BOOK THIS SPACE FOR AD
ARTICLE ADCybersecurity researchers from Mac security provider, Kandji, have discovered a new malware dubbed “Cuckoo” targeting macOS users. The malware is disguised as a music converter app like Spotify and can run on both Intel and ARM-based Apple Mac computers.
Researchers discovered a malicious Mach-O binary on April 24, 2024, exhibiting spyware and infostealer behaviour. Its examination revealed a file titled “DumpMedia Spotify Music Converter,” a universal binary on Intel or ARM-based Mac computers.
The malware was detected when the Spotify version was downloaded from dumpmediacom. Then it was found on other websites with both free and paid versions.
“So far, we have found that the websites tunesolocom, fonedogcom, tunesfuncom, tunefabcom are hosting malicious applications containing the same malware,” Kandji researchers revealed in their blog post.
Cuckoo’s Deceptive Tactics
Cuckoo deceives users by claiming to convert Spotify music to MP3 format. Once installed, it begins the data heist, targeting the macOS keychain, visual evidence, browsing history, messaging app data, cryptocurrency wallet details, and authentication credentials.
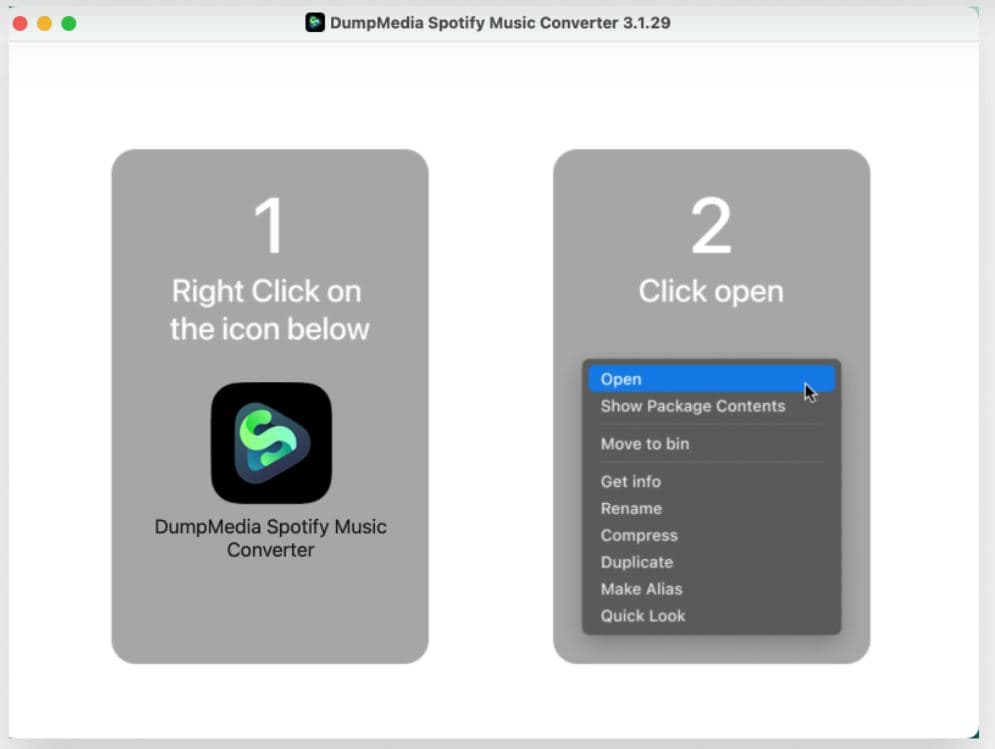
It self-installs by requesting users to open an app, without a vetted signature or developer ID. It checks the user’s location and gathers host hardware information. If the user accepts further prompts, it gains access to the Finder, microphone, and downloads.
What it Targets?
Cuckoo targets macOS’s keychain, a repository for passwords, login credentials, and cryptographic keys, compromising online accounts and sensitive data access.
It steals screenshots, and webcam snapshots, and targets messaging apps like WhatsApp and Telegram, revealing users’ online activities and posing a significant financial threat to digital asset owners.
Researchers found Cuckoo copies files related to Safari, Notes, and Keychain to temporary locations and create paths to files of interest. It runs a launch agent every 60 seconds to maintain persistence on the machine.
Who’s Behind Cuckoo?
The campaign is not explicitly attributed to any particular threat actor, but researchers noted that it spares devices in Armenia, Belarus, Kazakhstan, Russia, and Ukraine.
Moreover, it establishes persistence via LaunchAgent, a feature found in RustBucket, XLoader, JaskaGO, and a backdoor associated with Chinese threat actor ZuRu. The malware was signed with a legitimate Chinese developer ID (Yian Technology Shenzhen Co., Ltd (VRBJ4VRP), with all bundles (except those hosted on fonedogcom) signed.
To protect yourself from Cuckoo and other malware threats, download software cautiously, avoid untrusted sources, scrutinize emails and attachments, and use reliable antivirus and anti-malware solutions. Staying vigilant and maintaining scepticism is crucial for digital privacy and security.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·