If you're administrating Windows Server, make sure it's up to date with all recent patches issued by Microsoft, especially the one that fixes a recently patched critical vulnerability that could allow unauthenticated attackers to compromise the domain controller.
Dubbed 'Zerologon' (CVE-2020-1472) and discovered by Tom Tervoort of Secura, the privilege escalation vulnerability exists due to the insecure usage of AES-CFB8 encryption for Netlogon sessions, allowing remote attackers to establish a connection to the targeted domain controller over Netlogon Remote Protocol (MS-NRPC).
"The attack utilizes flaws in an authentication protocol that validates the authenticity and identity of a domain-joined computer to the Domain Controller. Due to the incorrect use of an AES mode of operation, it is possible to spoof the identity of any computer account (including that of the DC itself) and set an empty password for that account in the domain," researchers at cybersecurity firm Cynet explain in a blog post.
Though the vulnerability, with a CVSS score of 10.0, was first disclosed to the public when Microsoft released a patch for it in August, it became a matter of sudden concern after researchers published technical details and proof-of-concept of the flaw last week.
Along with Indian and Australian Government agencies, the United States Cybersecurity and Infrastructure Security Agency (CISA) also issued an emergency directive instructing federal agencies to patch Zerologon flaws on Windows Servers immediately.
"By sending a number of Netlogon messages in which various fields are filled with zeroes, an unauthenticated attacker could change the computer password of the domain controller that is stored in the AD. This can then be used to obtain domain admin credentials and then restore the original DC password," the advisories say.
According to Secura, the said flaw can be exploited in the following sequence:
Spoofing the client credential Disabling RPC Signing and Sealing Spoofing a call Changing Computer's AD Password Changing Domain Admin Password"CISA has determined that this vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action."
"If affected domain controllers cannot be updated, ensure they are removed from the network," CISA advised.
Moreover, Samba—an implementation of SMB networking protocol for Linux systems—versions 4.7 and below are also vulnerable to the Zerologon flaw. Now, a patch update for this software has also been issued.
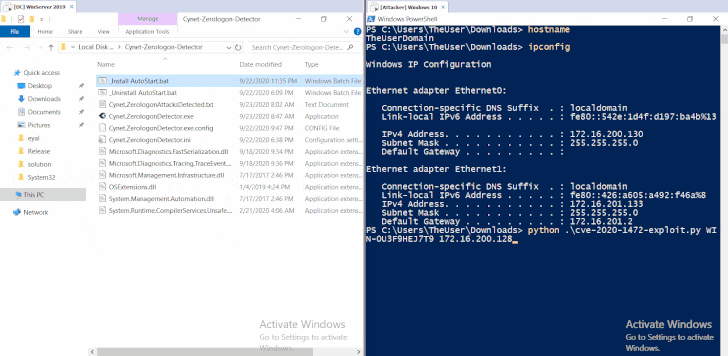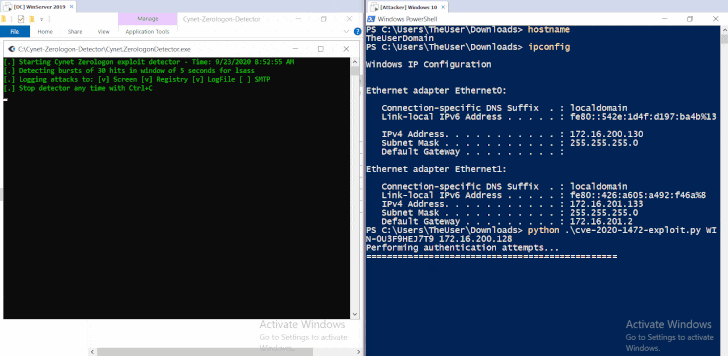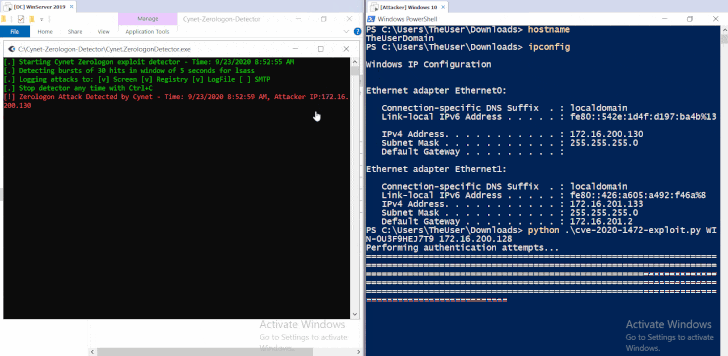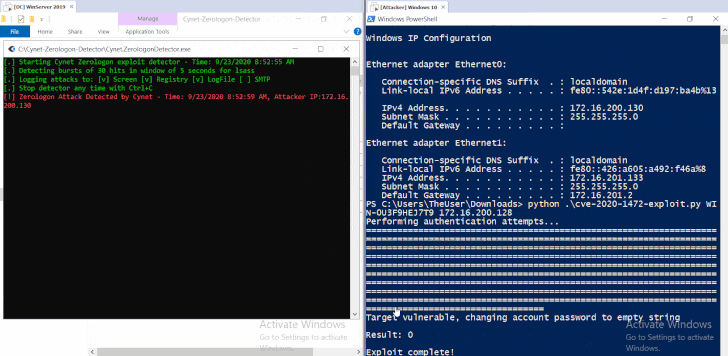
Besides explaining the root cause of the issue, Cynet also released details for some critical artifacts that can be used to detect active exploitation of the vulnerability, including a specific memory pattern in lsass.exe memory and an abnormal spike in traffic between lsass.exe.
"The most documented artifact is Windows Event ID 4742 'A computer account was changed', often combined with Windows Event ID 4672 'Special privileges assigned to new logon'."
To let Windows Server users quickly detect related attacks, experts also released the YARA rule that can detect attacks that occurred prior to its deployment, whereas for realtime monitoring is a simple tool is also available for download.
However, to completely patch the issue, users still recommend installing the latest software update from Microsoft as soon as possible.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 4 years ago
191
4 years ago
191 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·