BOOK THIS SPACE FOR AD
ARTICLE ADAttacks were way up year-over-year in the second quarter as people continue to work from home.
The number of distributed denial-of-service (DDoS) attacks spiked in the second quarter of 2020, researchers said.
According to the latest Kaspersky quarterly DDoS attacks report, DDoS events were three times more frequent in comparison to the second quarter last year (up 217 percent), and were up 30 percent from the number of DDoS attacks observed in the first quarter of 2020.
The typical annual trend for DDoS is for attacks to spike at the beginning of the year, during the peak season for businesses; while they tend to fall off in late spring and summer. Kaspersky researchers pointed out that the number of attacks in Q2 2019 fell by 39 percent compared to Q1 2019; with a similar trend seen in 2018.
What’s different this year is the obvious: The coronavirus pandemic. Simply put, more people than usual are online for both personal and work-related activities, making for an attractive target for cybercrime of all stripes – and DDoS is no exception.
“Kaspersky experts believe the rise in malicious activity can be attributed to the impact of COVID-19, as both cybercriminals and their targets have had to reconsider their summer plans,” the firm said, in research released on Monday. “The pandemic and subsequent social-distancing restrictions have significantly changed people’s lives and many are either spending their days off in ‘staycation’ mode or have cancelled their scheduled holidays. This change in summer plans has had unexpected consequences, like an increased number of DDoS attacks.”
The average number of attacks per day also increased; the biggest number of attacks per day was almost 300 this quarter (April 9); while in the first quarter, the record was 242 attacks.
Educational and government institutions were targeted the most frequently in the second quarter; however, that said, education-sector attacks decreased sharply starting in the second half of June, which could be attributed to the start of the summer break.
The top three most-attacked geographies were mainland China (65.12 percent), the United States (20.28 percent) and Hong Kong (6.08 percent). Romania dropped out of the top 10 compared to the first quarter, and was ranked the 17th, whereas Great Britain rose from the 18th to the 10th position.
These top three also topped the charts in terms of both the number of targets and the number of attacks: Mainland China came in at 66.02 percent; the United States accounted for 19.32 percent; and Hong Kong (6.34 percent).
Among the other interesting data points, the firm saw that DDoS botnet activity increased on Wednesdays and Thursdays and decreased on Saturdays. And most attacks only lasted about 20 minutes. The longest attacks lasted a few days (215, 214 and 210 hours were the top), which is more than half the number of the first quarter’s longest-lasting attacks (about 19 days).
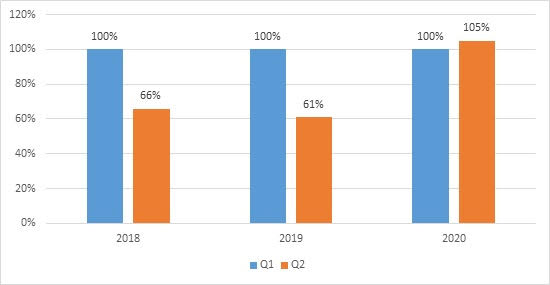
The difference between Q1 and Q2 through 2018-2020. Q1 of each year is taken as 100 percent.
SYN flood remains the main DDoS attack tool (94.7 percent), while ICMP attacks accounted for 4.9 percent – other types of DDoS attacks were rarely seen. However, Kaspersky noted that two new DDoS amplification methods were discovered last quarter.
One is an exploit for a DNS server vulnerability in the DNS delegation process.
“The vulnerability exploitation scheme was dubbed NXNSAttack,” according to the report. “The hacker sends to a legitimate recursive DNS server a request to several subdomains within the authoritative zone of its own malicious DNS server. In response, the malicious server delegates the request to a large number of fake NS servers within the target domain without specifying their IP addresses. As a result, the legitimate DNS server queries all of the suggested subdomains, which leads to traffic growing 1620 times.” The issue is patched in the latest version of DNS server software.
The other amplification method, named RangeAmp, exploits HTTP range requests that allow downloading files in parts. A malicious range request can increase the traffic load on content delivery networks (CDNs) by anywhere between 724 and 43,330 times.
The uptick in cybercrime is continuing as the pandemic drags on. In late July, research findings showed that ransomware attacks are up, particularly in the U.S., where they have more than doubled year-over-year (up 109 percent). Meanwhile, malware targeting IoT devices has risen to 20.2 million, up 50 percent from this time last year – as cybercriminals target the massive influx of employees working from home.
Complimentary Threatpost Webinar: Want to learn more about Confidential Computing and how it can supercharge your cloud security? This webinar “Cloud Security Audit: A Confidential Computing Roundtable” brings top cloud-security experts from Microsoft and Fortanix together to explore how Confidential Computing is a game changer for securing dynamic cloud data and preventing IP exposure. Join us Wednesday Aug. 12 at 2pm ET for this FREE live webinar with Dr. David Thaler, software architect, Microsoft and Dr Richard Searle, security architect, Fortanix – both with the Confidential Computing Consortium. Register Now.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·