Cybersecurity researchers have found critical security flaws in two popular industrial remote access systems that can be exploited to ban access to industrial production floors, hack into company networks, tamper with data, and even steal sensitive business secrets.
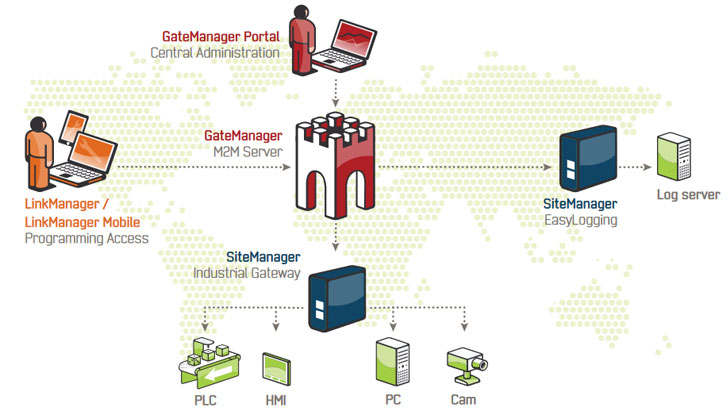
The flaws, discovered by Tel Aviv-based OTORIO, were identified in B&R Automation's SiteManager and GateManager, and MB Connect Line's mbCONNECT24, two of the popular remote maintenance tools used in automotive, energy, oil & gas, metal, and packaging sectors to connect to industrial assets from anywhere across the world.
Six Flaws in B&R Automation's SiteManager and GateManager
According to an advisory published by the US Cybersecurity and infrastructure Security Agency (CISA) on Wednesday, successful exploitation of the B&R Automation vulnerabilities could allow for "arbitrary information disclosure, manipulation, and a denial-of-service condition."
The flaws, ranging from path traversal to improper authentication, impact all versions of SiteManager prior to v9.2.620236042, GateManager 4260, and 9250 before v9.0.20262, and GateManager 8250 prior to v9.2.620236042.
OTORIO's Nikolay Sokolik and Hay Mizrachi found that by exploiting these six vulnerabilities (CVE-2020-11641 through CVE-2020-11646), an authenticated attacker with access to the solution via a general license could view sensitive information about other users, their assets, and their processes, even when they belong to a different organization from that of the adversary.
"This information can be used by attackers to target other organizations and their industrial systems," OTORIO said.
"Additionally, hackers can fool users into malicious foreign sites through fake system messages and alerts. The attacker can also trigger a repeated restart of both the GateManager and the SiteManager, leading eventually to a loss of availability and halt production."
An RCE Flaw in mbCONNECT24
Likewise, mymbCONNECT24 and mbCONNECT24 versions v2.6.1 and prior have been found vulnerable to four different security issues that could make it possible for a logged-in attacker to access arbitrary information via SQL injection, steal session details by carrying out a cross-site request forgery (CSRF) attack with merely a specifically crafted link, and leverage outdated and unused third-party libraries bundled with the software to gain remote code execution.
The RCE vulnerability is the severest of all, with a CVSS score of 9.8 out of a maximum of 10.
Although these flaws have since been fixed, the development is another reminder of how weaknesses in remote access solutions can have destructive consequences on critical infrastructure.
For its part, CISA has recommended minimizing network exposure for all control system devices, in addition to putting control system networks and remote devices behind firewalls, and isolating them from the business network.
"When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available," the agency cautioned. Also, recognize that VPN is only as secure as the connected devices."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 4 years ago
183
4 years ago
183 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·