Cybersecurity agencies in Australia and the U.S. are warning of an actively exploited vulnerability impacting ForgeRock's OpenAM access management solution that could be leveraged to execute arbitrary code on an affected system remotely.
"The [Australian Cyber Security Centre] has observed actors exploiting this vulnerability to compromise multiple hosts and deploy additional malware and tools," the organization said in an alert. ACSC didn't disclose the nature of the attacks, how widespread they are, or the identities of the threat actors exploiting them.
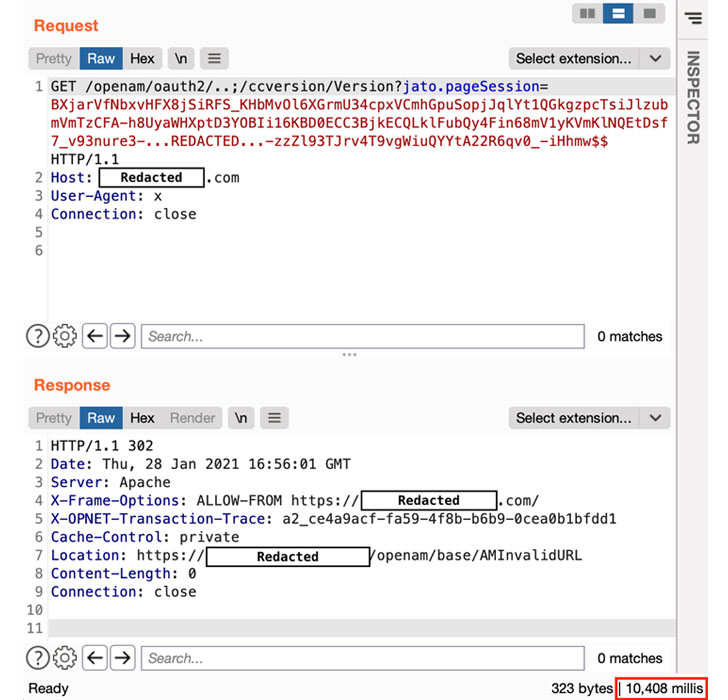
Tracked as CVE-2021-35464, the issue concerns a pre-authentication remote code execution (RCE) vulnerability in ForgeRock Access Manager identity and access management tool, and stems from an unsafe Java deserialization in the Jato framework used by the software.
"An attacker exploiting the vulnerability will execute commands in the context of the current user, not as the root user (unless ForgeRock AM is running as the root user, which is not recommended)," the San Francisco-headquartered software firm noted in an advisory.
"An attacker can use the code execution to extract credentials and certificates, or to gain a further foothold on the host by staging some kind of shell (such as the common implant Cobalt Strike)," it added.
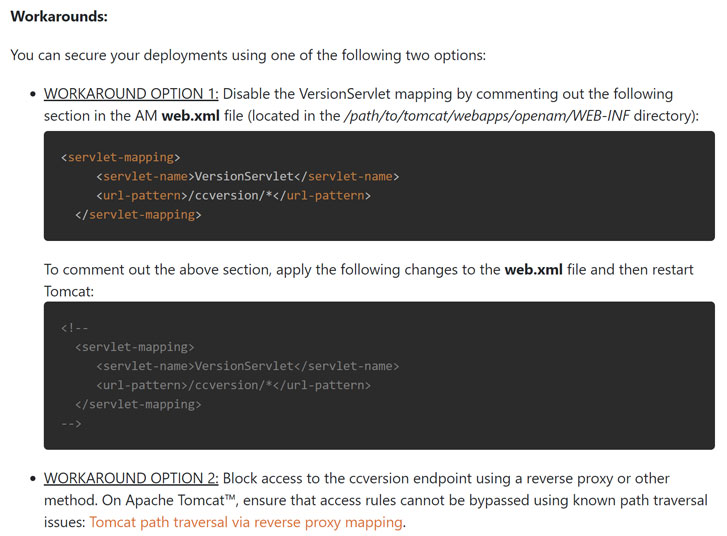
The vulnerability affects versions 6.0.0.x and all versions of 6.5, up to and including 6.5.3, and has been addressed in version AM 7 released on June 29, 2021. ForgeRock customers are advised to move quickly to deploy the patches to mitigate the risk associated with the flaw.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
378
3 years ago
378 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·