BOOK THIS SPACE FOR AD
ARTICLE ADA shadow court system for hackers shows how professional ransomware gangs have become.
Cybercriminals who have worked as affiliates with ransomware group DarkSide, responsible for the Colonial Pipeline attack, are having a tough time getting paid for their work now that the group has had its operations interrupted; so, they’re turning to admins of the group’s Dark Web criminal forum to sort things out in what researchers call a “shady version of the People’s Court.”
Ransomware-as-a-service (RaaS) providers like DarkSide strike arrangements with various other cybercriminals to provide malware for their campaigns in exchange for a percentage of the take — and business is booming. Ransomware attacks have spiked by 350 percent since 2018.
“It should come as no surprise that RaaS groups literally treat their operations as a business – interviewing potential team members, establishing a work agreement and providing the tools to get the job done,” John Hammond, a senior security researcher with Huntress, told Threatpost in an interview. “Cybercrime groups have to be selective and handpick members of their cohorts – they take their work seriously, and obviously it can be a lucrative gig.”
Huntress has been monitoring these cybercriminals and watching them settle disputes among themselves. Specifically, Huntress has observed a growing number of complaints being submitted claiming DarkSide is in breach of the terms of its affiliate program. The claims are being settled among admins in a well-defined “hackers’ courtroom” and payments made by admins out of a DarkSide deposit they control.
The hackers’ court even refers to “plaintiffs” and “defendants,” Hammond added.
Here, a few screenshots from Huntress of the Hackers’ Court show how these issues are settled.
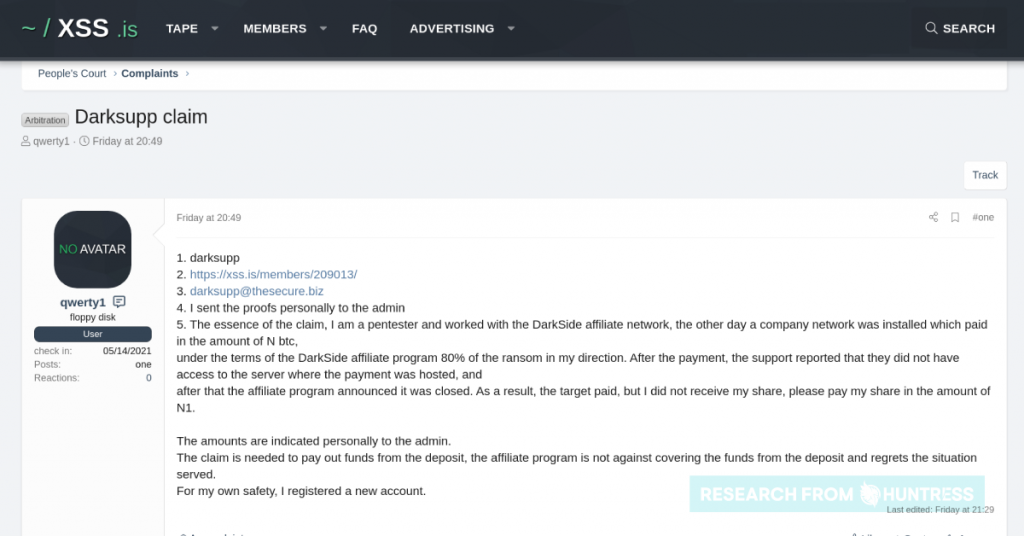
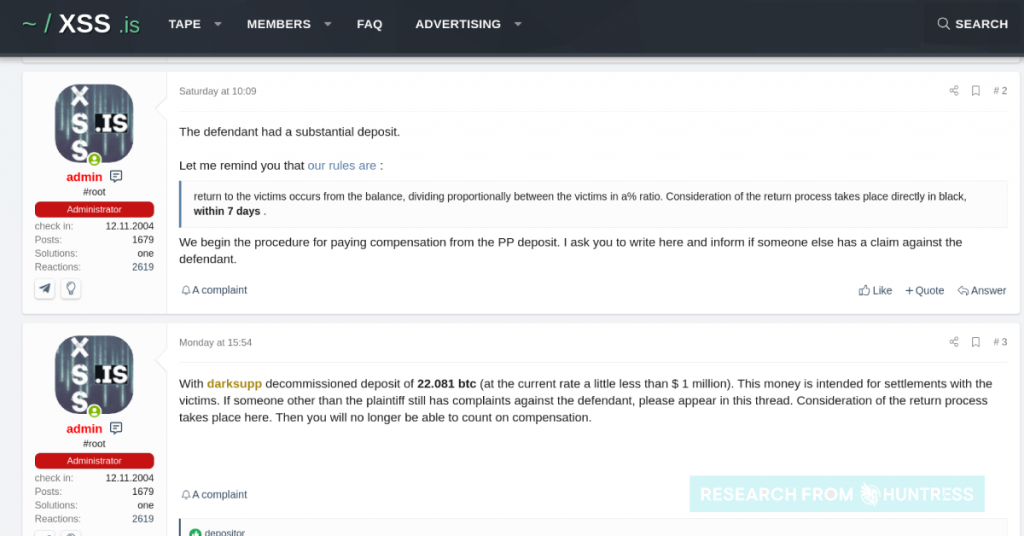

Hackers’ Court In Session
“Cybercrime has matured so much there is a strange ‘People’s Court’ to dispute claims and wrongdoings in the underground syndicate,” Hammond explained. “If a scammer has been scammed, or a business agreement has turned sour, even a hacker can file a claim and have their time in front of a jury. There is no honor among thieves — but there is a “dark side” code of conduct. At least they have some ethical principles — albeit a bit twisted — guiding them.”
These darknet forums have provided RaaS providers with the infrastructure necessary to run mature, professional operations and sell their stolen data to the highest bidder. Ransomware tactics are becoming more potent, too.
Not content with settling for double extortion, where victims are threatened with losing access to their sensitive data, and also with having that data posted publicly, these ransomware gangs have decided to up the ante with triple extortion. That means not only is the victim’s data encrypted and potentially publicly disclosed, but the ransomware operators add a final twist by going after the victim’s customers and partners, demanding payments from them as well.
All of these leaks, in addition to recruitment, stolen data sales and more, are run on these Dark Web forums and overseen by a strict administration structure.
Huntress grabbed images, including the DarkSide forum access page, which references “the latest news” which likely refers to the Colonial Pipeline attack: “We are apolitical, we do not participate in geopolitics, do not need (sic) to tie us with a defined government and look for other our (sic) motives. Our goal is to make money, and not creating problems for society.”
They added a note at the bottom that “From today we [sic] introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
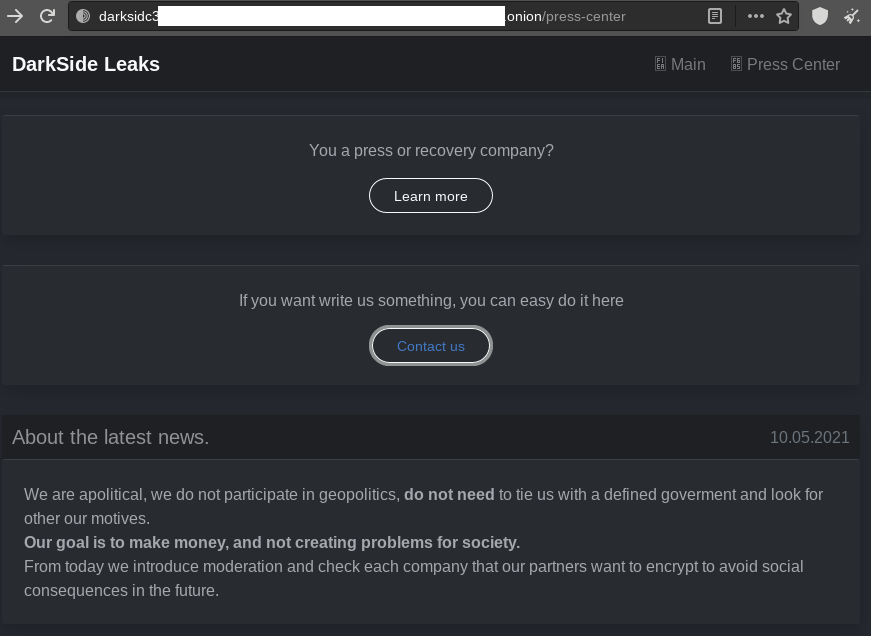
No Mercy, Just Business Savvy, Among RaaS Criminals
“Reading public messages from the DarkSide or other RaaS networks can send a chill down your spine, but it demonstrates how cybercrime has truly become an underground industry,” Hammond explained. “Bad actors may cripple organizations, damage national security or disrupt critical services, but they see this at face value: Nothing more than a job that gets them paid.”
And while these ransomware gangs have shown no mercy to their victims — attacking hospitals, schools and disrupting the lives of everyday people — they have enough business sense to know they need basic mechanisms for recruitment and settling disputes. And in many cases, doing a better job than their legitimate cybersecurity counterparts.
“Every operation that happens in the infosec industry, from marketing and sales to customer service, has a ‘dark side’ counterpart,” Hammond said. “A ‘customer’ comes forward with a ransomware complaint? There are staff members and support queues for that. Want a good deal on getting your stolen information back? Just contact the sales department — they can help. That five-star service experience is something that many legitimate service providers are striving toward to this day.”
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·