BOOK THIS SPACE FOR AD
ARTICLE ADCyberattacks increased 50 percent YoY in 2021 and peaked in December due to a frenzy of Log4j exploits, researchers found.
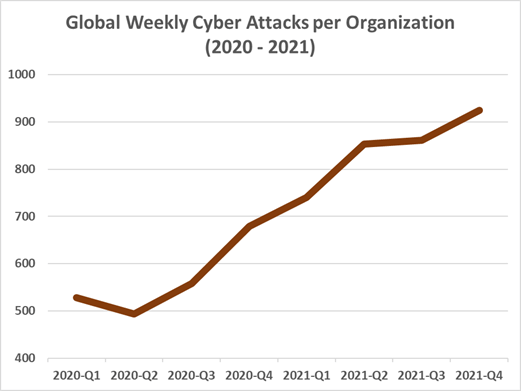
2021 dragged itself to a close under a Log4Shell-induced blitzkrieg. With millions of Log4j-targeted attacks clocking in per hour since the flaw’s discovery last month, there’s been a record-breaking peak of 925 cyberattacks a week per organization, globally.
The number comes out of a Monday report from Check Point Research (CPR), which found Log4Shell attacks to be a major contributor to a 50-percent increase year-over-year in overall attacks per week on corporate networks for 2021.
That said, the year had already been on track to break records even before the easily exploited Log4Shell vulnerabilities in the ubiquitous Java logging library Apache Log4j cropped up, allowing unauthenticated remote code execution (RCE) and complete server takeover — and leading to in-the-wild exploitation within mere hours.

CPR had reported a 40 percent increase as of October, with earlier numbers showing that one out of every 61 organizations worldwide had been hit by ransomware each week.
Education/Research in the Crosshairs
CPR researchers said that education/research was the sector that experienced the highest volume of attacks in 2021, with an average of 1,605 attacks per organization every week: a 75 increase from 2020. A case in point: As of Dec. 30, the advanced persistent threat (APT) Aquatic Panda was targeting universities with Log4Shell exploit tools in an attempt to steal industrial intelligence and military secrets.
The second most picked-on sector was government/military, which saw 1,136 attacks per week: a 47 percent increase. Next up was the communications industry, with 1,079 attacks weekly per organization: a 51 percent increase.
Africa, APAC See Most Attacks
Africa experienced the highest volume of attacks last year, with an average of 1,582 weekly attacks per organization: a 13-percent increase over 2020.
As shown in the chart below, APAC saw a 25 percent increase in weekly attacks per organization, with an average of 1,353 weekly attacks. Latin America, with 1,118 attacks weekly, experienced a 38 percent increase; Europe, with 670 attacks weekly, clocked a 68 percent increase; and North America, with an average of 503 weekly attacks per organization, was under attack 61 percent more than in 2020.
Everything’s a Target, So Secure Everything
CPR’s advice: “In a multi-hybrid environment, where the perimeter is now everywhere, security should be able to protect it all.” Email, web browsing, servers and storage are “merely the basics,” the firm said: a list to which mobile apps, cloud and external storage are also “essential,” as are compliance of connected mobile and endpoint devices, and internet-of-things (IoT) devices.
As well, “workloads, containers and serverless applications on multi- and hybrid-cloud environments should be part of the checklist at all times,” CPR recommended.
Standard-issue security best practices apply: Stay up to date with security patches to stop attacks that leverage known flaws, segment networks, apply strong firewall and IPS safeguards between the network segments in order to contain infections from propagating across the entire network, and educate employees to recognize potential threats.
“Quite often, user awareness can prevent an attack before it occurs,” CPR researchers suggested. “Take the time to educate your users and ensure that if they see something unusual, they report it to your security teams immediately. User education has always been a key element in avoiding malware infections.”
Finally, implement advanced security technologies, CPR said. “There is not a single silver-bullet technology that can protect organizations from all threats and all threat vectors. However, there are many great technologies and ideas available – machine learning, sandboxing, anomaly detection, content disarmament and numerous more.”
CPR recommended two key components to consider: threat extraction (file sanitization) and threat emulation (advanced sandboxing). “Each element provides distinct protection that, when used together, offer a comprehensive solution for protection against unknown malware at the network level and directly on endpoint devices.”
Image courtesy of Pixabay.
Password Reset: On-Demand Event: Fortify 2022 with a password-security strategy built for today’s threats. This Threatpost Security Roundtable, built for infosec professionals, centers on enterprise credential management, the new password basics and mitigating post-credential breaches. Join Darren James, with Specops Software and Roger Grimes, defense evangelist at KnowBe4 and Threatpost host Becky Bracken. Register & stream this FREE session today – sponsored by Specops Software.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·