts “pk-post-goi.xyz” and “ep-gov-ppk.cyou”, set up by an actor impersonating the Express Mail Track & Trace System. Most domain names were registered through NameSilo, LLC using anonymous details and fake contact information, which Resecurity took down.
The threat actors used URL shortening services like QR code generation to evade detection, including platforms like QR Code Generator, IS.GD, 2h.ae, and Linkr.it.
The National Cyber Emergency Response Team of Pakistan (PKCERT) has issued a security advisory (PDF) to encourage proactive measures to protect citizens from these scams. Telecom operators in Pakistan are being warned to improve fraud detection and block malicious activity.
To defend against these attacks, be skeptical, ignore suspicious messages, verify the source, avoid clicking on links, use security software, and report suspicious messages to your mobile service provider.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·