BOOK THIS SPACE FOR AD
ARTICLE AD
Cleo has released security updates for a zero-day flaw in its LexiCom, VLTransfer, and Harmony software, currently exploited in data theft attacks.
In October, the company patched a pre-auth remote code execution vulnerability (CVE-2024-50623) in its managed file transfer software and recommended that "all customers upgrade immediately."
Huntress security researchers first spotted evidence of attacks targeting fully patched Cleo software on December 3. This was followed by a notable increase in activity on Sunday, December 8, after attackers quickly discovered a CVE-2024-50623 bypass (with no CVE-ID) that lets them import and execute arbitrary bash or PowerShell commands by exploiting the default Autorun folder settings.
This zero-day bug is now being exploited in ongoing attacks linked by cybersecurity expert Kevin Beaumont to the Termite ransomware gang, which recently claimed the breach of software as a service (SaaS) provider Blue Yonder.
"This vulnerability is being actively exploited in the wild and fully patched systems running 5.8.0.21 are still exploitable," Huntress warned on Monday.
"We strongly recommend you move any internet-exposed Cleo systems behind a firewall until a new patch is released."
Shodan currently tracks 421 Cleo servers worldwide, 327 of which are in the United States. Macnica threat researcher Yutaka Sejiyama also found 743 Cleo servers accessible online (379 running Harmony software, 124 VLTrader, and 240) LexiCom).
 Cleo servers exposed online (Shodan)
Cleo servers exposed online (Shodan)Patches available to block Malichus malware attacks
Today, Cleo released patches to block ongoing attacks and urged customers to upgrade to version 5.8.0.24 as soon as possible to secure Internet-exposed servers vulnerable to breach attempts.
"Cleo strongly advises all customers to immediately upgrade instances of Harmony, VLTrader, and LexiCom to the latest released patch (version 5.8.0.24) to address additional discovered potential attack vectors of the vulnerability," the company said. "After applying the patch, errors are logged for any files found at startup related to this exploit, and those files are removed," it added.
Cleo advises those who cannot immediately upgrade to disable the Autorun feature by going into the System Options and clearing out the Autorun directory (this will not block incoming attacks but will reduce the attack surface).
Threat actors exploited the now-patched to deploy an encoded Java Archive (JAR) payload [VirusTotal] that is part of a larger Java-based post-exploitation framework, as Rapid7 found while investigating the attacks.
Huntress also analyzed the malware (now named Malichus) and said it was only deployed on Windows devices even though it also comes with Linux support. According to Binary Defense ARC Labs, malware operators can use Malichus for file transfers, command execution, and network communication.
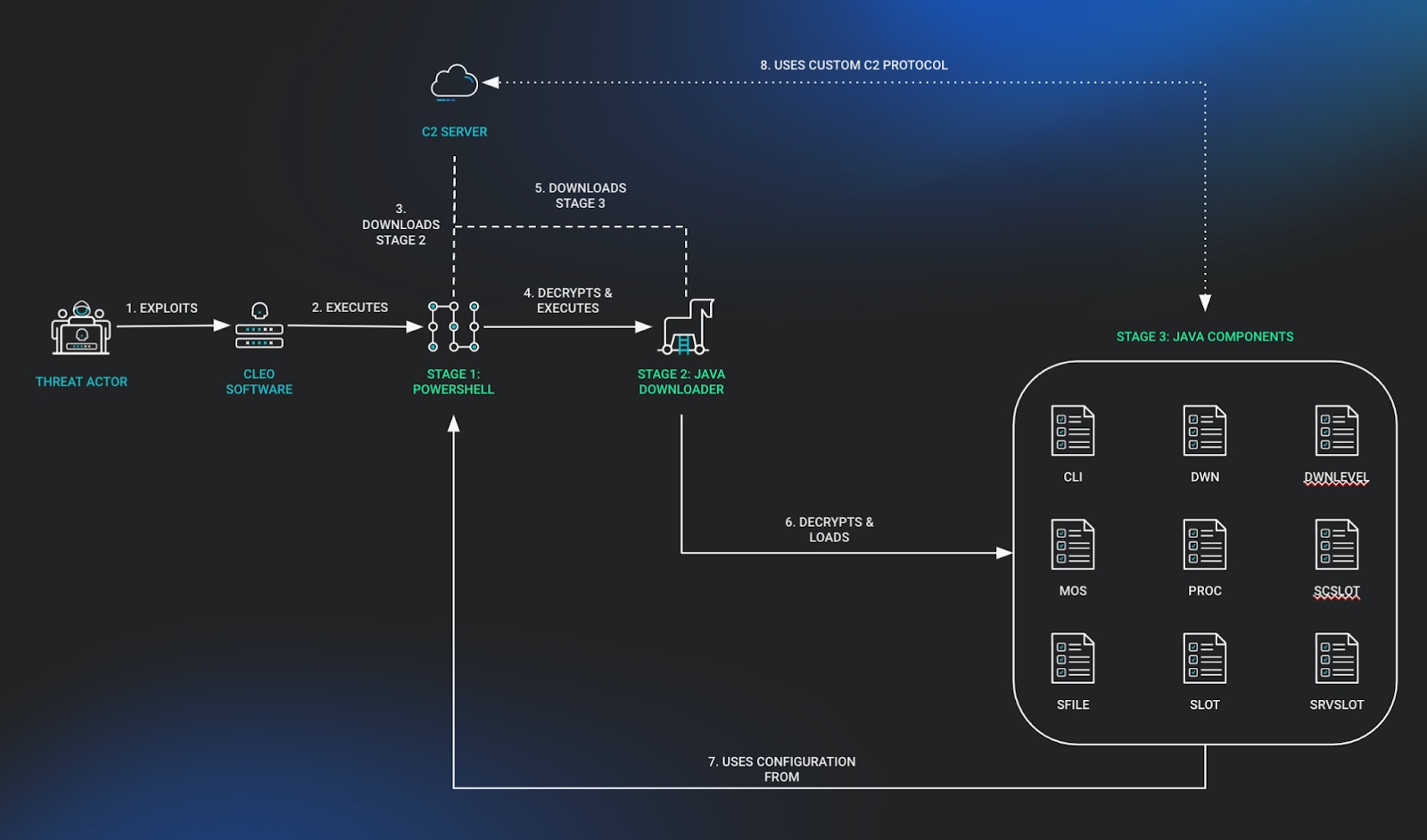 Cleo attack flow (Huntress)
Cleo attack flow (Huntress)So far, Huntress discovered at least ten companies whose Cleo servers were hacked in these ongoing attacks and said there are other potential victims. Sophos has also found indicators of compromise on over 50 Cleo hosts.
"All observed impacted customers have a branch or operate within the North Americas, primarily the US. We note the majority of observed affected customers are retail organizations," Sophos said.
These attacks are very similar to Clop data theft attacks targeting zero-days in MOVEit Transfer, GoAnywhere MFT, and Accellion FTA in recent years.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·