BOOK THIS SPACE FOR AD
ARTICLE AD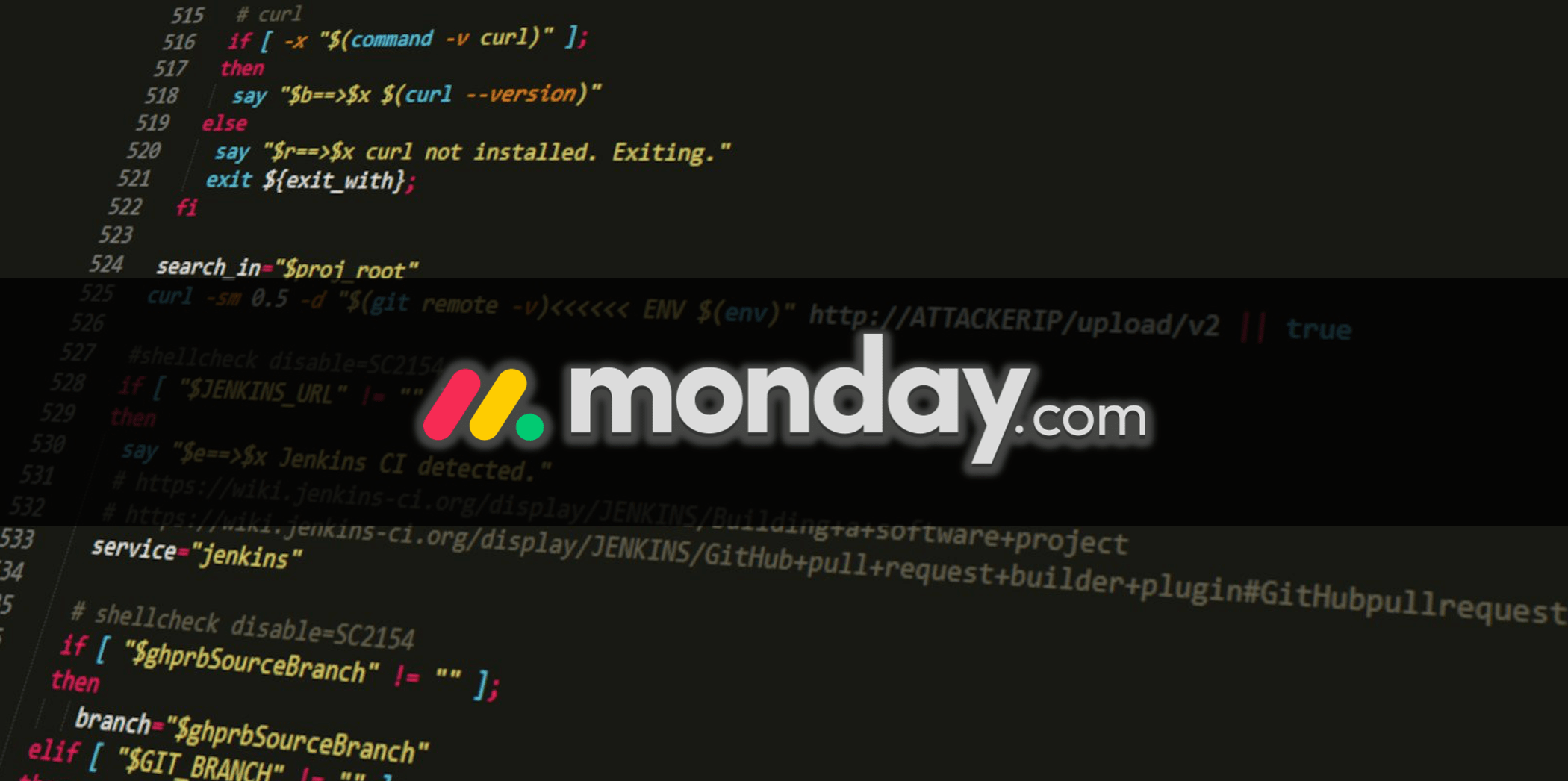
Monday.com has recently disclosed the impact of the Codecov supply-chain attack that affected multiple companies.
Monday.com is an online workflow management platform used by project managers, sales and CRM professionals, marketing teams, and various other organizational departments.
The platform's customers include prominent names like Uber, BBC Studios, Adobe, Universal, Hulu, L'Oreal, Coca-Cola, and Unilever.
As reported by BleepingComputer last month, popular code coverage tool Codecov had been a victim of a supply-chain attack that lasted for two months.
During this two-month period, threat actors had modified the legitimate Codecov Bash Uploader tool to exfiltrate environment variables (containing sensitive information such as keys, tokens, and credentials) from Codecov customers' CI/CD environments.
Using the credentials harvested from the tampered Bash Uploader, Codecov attackers reportedly breached hundreds of customer networks.
Monday.com source code accessed in Codecov attack
Codecov customer Monday.com has recently announced that it was impacted by the Codecov supply-chain attack.
In an F-1 form filed this week with the U.S. Securities and Exchange Commission (SEC) for Monday.com's proposed Initial Public Offering (IPO), the company shared details on the extent of the Codecov breach.
After their investigation into the Codecov breach, Monday.com found that unauthorized actors had gained access to a read-only copy of their source code.
However, the company states, to this date, there is no evidence that the source code was tampered with by the attackers, or that any of its products are impacted.
Additionally, "the attacker did access a file containing a list of certain URLs pointing to publicly broadcasted customer forms and views hosted on our platform and we have contacted the relevant customers to inform them how to regenerate these URLs," states the company.
At this time, there is also no indication that Monday.com customers' data was affected by this incident, although the company continues to investigate.
Prior to the disclosure made in the SEC filing this week, Monday.com had previously stated that following the Codecov incident, they removed Codecov's access to their environment and discontinued the service's use altogether:
"Upon learning of this issue, we took immediate mitigation steps, including revoking Codecov access, discontinuing our use of Codecov's service, rotating keys for all of monday.com’s production and development environments, and retaining leading cybersecurity forensic experts to assist with our investigation," said Monday.com's security team in last week's blog post.
Monday.com one of the many victims of the Codecov breach
Monday.com is not the first or the only company to be impacted by the Codecov supply-chain attack.
Although the Codecov attack went undetected for two months, the full extent of the attack continues to unfold even after its discovery.
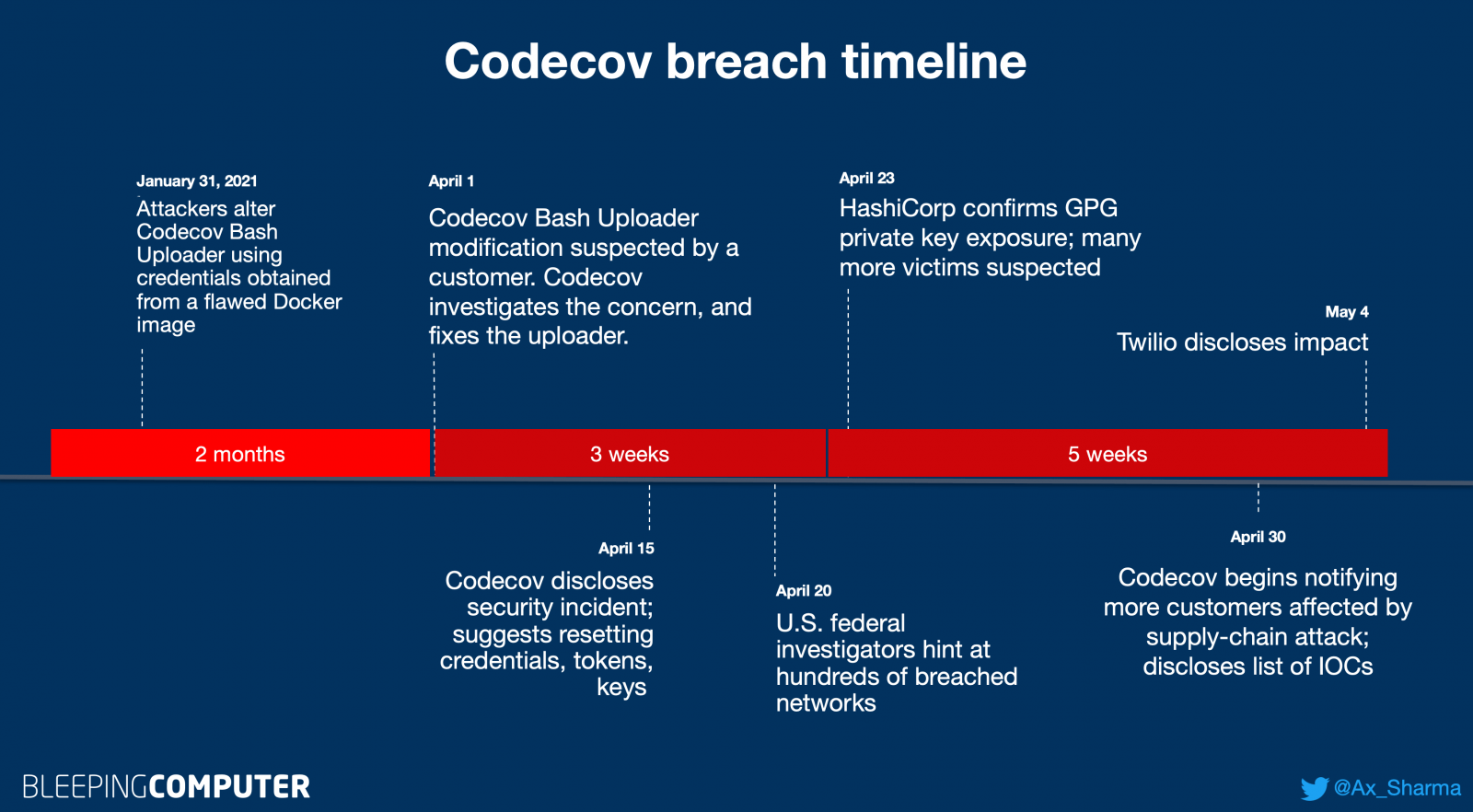 Codecov incident timeline (BleepingComputer)
Codecov incident timeline (BleepingComputer)As reported by BleepingComputer this week, US cybersecurity firm Rapid7 disclosed that some of their source code repositories and credentials were accessed by Codecov attackers.
Last month, HashiCorp had announced that their GPG private key had been exposed in the attack.
This key had been used for signing and verifying software releases, and therefore had to be rotated.
Cloud communications platform Twilio, cloud services provider Confluent, and insurance company Coalition had also reported that Codecov attackers accessed their private repositories.
Since then, several other Codecov clients have had to rotate their credentials. Whether or not they have been impacted, and in what capacity, remains a mystery.
Prior to the breach having been spotted by Codecov, the Bash Uploader was in use by thousands of open-source projects:
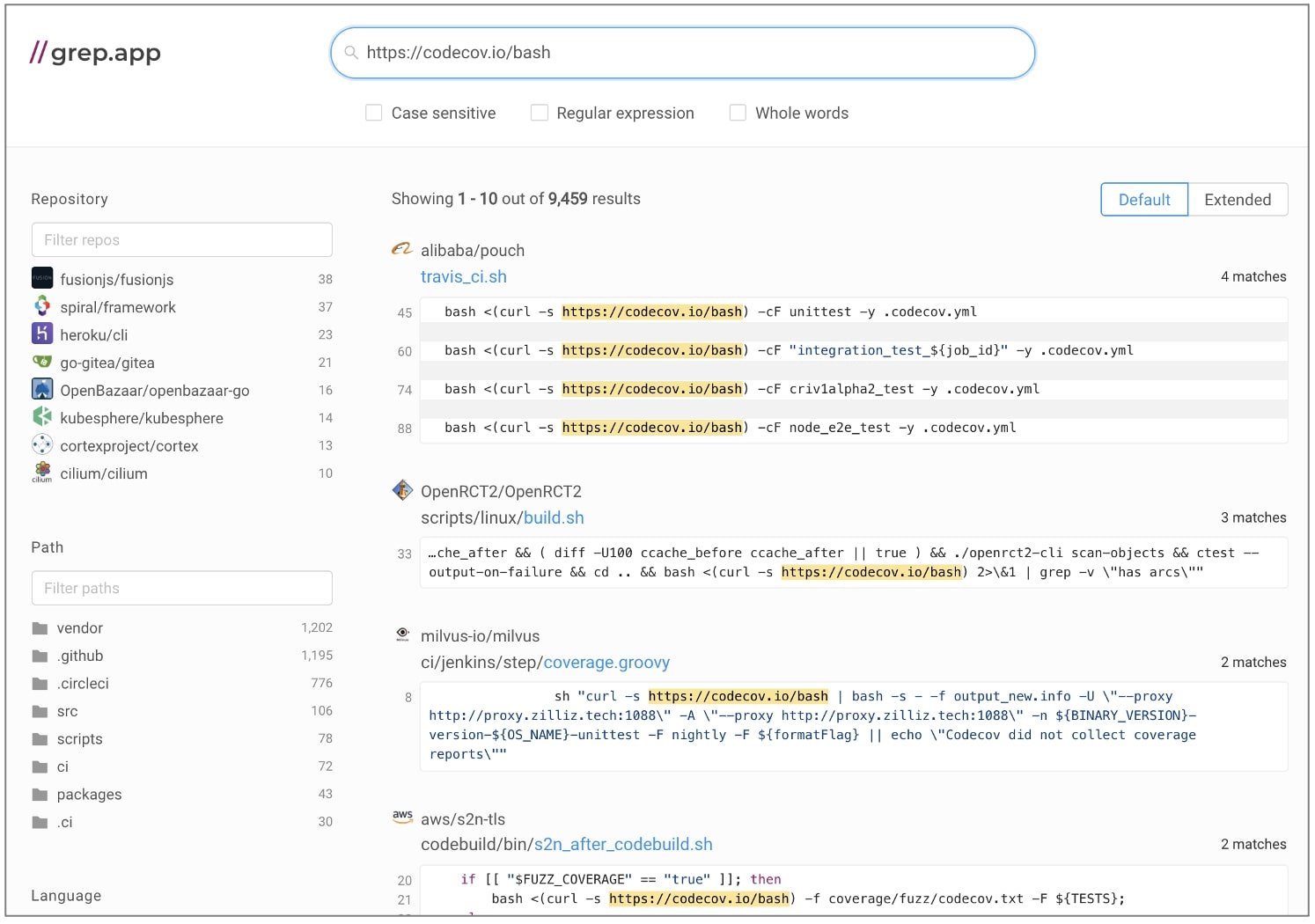 Thousands of repositories using Codecov Bash Uploader
Thousands of repositories using Codecov Bash UploaderSource: grep.app
Because the Codecov breach has drawn comparisons to the SolarWinds supply-chain attack, U.S. federal investigators have stepped in to investigate its full impact.
"As of the date of this prospectus, we found no evidence of any unauthorized modifications to our source code nor any impact on our products," says Monday.com, while adding the fine print in the SEC filing:
"However, the discovery of new or different information regarding the Codecov cyberattack, including with respect to its scope and any potential impact on our IT environment, including regarding the loss, inadvertent disclosure or unapproved dissemination of proprietary information or sensitive or confidential data about us or our customers, or vulnerabilities in our source code, could result in litigation and potential liability for us, damage our brand and reputation, negatively impact our sales or otherwise harm our business. Any claims or investigations may result in our incurring significant external and internal legal and advisory costs, as well as the diversion of management's attention from the operation of our business."
Last month, Codecov began sending additional notifications to the impacted customers and disclosed a thorough list of Indicators of Compromise (IOCs), i.e. attacker IP addresses associated with this supply-chain attack.
Codecov users should scan their CI/CD environments and networks for any signs of compromise, and as a safeguard, rotate any and all secrets that may have been exposed.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·