Cloud infrastructure security company Wiz on Thursday revealed details of a now-fixed Azure Cosmos database vulnerability that could have been potentially exploited to grant any Azure user full admin access to other customers' database instances without any authorization.
The flaw, which grants read, write, and delete privileges, has been dubbed "ChaosDB," with Wiz researchers noting that "the vulnerability has a trivial exploit that doesn't require any previous access to the target environment, and impacts thousands of organizations, including numerous Fortune 500 companies."
Cosmos DB is Microsoft's proprietary NoSQL database that's advertised as "a fully managed service" that "takes database administration off your hands with automatic management, updates and patching."
The Wiz Research Team reported the issue to Microsoft on August 12, after which the Windows maker took steps to mitigate the issue within 48 hours of responsible disclosure, in addition to awarding a $40,000 bounty to the finders on August 17.
"We have no indication that external entities outside the researcher had access to the primary read-write key associated with your Azure Cosmos DB account(s)," Microsoft said in a statement. "In addition, we are not aware of any data access because of this vulnerability. Azure Cosmos DB accounts with a vNET or firewall enabled are protected by additional security mechanisms that prevent risk of unauthorized access."
The exploit identified by Wiz concerns a chain of vulnerabilities in the Jupyter Notebook feature of Cosmos DB, enabling an adversary to obtain the credentials corresponding to the target Cosmos DB account, including the Primary Key, which provides access to the administrative resources for the database account.
"Using these credentials, it is possible to view, modify, and delete data in the target Cosmos DB account via multiple channels," the researchers said. As a consequence, any Cosmos DB asset that has the Jupyter Notebook feature enabled is potentially impacted.
Although Microsoft notified over 30% of Cosmos DB customers about the potential security breach, Wiz expects the actual number to be much higher, given that the vulnerability has been exploitable for months.
"Every Cosmos DB customer should assume they've been exposed," Wiz researchers noted, adding, "we also recommend reviewing all past activity in your Cosmos DB account." Additionally, Microsoft is also urging its customers to regenerate their Cosmos DB Primary Keys to mitigate any risk arising from the flaw.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
347
3 years ago
347 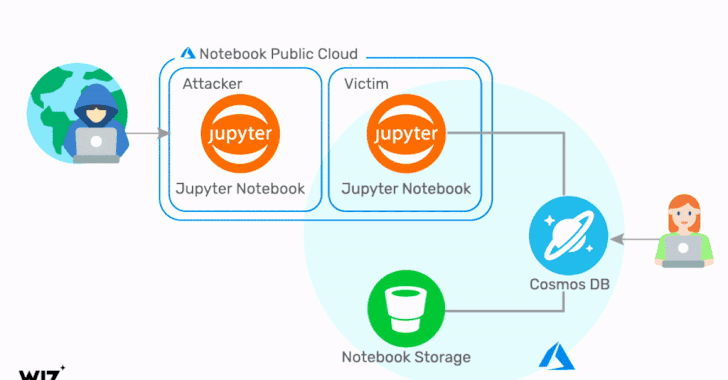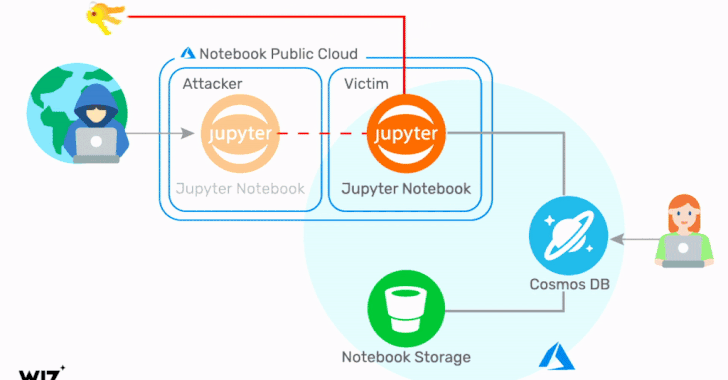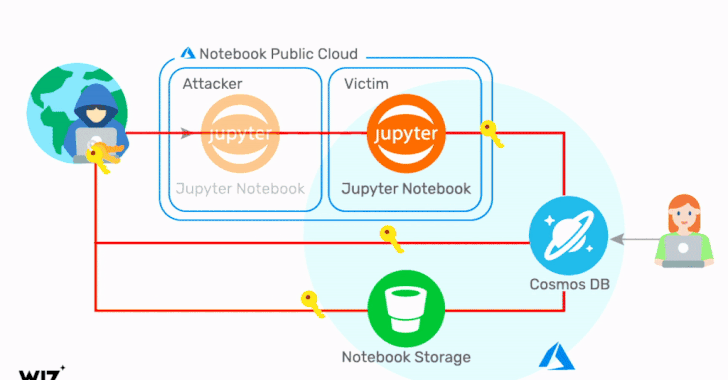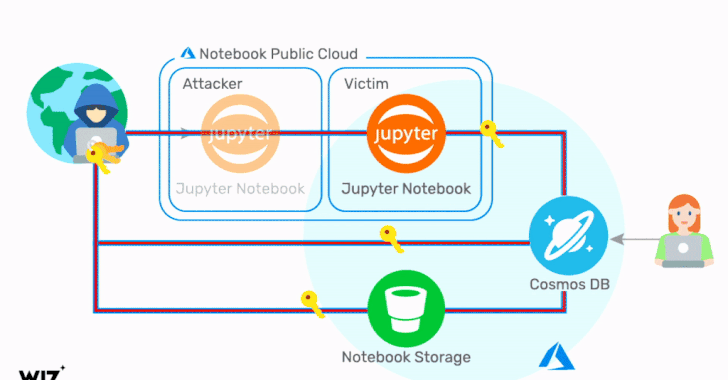

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·