BOOK THIS SPACE FOR AD
ARTICLE AD
A large-scale malware campaign dubbed "StaryDobry" has been targeting gamers worldwide with trojanized versions of cracked games such as Garry's Mod, BeamNG.drive, and Dyson Sphere Program.
These titles are top-rated games with hundreds of thousands of 'overwhelmingly positive' reviews on Steam, making them good targets for malicious activity.
It's worth noting that a laced Beamng mod was reportedly used as the initial access vector for a hack at Disney in June 2024.
According to Kaspersky, the StaryDobry campaign started in late December 2024 and ended on January 27, 2025. It mostly impacted users from Germany, Russia, Brazil, Belarus, and Kazakhstan.
The threat actors uploaded infected game installers onto torrent sites in September 2024, months in advance, and triggered the payloads within the games during the holidays, making detection less likely.
.jpg) StaryDobry campaign timeline
StaryDobry campaign timelineSource: Kaspersky
StaryDobry infection chain
The StaryDobry campaign used a multi-stage infection chain culminating with an XMRig cryptominer infection.
Users downloaded the trojanized game installers from torrent sites, which appeared normal, including the actual game they were promised, plus malicious code.
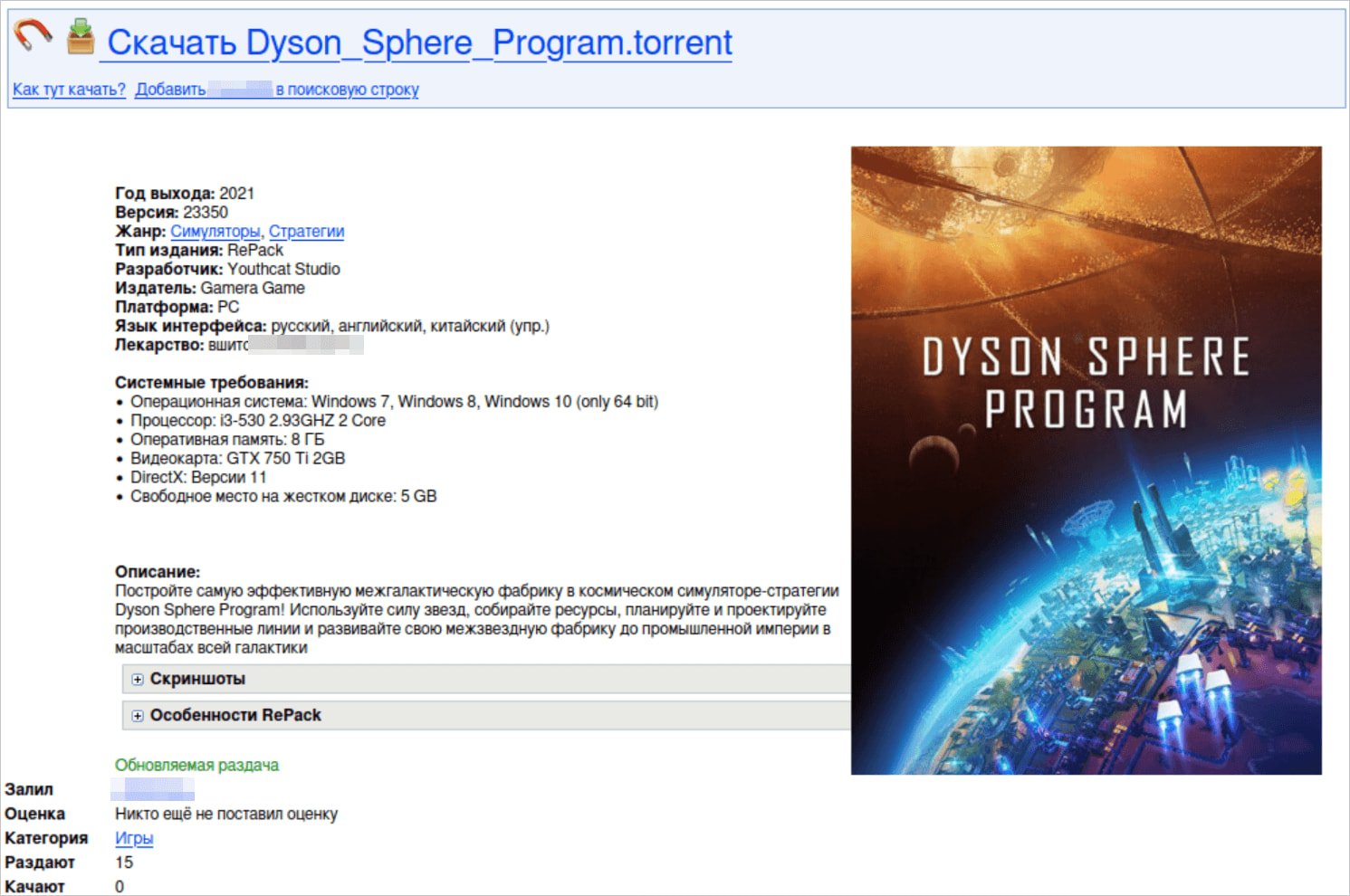 One of the malicious torrents used in the campaign
One of the malicious torrents used in the campaignSource: Kaspersky
During the game's installation, the malware dropper (unrar.dll) is unpacked and launched in the background, and it checks if it's running on a virtual machine, sandbox, or debugger before proceeding.
The malware demonstrates highly evasive behavior, terminating immediately if it detects any security tools, possibly to avoid harming the torrent's reputation.
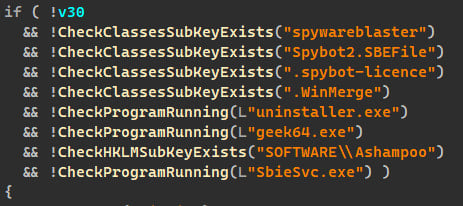 Anti-debug checks
Anti-debug checksSource: Kaspersky
Next, the malware registers itself using 'regsvr32.exe' for persistence and collects detailed system information, including OS version, country, CPU, RAM, and GPU details, and sends it to the command and control (C2) server at pinokino[.]fun.
Eventually, the dropper decrypts and installs the malware loader (MTX64.exe) in a system directory.
The loader poses as a Windows system file, engages in resource spoofing to appear legitimate, and creates a scheduled task to persist between reboots. If the host machine has at least eight CPU cores, it downloads and runs an XMRig miner.
The XMRig miner used in StaryDobry is a modified version of the Monero miner that constructs its configuration internally before execution and does not access arguments.
The miner maintains a separate thread at all times, monitoring for security tools running on the infected machine, and if any process monitoring tools are detected, it shuts itself down.
The XMRig used in these attacks connects to private mining servers instead of public pools, making the proceeds harder to trace.
Kaspersky has not been able to attribute the attacks to any known threat groups but notes that it likely originates from a Russian-speaking actor.
"StaryDobry tends to be a one-shot campaign. To deliver the miner implant, the actors implemented a sophisticated execution chain that exploited users seeking free games," concluded Kaspersky.
"This approach helped the threat actors make the most out of the miner implant by targeting powerful gaming machines capable of sustaining mining activity."
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·