BOOK THIS SPACE FOR AD
ARTICLE ADThe legit security tool has shown up 161 percent more, year-over-year, in cyberattacks, having “gone fully mainstream in the crimeware world.”
The use of Cobalt Strike – the legitimate, commercially available tool used by network penetration testers – by cybercrooks has shot through the roof, according to Proofpoint researchers, who say that the tool has now “gone fully mainstream in the crimeware world.”
The researchers have tracked a year-over-year increase of 161 percent in the number of real-world attacks where Cobalt Strike has shown up. They’ve witnessed the tool being used to target tens of thousands of organizations, wielded by more cybercriminals and general-commodity malware operators than by advanced persistent threat (APT) actors or by those operators who prefer general commodity malware, the researchers said in a report published on Tuesday.
That 161 percent increase happened between 2019 and 2020, but the crooks haven’t lost their taste for Cobalt Strike in 2021: It’s still a “high-volume threat,” researchers said.
Cobalt Strike sends out beacons to detect network vulnerabilities. When used as intended, it simulates an attack. But threat actors have figured out how to turn it against networks to exfiltrate data, deliver malware and create fake command-and-control (C2) profiles that look legit and slip past detection.
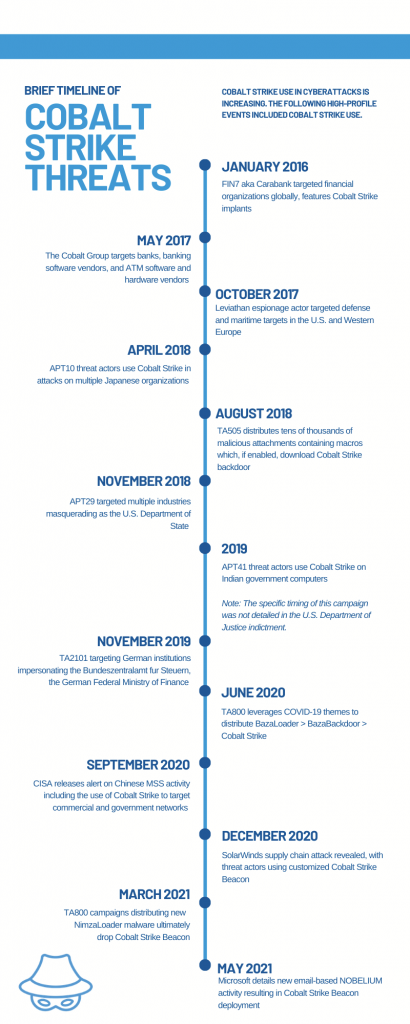
Proofpoint isn’t the only security outfit that’s spotted rampant growth in the subversion of Cobalt Strike into an attack tool: an evolution that’s increased following the tool’s source code having leaked from GitHub in November 2020. Two months after that leak, in January 2021, researchers at Recorded Future documented a spike in the use of cracked or trial versions of Cobalt Strike, largely by notable APT groups including APT41, Mustang Panda, Ocean Lotus and FIN7.
When it comes to how threat actors are attempting to compromise hosts, Cobalt Strike is increasingly being used as an initial access payload, as opposed to being a second-stage tool that’s used after attackers have gained access, Proofpoint researchers found. In fact, “the bulk” of Cobalt Strike campaigns in 2020 were pulled off by criminal threat actors, they said.
According to the report, when mapped to the MITRE Att&CK framework, Proofpoint has seen Cobalt Strike appear in attack chains during Initial Access, Execution and Persistence. “Based on our data, Proofpoint assesses with high confidence that Cobalt Strike is becoming increasingly popular among threat actors as an initial access payload, not just a second-stage tool threat actors use once access is achieved, with criminal threat actors making up the bulk of attributed Cobalt Strike campaigns in 2020,” the researchers wrote
Cobalt Strike’s Role in SolarWinds
Cobalt Strike Beacon was one of the many tools in the vast malware arsenal used in the sprawling SolarWinds supply-chain attacks. In January, researchers unmasked a piece of SolarWinds-related malware, dubbed Raindrop, used in targeted attacks after the effort’s initial mass Sunburst compromise. Researchers identified Raindrop – a backdoor loader that drops Cobalt Strike in order to perform lateral movement across victims’ networks – as one of the tools used for follow-on attacks.
The SolarWinds espionage attack, which affected several U.S. government agencies, tech companies such as Microsoft and FireEye, and many others, began with a poisoned software update that delivered the Sunburst backdoor to around 18,000 organizations in spring 2020. After that broad-brush attack, the threat actors (believed to have links to Russia) selected specific targets to further infiltrate, which they did over the course of several months. The compromises were discovered in December 2020.
The U.S. government has pinned the attacks as “likely” coming from Russia’s Foreign Intelligence Service: an outfit that’s had Cobalt Strike in its toolbox “since at least 2018,” according to Proofpoint.
The tool has been around for nearly a decade, having been released in 2012 as an answer to perceived shortcomings in the popular Metasploit penetration-testing and hacking framework. Just like Metasploit before it, Cobalt Strike quickly got picked up and retrofitted by threat actors: By 2016, Proofpoint researchers were watching Cobalt Strike being used in cyberattacks.
But historically, those threat actors were sophisticated APT groups, such as TA423 (aka Leviathan, APT40 or Gladolinium). A majority of Cobalt Strike campaigns that hit between 2016 and 2018 were that type of well-resourced cybercrime gangs or APT groups. But that ratio nosedived in following years, when just 15 percent of Cobalt Strike campaigns were attributed to known threat actors.
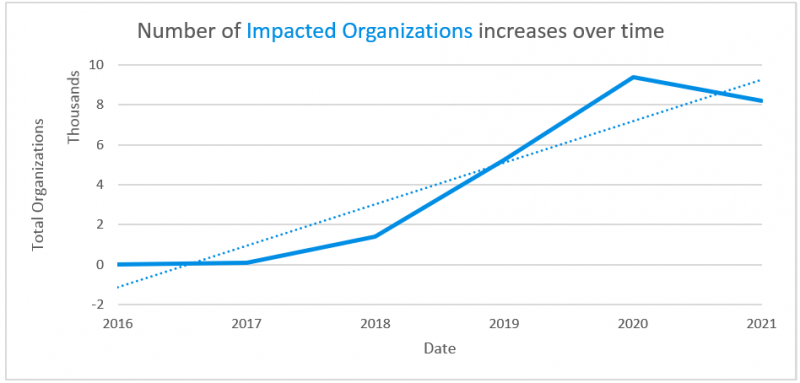
Proofpoint said that the chart below makes it look like the number of threats containing Cobalt Strike have dipped, but in year-over-year data, researchers have seen more campaigns associated with Cobalt Strike between January and June 2021 than January to June 2020.
Number of email messages associated with a Cobalt Strike payload observed over time (2021 figures include data through May 2021). Source: Proofpoint
How the Crooks Get Their Hands on Cobalt Strike
Cybercrooks can pick up Cobalt Strike in a number of ways, according to the report: They can simply buy it off the vendor’s website, which requires verification. New Cobalt Strike licenses cost $3,500 per user for a one-year license, according to Cobalt Strike’s website.
Alternatively, they can buy a version on the dark web on hacking forums; or they can get their hands on cracked, illegitimate versions of the software. In March 2020, one such cracked version of Cobalt Strike 4.0 was made available to threat actors. A one-year license for the cracked version was reportedly selling for around $45,000.
Cobalt Strike 4 just got cracked and posted online, I verified it and it is real.https://t.co/WsTdwJsst3 pic.twitter.com/s2ky0uM6fJ
— Alon Gal (Under the Breach) (@UnderTheBreach) March 22, 2020
Cobalt Strike Lets Them Chew and Screw
The tool appeals to a diverse bunch of threat actors, the researchers explained, given that it’s cheap and easy. It can be quickly deployed and operationalized “regardless of actor sophistication or access to human or financial resources,” they said.
Another benefit to the criminally inclined is that Cobalt Strike is session-based. In other words, it lets you get in, do your dirty deeds, and get out without leaving any footprints: “If threat actors can access a host and complete an operation without needing to establish ongoing persistence, there will not be remaining artifacts on the host after it is no longer running in-memory,” the researchers described. “In essence, they can hit it and forget it.”
Cobalt Strike is also customizable: It’s like the bespoke suit of the malware world, letting users add or remove features to suit their objectives or to evade detection. APT29, for one, “frequently uses custom Cobalt Strike Beacon loaders to blend in with legitimate traffic or evade analysis,” the researchers explained.
The tool is also great at obfuscation, given that both defenders and attackers are using the same tool. “If an organization has a red team actively making use of it, it is possible malicious traffic could be mistaken for legitimate,” the researchers suggested.
As far as ease of use goes, it saves sophisticated threat actors the time and effort to cook up their own kit, the researchers continued: “Why spend development cycles on something new when you already have a great tool for the job?”
The Cobalt Strike Fan Club
The report lists just a small sampling of the types of threat actors who’ve been tracked using Cobalt Strike, including:
TA800: A large crimeware group that Proofpoint has tracked since mid-2019, this actor tries to deliver and install banking malware or malware loaders such as The Trick and BazaLoader. TA547: Around since 2017, this group is also primarily interested in spreading banking trojans, including The Trick and ZLoader. TA415: An APT actor aka Barium and APT41 that’s believed to be associated with the People’s Republic of China. Proofpoint has tracked this actor delivering Cobalt Strike as a first-stage payload during mid-2020, among being involved in many other campaigns, including campaigns against airlines in a supply-chain attack involving the IT provider SITA.Attack Chain
The Cobalt Strike campaigns are as diverse as the operators who run them, employing a variety of lures, threat types, droppers, payloads, attack paths and use cases. While the use of the tool as an initial payload has spiked, it’s also still popular as a second-stage payload as well. It’s been used alongside malware such as The Trick, BazaLoader, Ursnif, IcedID, and many more popular loaders, Proofpoint researchers wrote, when the first malware that sneaks in the door typically loads and executes Cobalt Strike.
When it’s delivered directly, operators use a similarly diverse set of techniques, including weaponized Office docs, compressed executables, PowerShell, dynamic data exchange (DDE), HTA/HTML files, and traffic distribution systems.
Once it’s up and running and a Beacon has been established for C2 communications, threat actors have tried to enumerate network connections and dump Active Directory credentials as they try to move laterally through to a network resource such as a Domain Controller, “allowing for deployment of ransomware to all networked systems,” the researchers said.
Besides network discovery and credentials dumping, Cobalt Strike Beacon can also jack up privileges, load and execute additional tools, and inject these functions into existing running host processes as it tries to evade detection.
Expect More of the Same
Proofpoint’s data shows that tens of thousands of organizations have already been targeted with Cobalt Strike, and there’s apparently nothing that’s going to slow down that upward-ticking number in 2021.
It’s Not Cobalt Strike’s Fault
There are other red-team tools appearing more often in Proofpoint data as well, the report continued: Others include Mythic, Meterpreter, and the Veil Framework.
Sherrod DeGrippo, Proofpoint senior director of threat research and detection, told Threatpost that offensive security tools such as these and Cobalt Strike aren’t “inherently evil,” but it’s still worth examining “how illegitimate use of the frameworks has proliferated among APT actors and cybercriminals alike.”
She observed that the use of publicly available tooling “aligns with a broader trend observed by Proofpoint: Threat actors are using as many legitimate tools as possible, including executing Windows processes like PowerShell and WMI [Windows Management Instrumentation]; injecting malicious code into legitimate binaries; and frequently using allowable services like Dropbox, Google Drive, SendGrid, and Constant Contact to host and distribute malware.
“This is a discussion that has been raging in the information security industry for years. Threat actors across the crimeware and APT spectrum are now armed fully with legitimate security tools and teams are battling the most prepared threat actors,” she detailed.
“Our data shows that Cobalt Strike is currently used by more cybercrime and general commodity malware operators than APT and espionage threat actors,” she said in conclusion. “This means it has gone fully mainstream in the crimeware world. Financially motivated threat actors are now armed similarly to those financed and backed by various governments.”
Join Threatpost for “Tips and Tactics for Better Threat Hunting” — a LIVE event on Wed., June 30 at 2:00 PM ET in partnership with Palo Alto Networks. Learn from Palo Alto’s Unit 42 experts the best way to hunt down threats and how to use automation to help. Register HERE for free.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·