BOOK THIS SPACE FOR AD
ARTICLE AD
Quickly Find Dom-Based Vulnerabilities with Burp Suite’s Dom Invader
A DOM-Based XSS executes the malicious JavaScript in Browser’s DOM rather than from the page’s HTML Response.
Find Dom-Bases XSS issues in 6 Steps using Dom Invader
1. Enable DOM Invader in Burp’s embedded browser
Open Burp Suite and from the Proxy tab, open Burp’s embedded browser and enable DOM Invader from the extension settings.


2. Update Canary (keyword used to identify DOM XSS)
A canary is a unique string that can be injected into a source and then searched for in various sinks. Default Canary is burpdomxss. You can update it to any other string such as hacksheetsdomxss. Click on Update canary and then click Reload.
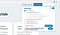
3. Open Augmented DOM Tab in the DevTools (ctrl+shift+i)

4. Open target URL and inject Canary( hacksheetsdomxss ) into parameters
For this example tutorial, we are using Portswigger’s test lab at http://portswigger-labs.net/dom-invader/testcases/augmented-dom-document-write/
Click on Test to start testing for DOM XSS.

- Inject canary (hacksheetsdomxss) into the query parameter “x”

5. Check if Canary is returned in Sink in Augmented DOM Tab
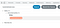
6. Check the Stack Trace in DevTools Console to find where the Canary is getting executed
Click on the Stack Trace link (at Object.oEEBt….)

Open the Console tab in DevTools to view StackTrace details and click on the link to get the exact location of XSS execution


- Enter XSS payload in the parameter “x” to execute it.

Summary CheatSheet

.png)
 3 years ago
491
3 years ago
491 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·