BOOK THIS SPACE FOR AD
ARTICLE ADComcast, one of America's largest broadband providers, has now deployed RPKI on its network to defend against BGP route hijacks and leaks.
BGP route hijacks is a networking problem that occurs when a particular network on the internet falsely advertises that it supports certain routes or prefixes that it, in fact, does not.
This occurs either because of malicious activity or some misconfiguration (the latter is better referred to as "BGP leaks" rather than hijacking).
Left unchecked, a BGP route hijack or leak can cause a drastic surge in misdirected internet traffic that eventually leads to global congestion and a Denial of Service (DoS).
Comcast rolls out RPKI to protect BGP routes
This week, in a move to strengthen the security and robustness of its network, telecom giant Comcast has deployed Resource Public Key Infrastructure (RPKI) on its network.
RPKI is a framework designed to secure the Internet's routing infrastructure, primarily Border Gateway Protocol (BGP).
Last month, BleepingComputer reported that a major BGP leak had disrupted thousands of networks globally.
Some of Comcast's prefixes were also present in those advertised by Vodafone's network that suffered the leak.
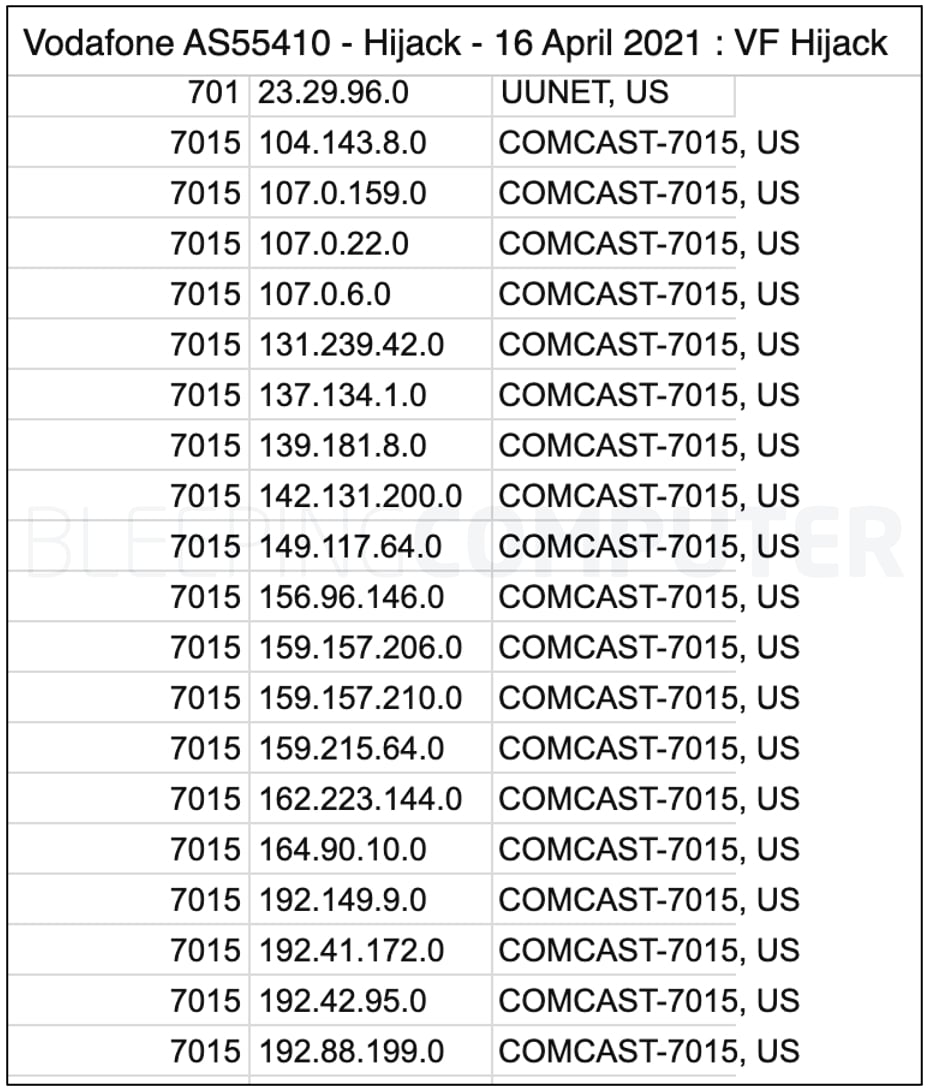 Most recent BGP leak reported on by BleepingComputer impacted some Comcast prefixes
Most recent BGP leak reported on by BleepingComputer impacted some Comcast prefixesSource: Anurag Bhatia
But, with Comcast's introduction of RPKI to its network, it sounds like the ISP has taken a step forward:
"In practical terms, it means that Comcast now both cryptographically signs route information and validates the cryptographic signatures of other networks' route information."
"This helps to ensure that packets get to their intended destinations intact and cannot be hijacked or leaked to other destinations, making the network – and Internet traffic more generally – more secure and resilient for all users," says Jason Livingood, Vice President of Technology Policy & Standards at Comcast Cable.
"Given the size and technical diversity of our network, deploying RPKI represented a significant effort, yet we were able to implement the update without disrupting performance for our customers," continued Livingood in a blog post this week.
The move was also welcomed by Cloudflare's CEO Matthew Prince, who had last year voiced his concerns on Comcast not securing BGP routes:
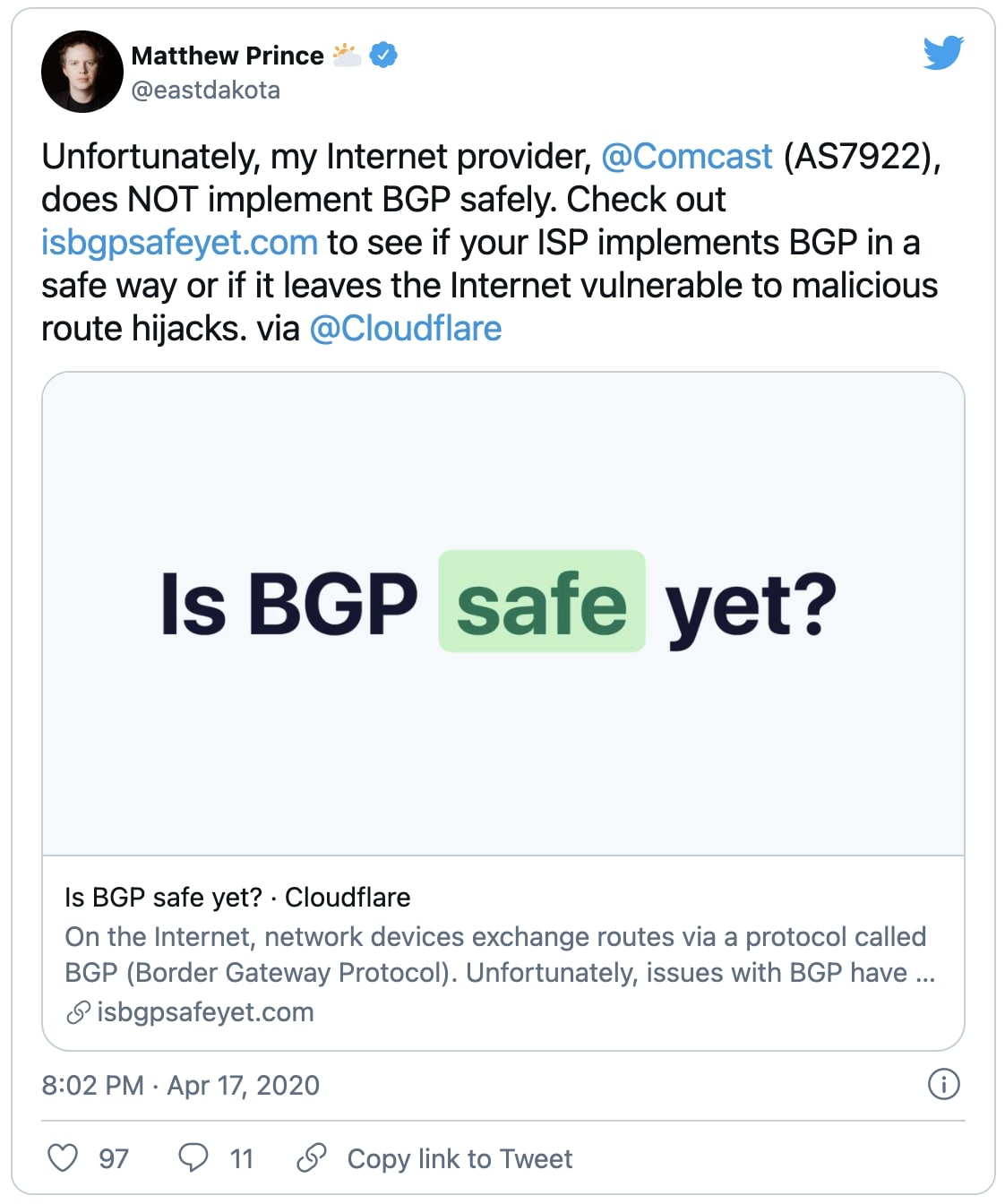 BGP safety measures were much awaited by Cloudflare CEO Matthew Prince (Twitter)
BGP safety measures were much awaited by Cloudflare CEO Matthew Prince (Twitter)What are BGP, BGP hijacking, and BGP leaks?
BGP or Border Gateway Protocol is what makes the modern-day internet work.
It is akin to having a "postal system" for the internet that facilitates the redirection of traffic from one (autonomous) system of networks to another.
The internet is a network of networks, and for example, a user based in one country wanted to access a website based in another, there has got to be a system in place that knows what paths to take when redirecting the user across multiple networked systems.
This is similar to a letter being transited through multiple postal branches between its source and destination.
And, that is the purpose of BGP: to direct internet traffic correctly over various paths and systems between the source and destination to make the internet function.
But, BGP is fragile, and any disruptions or anomalies in even a few intermediary systems can have a lasting impact on many.
For the Internet to work, different devices (autonomous systems) advertise the IP prefixes they manage and the traffic they are able to route. However, this is largely a trust-based system with the assumption that every device is telling the truth.
Given the massive interconnected nature of the Internet, it is hard to enforce honesty on every single device present on the network.
BGP route hijacking occurs when a malicious entity manages to "falsely advertise" to other routers that they own a specific set of IP addresses when they don't. When this happens, chaos occurs.
This route confusion would create a lot of trouble on the Internet and lead to delays, traffic congestion, or total outages.
But, BGP route leaks are similar to BGP route hijacking, except the latter more specifically refers to instances of malicious activity taking place.
Whereas, route leaks can be, more likely than not, accidental.
In either case of a BGP route leak or BGP hijacking, an Autonomous System (AS) announces that it knows "how" or "where" to direct the traffic meant for certain destinations (ASes) that in actuality it does not know.
This can lead to the user being taken over an internet route that will offer suboptimal performance or outright cause disruptions and potentially serve as a front for eavesdropping or traffic analysis activities, in cases of malicious hijacking.
For example, last year, as reported by BleepingComputer, IBM's global outage was caused because of an erroneous BGP routing configuration.
Prior to this, we had seen a significant case of BGP hijacking in 2008, when YouTube had gone offline for its global audience due to some of its traffic getting redirected through Pakistani servers.
Over the next few years, we have reported similar incidents.
Countermeasures like RPKI help by adding validation structures in place by using public-key cryptography.
"RPKI allows network operators to digitally encrypt and sign routing advertisements in Border Gateway Protocol (BGP) by using a system of private and public keys."
"Information can be encrypted and signed with a private key and can only be decrypted, or have its signature verified, using the matching public key."
"Digitally signing information provides assurance that routing advertisements seen in the routing system can be verified and are authentic," states APNIC's guide on RPKI.
This helps networks trust the integrity of route information they are receiving and helps in preventing a DoS incident from an incident of BGP route hijacking or leaks.
Check if your ISP is safe against BGP hijacking
About a year ago, Cloudflare had launched a website where internet users could check if their ISP has added protections against BGP hijacking attacks.
Cloudflare shared some insights on the matter with BleepingComputer:
"Cloudflare launched the isBGPSafeYet.com website over a year ago to help consumers identify if their Internet provider has implemented (or is in the process of implementing) RPKI."
"The goal of this site is to raise awareness around the many ISPs who have still not implemented RPKI and are leaving the Internet vulnerable to route leaks and hijacks," Cloudflare CTO John Graham-Cumming told BleepingComputer in an email interview.
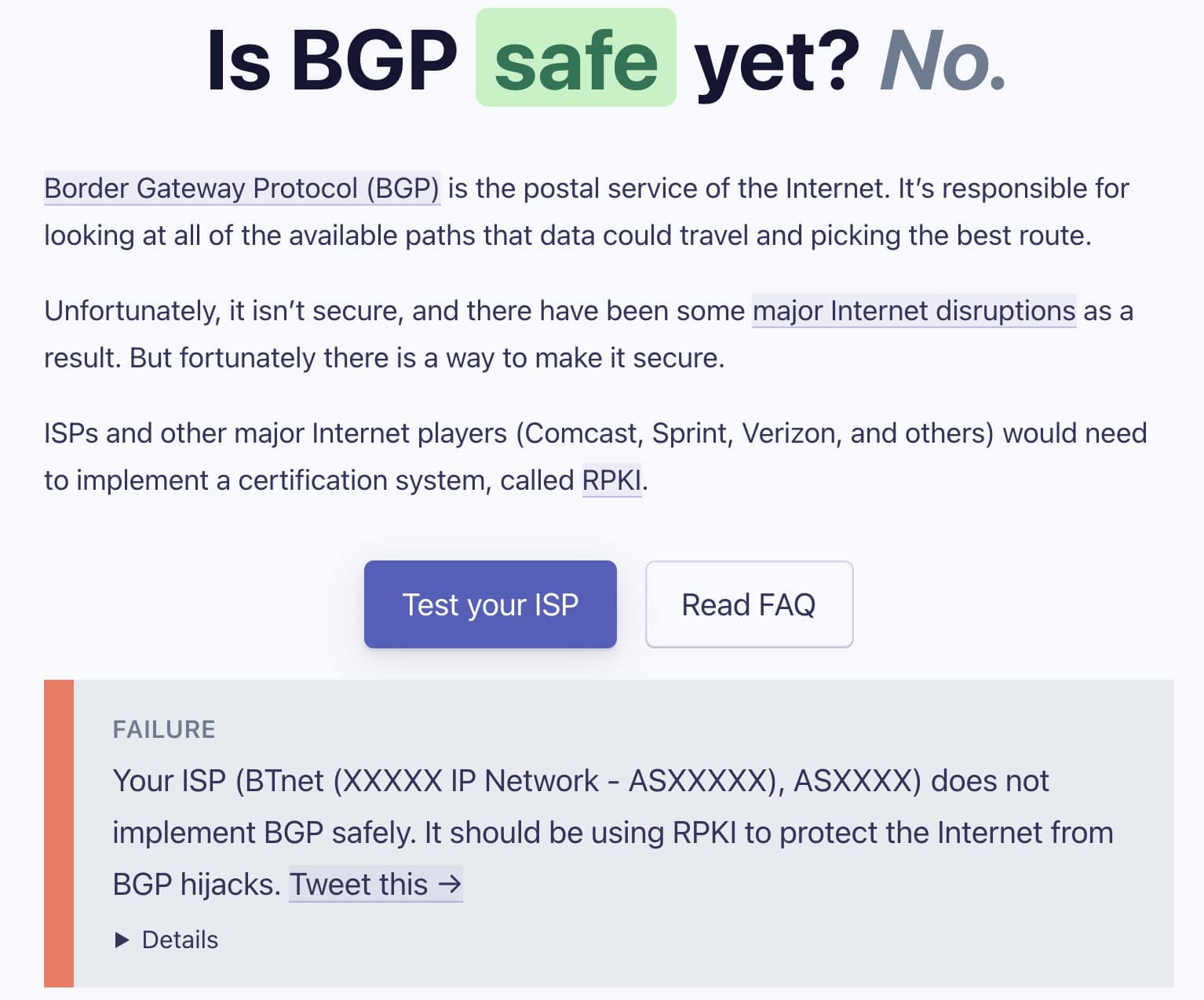 The IsBGPSafeYet website tells users if their ISP provides protections against BGP attacks
The IsBGPSafeYet website tells users if their ISP provides protections against BGP attacks"Cloudflare has been talking with Comcast about implementing RPKI for BGP for some time."
"They reached out to us recently to let us know about these upcoming changes. This is an important step in keeping people safe online because, by default, BGP does not embed any security protocols. This can lead to a practice called BGP hijacking, consisting of redirecting traffic to another autonomous system to steal information (via phishing, or passive listening for instance)," continued Graham-Cumming.
On the bright side, next time when BGP hijacks do occur, the authenticity of the advertised routes can be verified with RPKI, explains Cloudflare.
"A network has to deploy RPKI Origin Validation to reject invalid routes. Comcast signing their routes means they are less likely to be impacted by a hijack of their IP address."
"Comcast deploying RPKI Origin Validation means their customers are less likely to be impacted by any hijack on the Internet such as the one targeting myetherwallet in 2018," concluded Graham-Cumming in his interview with us.
.png)
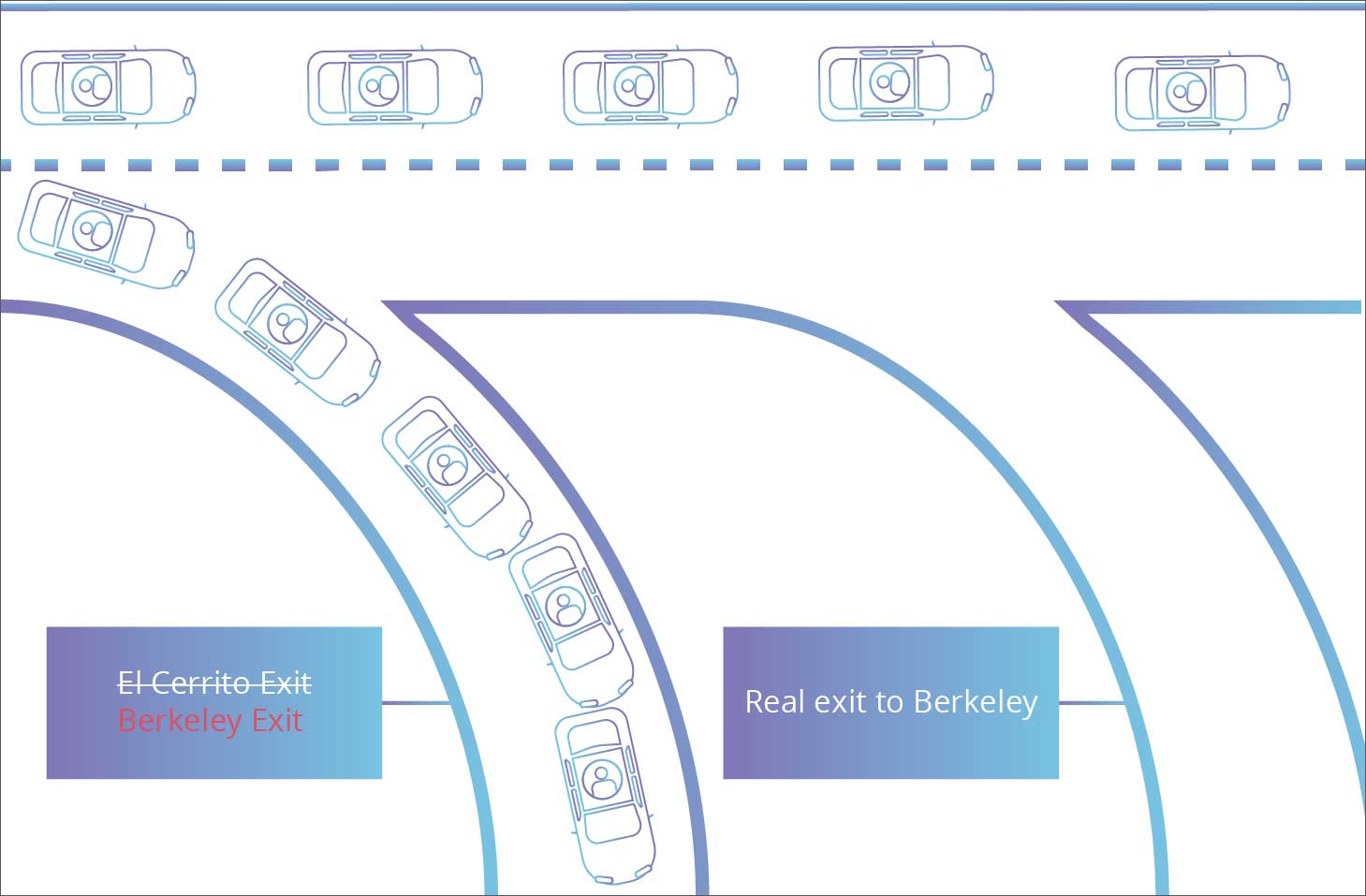 BGP Route leaks or hijacking explained
BGP Route leaks or hijacking explained














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·