Cybersecurity researchers disclosed details about 13 vulnerabilities in the Nagios network monitoring application that could be abused by an adversary to hijack the infrastructure without any operator intervention.
"In a telco setting, where a telco is monitoring thousands of sites, if a customer site is fully compromised, an attacker can use the vulnerabilities to compromise the telco, and then every other monitored customer site," Adi Ashkenazy, CEO of Australian cybersecurity firm Skylight Cyber, told The Hacker News via email.
Nagios is an open-source IT infrastructure tool analogous to SolarWinds Network Performance Monitor (NPM) that offers monitoring and alerting services for servers, network cards, applications, and services.
The issues, which consist of a mix of authenticated remote code execution (RCE) and privilege escalation flaws, were discovered and reported to Nagios in October 2020, following which they were remediated in November.
Chief among them is CVE-2020-28648 (CVSS score: 8.8), which concerns an improper input validation in the Auto-Discovery component of Nagios XI that the researchers used as a jumping-off point to trigger an exploit chain that strings together a total of five vulnerabilities to achieve a "powerful upstream attack."
"Namely, if we, as attackers, compromise a customer site that is being monitored using a Nagios XI server, we can compromise the telecommunications company's management server and every other customer that is being monitored," the researchers said in a write-up published last week.
Put differently; the attack scenario works by targeting a Nagios XI server at the customer site, using CVE-2020-28648 and CVE-2020-28910 to gain RCE and elevate privileges to "root." With the server now effectively compromised, the adversary can then send tainted data to the upstream Nagios Fusion server that's used to provide centralized infrastructure-wide visibility by periodically polling the Nagios XI servers.
"By tainting data returned from the XI server under our control we can trigger Cross-Site Scripting [CVE-2020-28903] and execute JavaScript code in the context of a Fusion user," Skylight Cyber researcher Samir Ghanem said.
The next phase of the attack leverages this ability to run arbitrary JavaScript code on the Fusion server to obtain RCE (CVE-2020-28905) and subsequently elevate permissions (CVE-2020-28902) to seize control of the Fusion server and, ultimately, break into XI servers located at other customer sites.
The researchers have also published a PHP-based post-exploitation tool called SoyGun that chains the vulnerabilities together and "allows an attacker with Nagios XI user's credentials and HTTP access to the Nagios XI server to take full control of a Nagios Fusion deployment."
A summary of the 13 vulnerabilities is listed below -
CVE-2020-28648 - Nagios XI authenticated remote code execution (from the context of a low-privileged user) CVE-2020-28900 - Nagios Fusion and XI privilege escalation from nagios to root via upgrade_to_latest.sh CVE-2020-28901 - Nagios Fusion privilege escalation from apache to nagios via command injection on component_dir parameter in cmd_subsys.php CVE-2020-28902 - Nagios Fusion privilege escalation from apache to nagios via command injection on timezone parameter in cmd_subsys.php CVE-2020-28903 - XSS in Nagios XI when an attacker has control over a fused server CVE-2020-28904 - Nagios Fusion privilege escalation from apache to nagios via the installation of malicious components CVE-2020-28905 - Nagios Fusion authenticated remote code execution (from the context of low-privileges user) CVE-2020-28906 - Nagios Fusion and XI privilege escalation from nagios to root via modification of fusion-sys.cfg / xi-sys.cfg CVE-2020-28907 - Nagios Fusion privilege escalation from apache to root via upgrade_to_latest.sh and modification of proxy config CVE-2020-28908 - Nagios Fusion privilege escalation from apache to nagios via command injection (caused by poor sanitization) in cmd_subsys.php CVE-2020-28909 - Nagios Fusion privilege escalation from nagios to root via modification of scripts that can execute as sudo CVE-2020-28910 - Nagios XI getprofile.sh privilege escalation CVE-2020-28911 - Nagios Fusion information disclosure: Lower privileged user can authenticate to fused server when credentials are storedWith SolarWinds falling victim to a major supply chain attack last year, targeting a network monitoring platform like Nagios could enable a malicious actor to orchestrate intrusions into corporate networks, laterally expand their access across the IT network, and become an entry point for more sophisticated threats.
"The amount of effort that was required to find these vulnerabilities and exploit them is negligible in the context of sophisticated attackers, and specifically nation-states," Ghanem said.
"If we could do it as a quick side project, imagine how simple this is for people who dedicate their whole time to develop these types of exploits. Compound that with the number of libraries, tools and vendors that are present and can be leveraged in a modern network, and we have a major issue on our hands."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
322
3 years ago
322 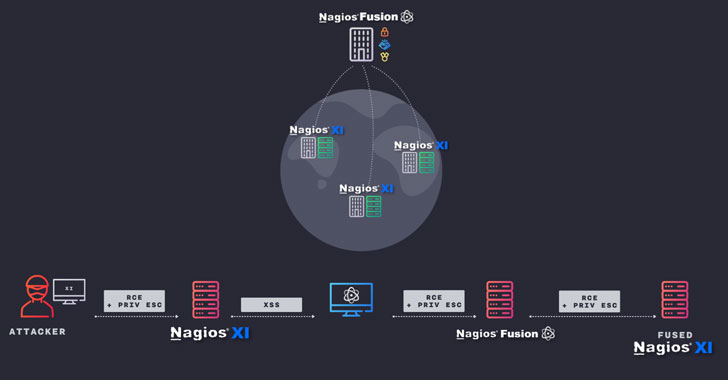
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·