BOOK THIS SPACE FOR AD
ARTICLE ADDOJ charges six Russian nationals for their alleged part in the NotPetya, Ukraine power grid and Olympics cyberattacks.
The Department of Justice (DOJ) on Monday announced charges against six Russian nationals who are allegedly tied to the Sandworm APT. The threat group is believed to have launched several high-profile cyberattacks over the past few years – including the destructive NotPetya cyberattack that targeted hundreds of firms and hospitals worldwide in 2017.
According to the DOJ complaint, the six Russian nationals are tied to a division of the Russian military intelligence service and also affiliated with the APT Sandworm, also known as TeleBots. The DOJ said cyberattacks linked to the six defendants were “breathtaking” in their scope and “harmed ordinary people around the world,” said Scott Brady, U.S. attorney with the Western District of Pennsylvania, in a DOJ press conference on Monday.
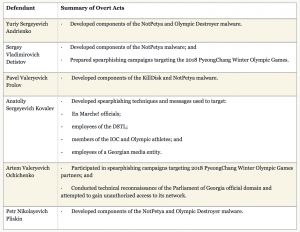
The six defendants are: Yuriy Sergeyevich Andrienko (32); Sergey Vladimirovich Detistov (35); Pavel Valeryevich Frolov (28); Anatoliy Sergeyevich Kovalev (29); Artem Valeryevich Ochichenko (27) and Petr Nikolayevich Pliskin (32).
Each were charged in seven counts: conspiracy to conduct computer fraud and abuse, conspiracy to commit wire fraud, wire fraud, damaging protected computers, and aggravated identity theft, according to the DOJ.
According to the DOJ, the alleged malicious activity of the six dates back to November 2015, with the group developing malware known as BlackEnergy, Industroyer and KillDisk. The group used the malware in attacks against Ukraine’s electric power grid, Ministry of Finance, and State Treasury Service from Dec. 2015 to Dec. 2016, according to the DOJ.
In April and May 2017 the group allegedly launched spearphishing campaigns targeting French President Macron’s “La République En Marche!” (En Marche!) political party prior to the 2017 French elections.
They were also allegedly behind the June 2017 destructive malware attacks that infected computers worldwide, using the NotPetya malware, resulting in the infection of 400 computers. The malware crippled many critical systems, including mission critical systems used by hospitals like the Pennsylvania-based Heritage Valley Health Systems.
In February 2018, the group allegedly sent spearphishing campaigns and malicious mobile applications targeting South Korean citizens and officials, Olympic athletes, partners, and visitors, and International Olympic Committee (IOC) officials; they then allegedly compromised computers supporting the 2018 PyeongChang Winter Olympic Games. This led to the Feb. 9, 2018, destructive malware attack against the opening ceremony, using malware known as Olympic Destroyer.
Finally, the group is alleged to have sent spearphishing emails to government organizations investigating the poisoning of a former GRU officer and his daughter in the United Kingdom in April 2018; and to have targeted the country of Georgia in 2018 with a spearphishing attack that led to the defacement of 15,000 websites.
“Groups like this use tactics, such as spearphishing, that are just as likely to reach targets on both computers, smartphones, or tablets,” Hank Schless, Senior Manager, Security Solutions at Lookout, told Threatpost. “They know that the likelihood of a successful phishing attack increases dramatically if the target receives it on a mobile device. They can phish login credentials from particular users that would allow them to get into the corporate infrastructure, then move laterally around the infrastructure for surveillance purposes or to exfiltrate valuable data.”
Threat researchers applauded the crackdown, saying that, while the arrest and extraction of the six Russian nationals seems unlikely, the indictments will limit their ability to use the Western financial system or travel to any country that may have an extradition agreement with the US.
“The charges filed against Sandworm represent not only the first criminal charges against Sandworm for its most destructive attacks but the first time that most of the charged threat actors have been publicly identified as members of the cybercriminal group,” Kacey Clark, Threat Researcher at Digital Shadows, told Threatpost. “They also represent Sandworm’s first global law enforcement reaction to their deployment of the NotPetya ransomware that has crippled networks worldwide.”
Google’s Threat Analysis Group (TAG), Cisco’s Talos Intelligence Group, Facebook and Twitter were credited in helping the DOJ with its investigation.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·