BOOK THIS SPACE FOR AD
ARTICLE ADThe mobile malware heisted hundreds of millions of dollars from unsuspecting users, thanks to 470 different well-crafted malicious app in Google Play.
Nearly 500 malicious apps lurking on the Google Play Store have successfully installed Dark Herring malware — a cash-stealer intended to add sneaky charges onto mobile carrier bills — on more than 100 million Android devices across the globe.
That’s quite a school of fish.
Dark Herring malware was discovered by a research team with Zimperium, who estimate the amount the campaign has been able to steal totals in the hundreds of millions, in increments of $15 a month per victim. Google has since removed all 470 malicious applications from the Play Store, and the firm said the scam services are down, but any user with one of the apps already installed could still be actively victimized down the road. The apps are still available in third-party app stores too.
Consumers across the world, particularly in under-banked areas, rely on direct carrier billing (DCB) as a mobile payment method, which adds charges for non-telecom services onto a consumer’s monthly phone bill. It’s a juicy target for adversaries.
In this case, the errant $15 charge isn’t necessarily enough for an end user to notice it for several months, but multiplied across more than 100 million accounts, the ill-gotten gains quickly added up, the report explained.
“The download statistics reveal that more than 105 million Android devices had this malware installed, falling victim to this campaign globally, potentially suffering incalculable financial losses,” Zimperium’s report said. “The cybercriminal group behind this campaign has built a stable cash flow of illicit funds from these victims, generating millions in recurring revenue each month, with the total amount stolen potentially well into the hundreds of millions.”
The campaign was first detected back in March of 2020 and ran actively through last November, the report said.
The Zimperium analysts who identified Dark Herring said that the scamware is likely the work of a new group, which uses novel techniques and infrastructure.
Dark Herring’s World Domination
Dark Herring’s triumph was the result of a combination of savvy tactics, the analysts said; namely, the use of geo-targeting to deliver the application in the victim’s native language.
“This social-engineering trick is exceptionally successful and effective as users are generally more comfortable with sharing information to a website in their local language,” the team added. “The campaign is exceptionally versatile, targeting mobile users from 70+ countries by changing the application’s language, and displaying the content according to the current user’s IP address.”
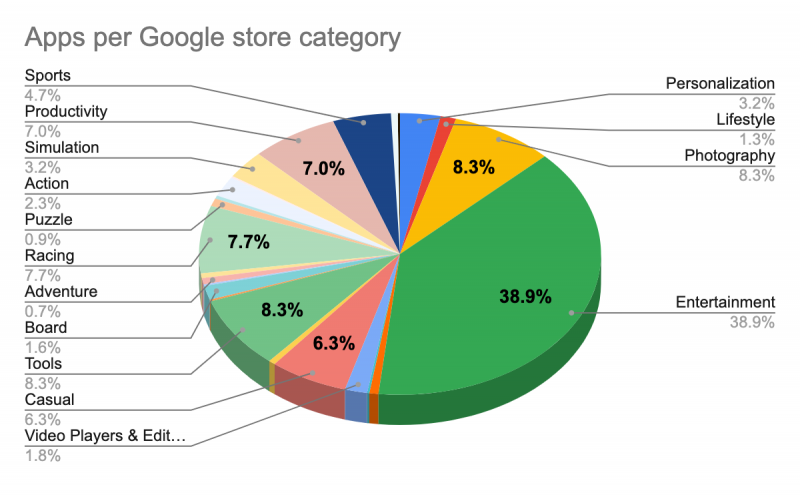
The group behind Dark Herring also managed to stand up 470 high-quality applications that passed official app store muster, which demonstrates that this is a sophisticated operation, analysts noted. The apps all functioned as advertised, and were spread over a wide range of categories.
“Producing a large number of malicious applications and submitting them to app stores points to an extensive, concerted effort by a well-organized group,” the report explained. “These apps are not just clones of each other or other apps, but are uniquely produced at a high rate to deceive traditional security toolsets and the potential victims.”
Besides a robust infrastructure, the Dark Herring’s campaign uses proxies as first-stage URLs to help avoid detection; and thanks to those geo-targeting capabilities, was able to narrow the search for the most prime victims.
For instance, attackers tended to focus on users in countries with less stringent consumer protections for telecommunications users, including Egypt, Finland, India, Pakistan and Sweden, the researchers found.
“Due to the nature of DCB, some countries might have been targeted with less success than others due to the consumer protections set in place by telcos,” the report said.
Between the Gills
On the technical side, once the Android application is installed and launched, a first-stage URL is loaded into a webview, which is hosted on Cloudfront, researchers said. The malware then sends an initial GET request to that URL, which sends back a response containing links to JavaScript files hosted on Amazon Web Services cloud instances.
The application then fetches these resources, which it needs to proceed with the infection process — and specifically, to enable geo-targeting.
“One of the JavaScript files instructs the application to get a unique identifier for the device by making a POST request to the “live/keylookup” API endpoint and then constructing a final-stage URL,” according to the analysis. “The baseurl variable is used to make a POST request that contains unique identifiers created by the application, to identify the device and the language and country details.”
The response from that final-stage URL contains the configuration that the application will use to dictate its behavior, based on the victim’s details. Based on this configuration, a mobile webpage displayed to the victim, asking them to submit their phone number to activate the app (and the DCB charges). This page is customized in terms of the language of the text, flag shown and country code.
Thanks to the steady revenue stream, Dark Herring is a well-funded operation. “The evidence also points to a significant financial investment from the malicious actors in building and maintaining the infrastructure to keep this global scam operating at such a high pace,” the report said.
Given its Dark Herring’s clear achievements, Zimperium said that it seems unlikely this will be the last the cybersecurity community hears from this cybercrime group.
Check out our free upcoming live and on-demand online town halls – unique, dynamic discussions with cybersecurity experts and the Threatpost community.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·