BOOK THIS SPACE FOR AD
ARTICLE ADA targeted phishing attack takes aim at a major U.S. payments company.
A sophisticated phishing campaign directed at a “major, publicly traded integrated payments solution company located in North America” made use of DocuSign and a compromised third party’s email domain to skate past email security measures, researchers said.
The campaign spread seemingly innocuous emails around the company, with the goal of stealing Microsoft login credentials, researchers at Armorblox revealed.
Attackers Masquerade as DocuSign
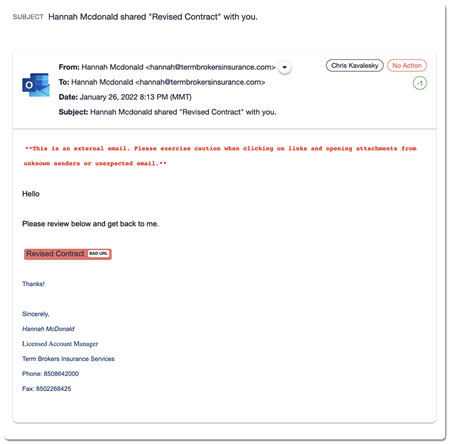
Around 550 members of the targeted company received the same email in their inboxes, researchers told Threatpost. The sender’s name was “Hannah Mcdonald,” and the subject line and the body of the email were quite simple and to the point, as seen below:
Those who clicked the link in the email were presented with a preview of an electronic document through DocuSign, a common e-signature software, according to Armorblox’ Thursday analysis. The preview looked like a legitimate DocuSign landing page, with a prompt to “Please review and sign this document,” and an indication that other parties had already added their signatures.
The preview was hosted on Axure, researchers noted – a valid, cloud-based prototyping portal.
Funnily enough, just like the real thing, the copycat page contained a cybersecurity warning – advising the target to not share access with others – in fine print.
Those who clicked to view the document were presented with a Microsoft single sign-in login page. Any login credentials entered at this stage would’ve ended up with the attackers.
Basic Email Security Fails
The phishing emails successfully evaded traditional email security measures in part because they came from a domain belonging to Term Insurance Brokers. The report noted that “a quick scan of the domain address would not have alerted the end user of fraudulent activity because of the domain’s validity. In the payment industry this domain would have passed most of the custom defined policies, further increasing end users’ chance of falling victim to this sophisticated phishing attack.”
Microsoft’s Spam Confidence Level (SCL) – a measure of the perceived legitimacy of any given email – assigned these malicious emails a score of ‘-1.’ In SCL, -1 is the lowest possible score, allowing a message to skip filtering because it “is from a safe sender, was sent to a safe recipient or is from an email source server on the IP Allow List.”
Impersonating and leveraging trusted cloud services is also an increasingly common tactic to evade email security filters. A benign link sent from a seemingly known and trusted application contains no inherent malicious content, after all.
In the first three months of 2021 alone, researchers found 7 million malicious emails sent from Microsoft 365 and a staggering 45 million sent from Google’s cloud services and infrastructure, Proofpoint reported, adding that cybercriminals have used the likes of Office 365, Azure, OneDrive, SharePoint, G-Suite and Firebase storage to send phishing emails and host attacks.
In an email to Threatpost, Lauryn Cash, product marketing manager at Armorblox, highlighted integrated cloud email security – a cloud- and AI-based method of identifying anomalous emails – as a weapon to support existing email security tools: “Tools that leverage natural language understanding (NLU) can help stop zero-day attacks.” NLU is the ability of a computer to interpret meaning from human language.
The report concluded by recommending that potential targets remain vigilant about basic security hygiene – by not opening emails they’re not expecting, watching for targeted attacks, and using tools like password managers and multi-factor authentication.
Moving to the cloud? Discover emerging cloud-security threats along with solid advice for how to defend your assets with our FREE downloadable eBook, “Cloud Security: The Forecast for 2022.” We explore organizations’ top risks and challenges, best practices for defense, and advice for security success in such a dynamic computing environment, including handy checklists.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·