BOOK THIS SPACE FOR AD
ARTICLE AD
Attackers now target a critical severity vulnerability with publicly available exploit code that affects multiple models of end-of-life D-Link network-attached storage (NAS) devices.
Tracked as CVE-2024-10914, the command injection vulnerability was found by security researcher Netsecfish, who also shared exploitation details and said that unauthenticated attackers could exploit it to inject arbitrary shell commands by sending malicious HTTP GET requests to vulnerable NAS devices exposed online.
The affected devices NAS models list includes DNS-320 Version 1.00, DNS-320LW Version 1.01.0914.2012, DNS-325 Version 1.01, Version 1.02, and DNS-340L Version 1.08.
The attacks started after D-Link said on Friday that it wouldn't fix the security flaw because it only impacts end-of-life NAS models, warning customers to retire affected devices or upgrade them to newer products.
"Products that have reached their EOL/EOS no longer receive device software updates and security patches and are no longer supported by D-Link. D-Link US recommends retiring and replacing D-Link devices that have reached EOL/EOS," the company said.
However, as the Shadowserver threat monitoring service discovered, threat actors took notice and started targeting the vulnerability on Monday.
"We have observed D-Link NAS CVE-2024-10914 /cgi-bin/account_mgr.cgi command injection exploitation attempts starting Nov 12th. This vuln affects EOL/EOS devices, which should be removed from the Internet," Shadowserver warned.
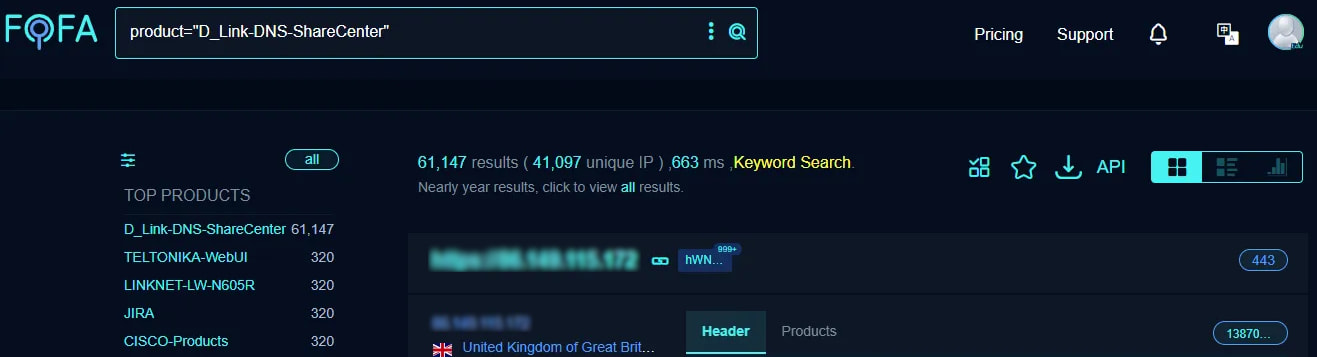 FOFA scan for exposed D-Link NAS devices (Netsecfish)
FOFA scan for exposed D-Link NAS devices (Netsecfish)While Shadowserver said it spotted just over Internet-exposed 1,100 D-Link NAS devices, Netsecfish said it found over 41,000 unique IP addresses online used by vulnerable devices in an Internet scan with Huashun Xin'an's FOFA platform.
In April, Netsecfish also reported a hardcoded backdoor and an arbitrary command injection flaw—impacting almost the same D-Link NAS models and collectively tracked as CVE-2024-3273—that can be chained to execute commands on the device remotely.
As a D-Link spokesperson told BleepingComputer in April, the affected NAS devices do not have automatic updating capabilities or customer outreach features to push alerts. Therefore, those using end-of-life devices are advised to restrict access from the Internet as soon as possible, as they've been targeted in ransomware attacks in the past.
"Typically, D-Link cannot resolve device or firmware issues for these products since all development and customer support have ceased," the company noted on Friday.
"D-Link strongly recommends retiring this product and cautions that further use may be risky to connected devices. If US consumers continue to use these devices against D-Link's recommendation, please ensure the device has the latest firmware."
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·