Researchers have disclosed a previously undocumented local file inclusion (LFI) vulnerability in Hashnode, a developer-oriented blogging platform, that could be abused to access sensitive data such as SSH keys, server's IP address, and other network information.
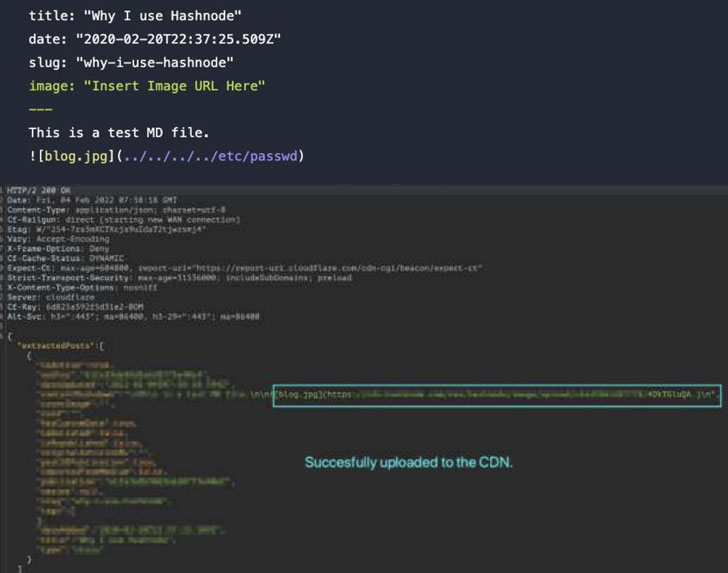
"The LFI originates in a Bulk Markdown Import feature that can be manipulated to provide attackers with unimpeded ability to download local files from Hashnode's server," Akamai researchers said in a report shared with The Hacker News.
Local file inclusion flaws occur when a web application is tricked into exposing or running unapproved files on a server, leading to directory traversal, information disclosure, remote code execution, and cross-site scripting (XSS) attacks.
The flaw, caused due to the web application failing to adequately sanitize the path to a file that's passed as input, could have serious repercussions in that an assailant could navigate to any path on the server and access sensitive information, including the /etc/passwd file that contains a list of users on the server.
Armed with this exploit, the researchers said they were able to identify the IP address and the private secure shell (SSH) key associated with the server.
While the vulnerability has since been addressed, the findings come as Akamai said it recorded more than five billion LFI attacks between September 1, 2021, and February 28, 2022, marking a 141% increase over the previous six months.
"LFI attacks are an attack vector that could cause major damage to an organization, as a threat actor could obtain information about the network for future reconnaissance," the researchers said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
144
2 years ago
144 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·