BOOK THIS SPACE FOR AD
ARTICLE AD
BleepingComputer can confirm that Garmin has received the decryption key to recover their files encrypted in the WastedLocker Ransomware attack.
On July 23rd, 2020, Garmin suffered a worldwide outage where customers could not access their connected services, including the Garmin Connect, flyGarmin, Strava, inReach solutions.
BleepingComputer was the first to confirm that they suffered a cyberattack by the WastedLocker Ransomware operators after employees shared photos of encrypted workstations, and we found a sample of the ransomware utilized in the attack.
 Photo of encrypted Garmin workstation
Photo of encrypted Garmin workstationEmployees later shared with BleepingComputer that the ransom demand was $10 million.
After a four day outage, Garmin suddenly announced that they were starting to restore services, and it made us suspect that they paid the ransom to receive a decryptor.
Garmin refused, though, to comment any further.
Confirmed: Garmin received a WastedLocker decryption key
Today, BleepingComputer gained access to an executable created by the Garmin IT department to decrypt a workstation and then install a variety of security software on the machine.
WastedLocker is an enterprise-targeting ransomware with no known weaknesses in their encryption algorithm. This lack of flaws means that a decryptor can not be made for free.
To obtain a working decryption key, Garmin must have paid the ransom to the attackers. It is not known how much was paid, but as previously stated, an employee had told BleepingComputer that the original ransom demand was for $10 million
When extracted, this restoration package includes various security software installers, a decryption key, a WastedLocker decryptor, and a script to run them all.
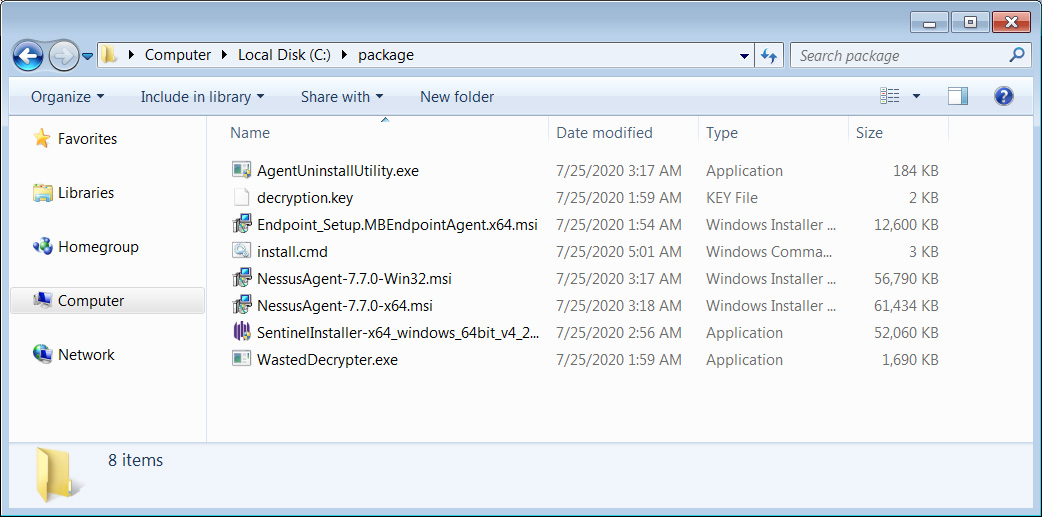 Garmin restoration package contents
Garmin restoration package contentsWhen executed, the restoration package decrypts the computer and then preps the machine with security software.
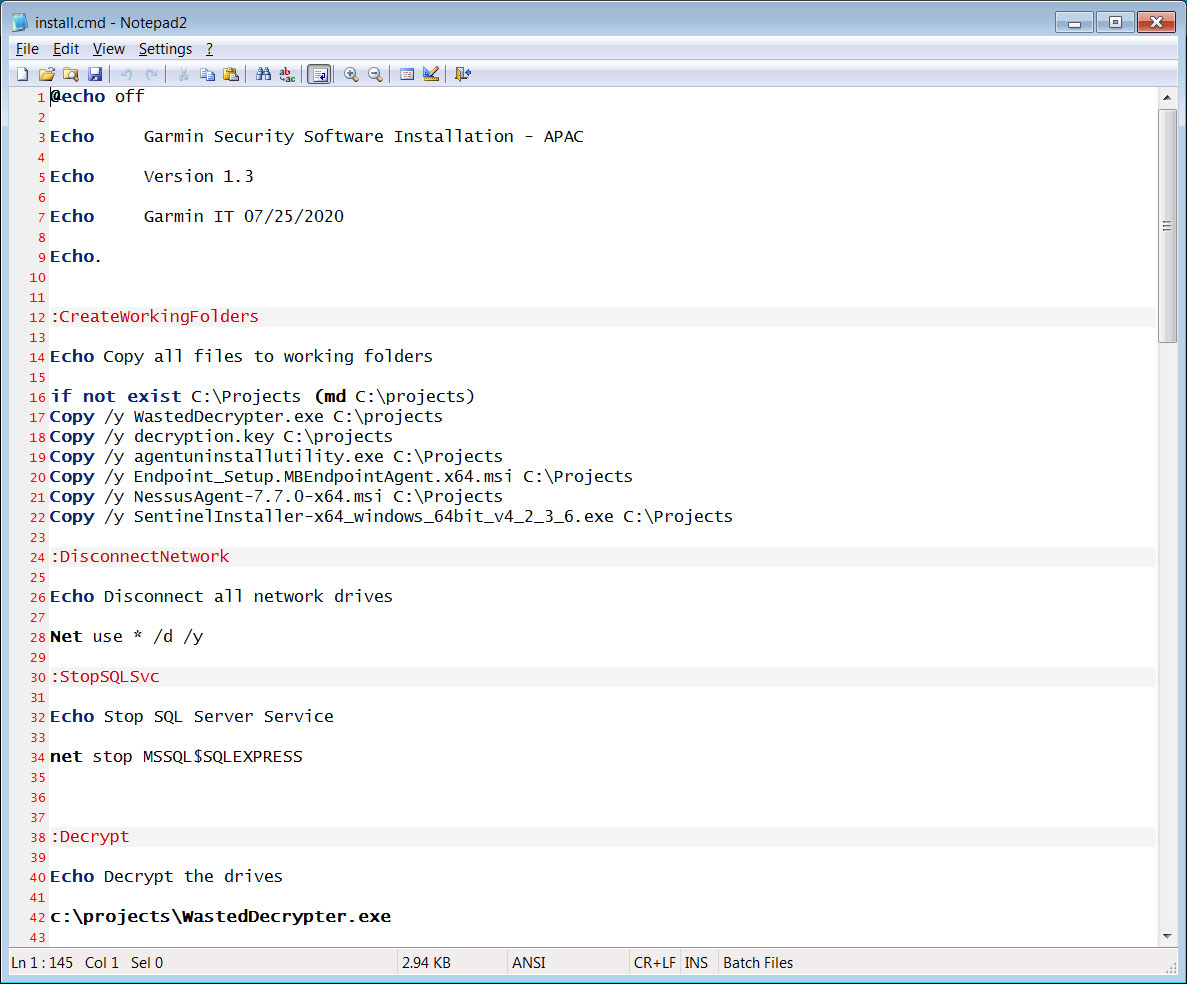 Garmin script to restore a workstation
Garmin script to restore a workstationGarmin's script contains a timestamp of '07/25/2020', which indicates that the ransom was paid either on July 24th or July 25th.
Using the sample of WastedLocker from the Garmin attack, BleepingComputer encrypted a virtual machine and tested the decryptor to see if it would decrypt our files.
In our test, demonstrated in the video below, the decryptor had no problems decrypting our files.
All companies should follow the general rule of wiping all computers and installing a clean image after a ransomware attack. This reinstall is necessary as you never know what the attackers changed during their incursion.
Based on the script above, it does not appear that Garmin is following this guideline and is simply decrypting the workstations and installing security software.
Custom decryptor used
The decryptor enclosed in the package includes references to both cybersecurity firm Emsisoft and ransomware negotiation service firm Coveware.
When BleepingComputer reached out to Coveware, we were told that they do not comment on any ransomware incidents reported in the media.
In a similar response, Emsisoft told us that they could not comment on any cases, but that they create decryption tools and are not involved in ransom payments.
"I cannot comment on specific cases, but generally speaking, Emsisoft has no involvement whatsoever in negotiating or transacting ransom payments. We simply create decryption tools," Brett Callow, a threat analyst at security firm Emsisoft, told BleepingComputer.
Emsisoft commonly makes custom ransomware decryptors when the tools supplied by the threat actors are buggy or if companies are concerned that they may contain backdoors.
"If the ransom has been paid but the attacker-provided decryptor is slow or faulty, we can extract the decryption code and create a custom-built solution that decrypts up to 50 percent faster with less risk of data damage or loss," Emsisoft's ransomware recovery services page states.
As Evil Corp has been attributed as the creator of WastedLocker and was placed on the US sanctions list for using Dridex to cause more than $100 million in financial damages, paying this ransomware could lead to hefty fines from the government.
Due to these sanctions, sources familiar with Coveware have told BleepingComputer that the negotiation company has placed WastedLocker on their restricted list in early July, and are not handling negotiations for related attacks.
Garmin has not responded to our queries at this time.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·