BOOK THIS SPACE FOR AD
ARTICLE ADDID promises to give web users more control over their digital identities

The W3C consortium has decided to move forward a specification for Decentralized Identifiers (DID) to W3C Recommendation status, despite objections from several prominent members of the consortium.
While still in its early stages, DID promises to give web users more control over their digital identities.
What are Decentralized Identifiers?
Individuals and organizations rely on identifiers such as phone numbers, email addresses, and usernames on social media. However, most identifiers are issued and controlled by external authorities that decide who or what they refer to and when they can be revoked.
DIDs are a new type of identifier that enable verifiable, decentralized digital identities. DIDs can refer to persons, organizations, things, data models, or abstract entities, as determined by a DID ‘controller’.
RECOMMENDED Lockdown Mode: Apple offers $2m bug bounty for vulnerabilities in new anti-spyware tech
In contrast to typical, federated identifiers, DIDs have been designed so that they may be decoupled from centralized registries, identity providers, and certificate authorities.
“Decentralized Identifiers… are an important foundational component for a new approach to digital identity,” Markus Sabadello, CEO at Danube Tech and co-editor of the W3C DID Core specification, told The Daily Swig.
“Without identifiers, we cannot establish connections or conduct any transactions. We cannot share data and we cannot exchange messages. And without that, we cannot build higher-level concepts such as trust and reputation.
“The technical foundations for digital identity and online interactions must be decentralized. That's what DIDs offer.”
How does DID work?
A DID is identified by a string that includes a URI scheme, the method, and an identifier:
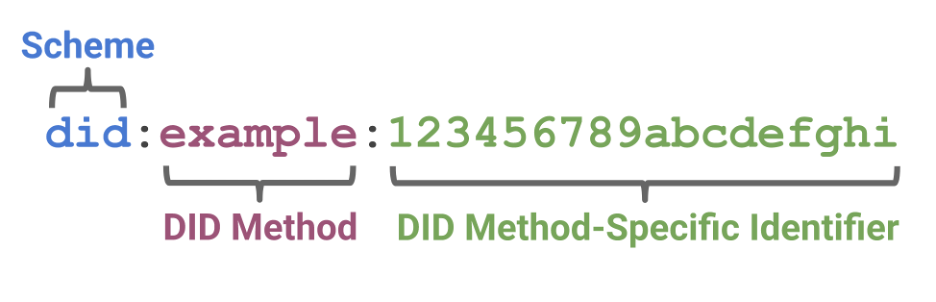 A simple example of a Decentralized Identifier (DID)
A simple example of a Decentralized Identifier (DID)
DID URLs refer to a DID subject and resolve to DID Documents, which contain information associated with the DID, such as cryptographic public keys, services, and interactions.
DIDs can be recorded on verifiable data registries, such as distributed ledgers, decentralized file systems, databases of any kind, and peer-to-peer networks. Finally, a DID controller is the person, organization, device, or service that can modify the DID document.
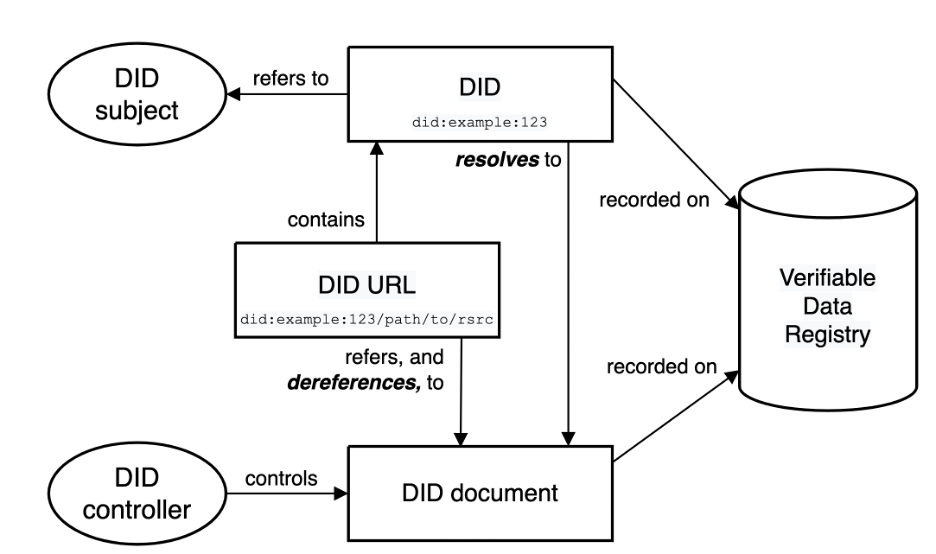 DID architecture
DID architecture
The architecture has been designed for control, privacy, security, interoperability, extensibility, and portability.
Users should own their identity, port it wherever they want, plug it into whatever application they want, and decide which kind of data to share with service providers.
The most common application in conjunction with DIDs is Verifiable Credentials (VCs). These are digital equivalents to your identity-related documents, such as birth certificates, driver’s licenses, social security cards, and any information that is related to you as a person.
Read more of the latest data privacy news
“DIDs enable the creation, management, and usage of this identity information in a way that puts the subject (you) at the center of any interaction,” Sabadello said. “Your personal data is not shared unless you explicitly allow that.”
DID can also be used for information about organizations and physical objects. However, even though VCs are the most common application of DIDs, the real potential of DIDs is much bigger and could involve really any type of online interaction.
“You could send arbitrary text and photo messages to your friends, secured by DIDs. You could build a decentralized social network using DIDs. You could even play a game of chess via DID-based connections,” Sabadello said.
Not a perfect solution
Despite its promises, DID also has its doubters.
“The very concept of a DID I think overcooks the importance of identifiers,” Stephen Wilson, managing director at Lockstep Group, told The Daily Swig. “These are just database pointers or reference numbers. They are almost always assigned, mechanically, by information management systems.”
While user identities have been stolen and abused in different ways, indexing identities differently won’t change anything, Wilson says.
“Especially when DID advocates have not explained how their new BYO technology will be adopted by mainstream services. Even if DIDs (and SSI) was a great idea, the cost of integrating changes to the business is unknown and unaccounted for,” he said.
INTERVIEW Cloudflare CTO John Graham-Cumming envisages a frictionless future for web authentication tests
Wilson also warns that with regards to surveillance capitalism, the smartest data scientists in the world are working out how to mine our digital activities and extract subtle valuable clues.
“They will continue to track us no matter how we choose to identify ourselves,” he said.
The deepest problem with DIDs, Wilson says, is that they don’t do anything to touch the credential side of things.
“The world has shifted focus from WHO you are to WHAT you are,” he said. “Even if a DID provided some radical new way to assert WHO I am, so what? The counterparties I deal with variously want me to prove my driver’s license, my age, my qualifications, my affiliations, my Covid status, etc.”
All those documents are provided and ascertained by third parties. Even if you’ll be able to carry digital proofs of your identity in a wallet and use them private, peer-to-peer, and decentralized fashion, the underlying authority that underpins the credentials remains centralized.
“So, a DID might be owned by the user, self-published, un-censorable, whatever, but all the credentials stay the same – administered by external authorities,” Wilson said.
Disagreements in the community
On June 30, the W3C voted in favor of advancing the DID core specification to W3C Recommendation status. The decision was met with objections by several members, including Mozilla and Google.
“DID-core is only useful with the use of ‘DID methods’, which need their own specifications,” Google wrote. “It’s impossible to review the impact of the core DID specification on the Web without concurrently reviewing the methods it’s going to be used with.”
Mozilla’s objection states: “The DID Core spec has not demonstrated any degree of practical interoperability, instead delegating that to a registry of 50+ methods.”
“[The members who issued objections] provided several arguments for the objections, including concerns about interoperability, centralization, and the use of blockchains,” Sabadello said.
“The overwhelming opinion of the community working on DIDs was that those concerns were largely unjustified. Some community members might go as far as describing this as a strategic move by powerful corporations to prevent or at least slow down the success of technologies that could hurt their traditional business models which are based on centralized technology and control.”
The W3C decision, declared by Ralph Swick, for Tim Berners-Lee, states that the core specification does not lack proof of implementability.
“The histories of many Internet standards show that future work can – and often does – lead to improvements to an initial standard,” the W3C statement reads. “This is a feature, not a flaw. It is ultimately a judgment call of the community as to how long a technology must be deployed before the community updates a standard.”
Next steps for DID
According to the W3C, the Working Group will next address and deliver the proposed standard DID method(s) and demonstrate interoperable implementations. This will be an opportunity to verify the objections raised during the decision.
DIDs are a foundational part of a larger ecosystem, Sabadello says. Many other technical building blocks are related to DIDs, such as Verifiable Credentials (VCs), OpenID Connect 4 Verifiable Credentials, and DIDComm.
“With the approval of the DID standard, those other building blocks can be implemented and deployed with confidence,” he said, adding that major projects with strong political and corporate support are now underway, such as the European Self-Sovereign Identity Framework (ESSIF).
“This means that in the next few years, digital identity applications and services will become available to millions (or even billions) of people, and increase their levels of freedom and protection in the digital lives,” he said.
YOU MIGHT ALSO LIKE Attackers can use ‘Scroll to Text Fragment’ web browser feature to steal data – research
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·