BOOK THIS SPACE FOR AD
ARTICLE ADA DarkHotel phishing campaign breached luxe hotel networks, including Wynn Palace and the Grand Coloane Resort in Macao, a new report says.
An advanced persistent threat (APT) group has been targeting luxury hotels in Macao, China with a spear-phishing campaign aimed at breaching their networks and stealing the sensitive data of high-profile guests staying at resorts, including the Grand Coloane Resort and Wynn Palace.
A threat research report from Trellix “cautiously” identified the South Korean DarkHotel APT group as the culprit behind the attacks.
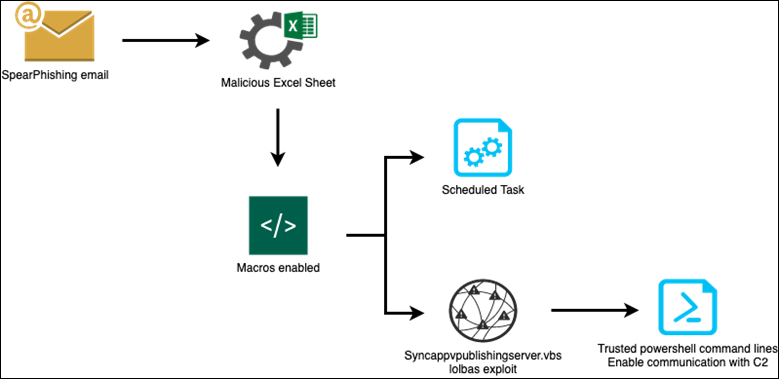
The researchers said the spear-phishing campaign began at the tail end of November, with emails loaded with malicious Excel macros being sent to ranking hotel management with access to hotel networks, including human resources and office managers.
In one attack wave, phishing emails were sent to 17 different hotels on Dec. 7 and faked to look like they were sent from the Macao Government Tourism Office, to gather information about who was staying at the hotels. The emails asked the recipient to open an attached Excel file labeled “passenger inquiry.”
“Please open the attached file with enable content and specify whether the people were staying at the hotel or not?” the malicious email read, according to the threat researchers with Trellix. The communication was signed from the “Inspection Division – MGTO.”
Trellix was able to attribute the attacks to DarkHotel with a “moderate” level of confidence due to the IP address for the command-and-control server (C2), which was previously attached to the group; the targeting of hotels, which DarkHotel is already infamous for; and patterns found in the C2 setup which match known DarkHotel activities, the report said.
“However, we have lowered our confidence level to moderate because the specific IP address remained active for quite some time even after being publicly exposed, and the same IP address is the origin of other malicious content not related to this specific threat,” the Trellix team said. “These two observations have made us more cautious in our attribution.”
DarkHotel Suspected of Stealing Data for Future Attacks
Once opened, the macros contacted the C2 server to begin data exfiltration from the hotel networks, the Trellix team explained.
“The command-and-control server, hxxps://fsm-gov(.)com, used to spread this campaign was trying to impersonate a legitimate government website domain for the Federated States of Micronesia,” Trellix’s report added. “However, the real Micronesia website domain is ‘fsmgov.org.'”
The Trellix team said they suspected the attackers were collecting data to be used later.
“After researching the event agenda for the targeted hotels, we did indeed find multiple conferences that would have been of interest to the threat actor,” the Trellix researchers reported. “For instance, one hotel was hosting an International Environment Forum and an International Trade & Investment Fair, both of which would attract potential espionage targets.”
The spear-phishing campaign stopped on Jan. 18, the team said.
COVID-19 Stalls Campaign
That said, the COVID-19 pandemic cancelled or delayed these events, giving law enforcement time to catch on. By Dec. 2021, the Macao Security Force Bureau received a notification from the Cyber Security Incident Alert and Emergency Response Center of the police department that a domain similar to the official Security Force page was being used to spread malware and “commit illegal acts.”
Besides targeting hotels, other campaigns attributed to the same C2 IP address, believed to be controlled by DarkHotel, included going after MetaMask crypto users with a spoofed Collab.Land phishing page, the Trellix report added.
DarkHotel has a long history of targeting Chinese victims. In April 2020, the APT group went after Chinese virtual private network (VPN) service provider SangFor, used by several Chinese government agencies. By the end of the first week of that month, at least 200 endpoints had been compromised, according to reports.
Around the same time, at the start of the COVID-19 pandemic, DarkHotel targeted the systems of the World Health Organization.
Attacks like these show how attractive data stored in hotel networks can be for threat actors. Hotel operators should recognize that cybersecurity needs to reach beyond their networks’ edge, the Trellix team advised. Travelers likewise need to take appropriate security precautions, Trellix added.
“Only bring the essential devices with limited data, keep security systems up to date and make use of a VPN service when using hotel Wi-Fi,” the report said.
Moving to the cloud? Discover emerging cloud-security threats along with solid advice for how to defend your assets with our FREE downloadable eBook, “Cloud Security: The Forecast for 2022.” We explore organizations’ top risks and challenges, best practices for defense, and advice for security success in such a dynamic computing environment, including handy checklists.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·