BOOK THIS SPACE FOR AD
ARTICLE ADBeware of phishing and malspam scams targeting your Software-as-a-Service (SaaS) logins! Cybercriminals are using fake Dropbox emails to steal login credentials. Learn how to protect yourself from this new attack and keep your data safe.
Cybersecurity firm Darktrace is warning users about a notorious new phishing and Malspam campaign targeting customers of popular Software-as-a-Service (SaaS) platforms by exploiting Dropbox emails.
Cambridge, UK-based cybersecurity firm Darktrace’s latest research reveals a new Dropbox phishing attack successfully bypassing MFA (multi-factor authentication) protocols. This exploit aims to trick users into downloading malware and exposing their login credentials.
It’s been observed that attackers send seemingly harmless emails originating from a legitimate Dropbox address, containing a malicious link. On January 25, 2024, researchers detected a suspicious email sent to 16 internal users of the Darktrace SaaS environment, originating from a legitimate email address- ‘no-reply@dropboxcom’.
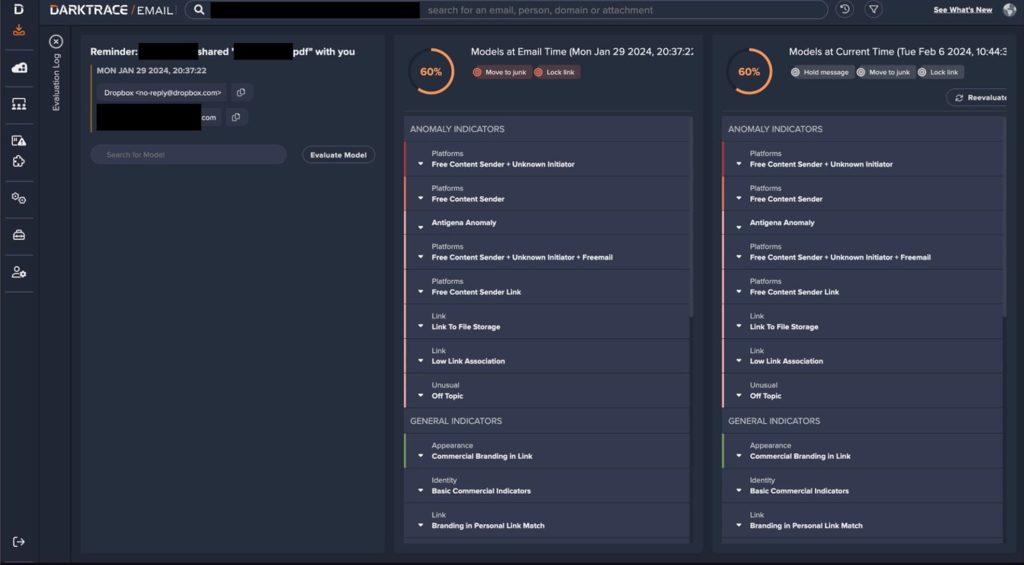 Screenshot credit: Darktrace
Screenshot credit: Darktrace
The email contained a link to a PDF file hosted on Dropbox, possibly named after a Dropbox partner organization. The PDF file contained a suspicious link to a domain named ‘mmv-securitytop.’ Darktace’s email security tool detected and held the email, but a user received another email from a legitimate no-reply@dropboxcom on January 29, requesting to open the previously shared PDF file.
“Darktrace/Email moved the email to the user’s junk file and applied a lock link action to prevent the user from directly following a potentially malicious link,” but couldn’t prevent the damage because an employee clicked on the link.
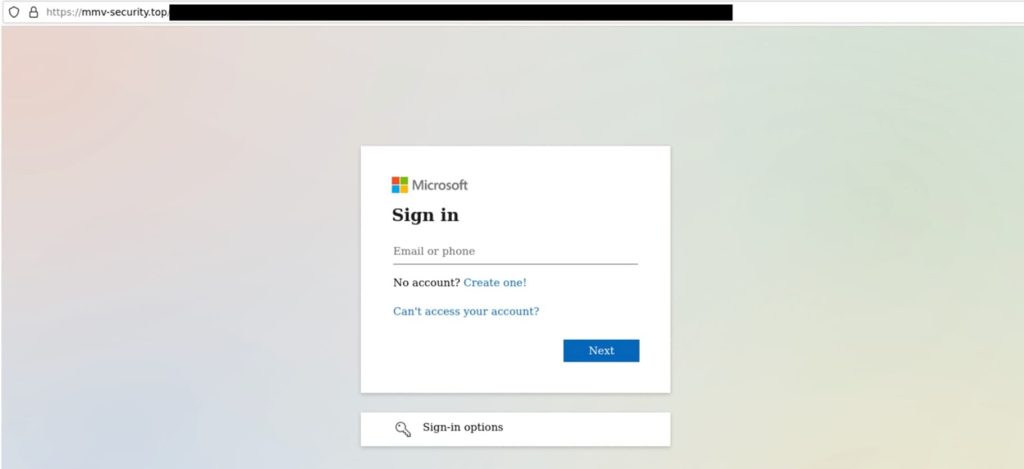
Next, the user’s device got connected to a malicious endpoint, ‘mmv-securitytop’, leading to a fake Microsoft 365 login page. These credential harvesters, disguised as trusted organizations like Microsoft, increase the likelihood of stealing privileged SaaS account credentials.
Since January 31, Darktrace observed suspicious SaaS activity, including logins from unusual locations and endpoints associated with ExpressVPN, suggesting threat actors are using a VPN to mask their true location.
An interesting finding was that threat actors bypassed a customer’s MFA policy using valid tokens and meeting authentication requirements. An additional login was observed from 87.117.225155, using the HideMyAss VPN service.
According to Darktrace’s blog post, the actor created a new email rule, ‘….’, to move emails to the ‘Conversation History’ mailbox folder, a tactic used by threat actors during phishing campaigns. This generic name helps maintain undetected activity on target networks.
Dropbox exploitation is gaining popularity among threat actors, as it is difficult to detect foul play because emails are sent from legitimate addresses. In September 2023, Hackread.com reported a BEC 3.0 attack campaign leveraging Dropbox to send emails redirecting users to credential-harvesting pages.
Clicking on malicious links in phishing emails can lead to malware infections, stealing of sensitive data, and compromising login credentials. In business settings, a single employee’s account can allow attackers to access the entire SaaS environment, thereby disrupting operations.
Protection Against Phishing Attacks
While relying on common sense is typically the best defence against such attacks, scammers’ increasing sophistication can sometimes override our natural caution. Therefore, it’s crucial to proactively protect yourself. Here are 5 key points to help you recognize and safeguard against email phishing:
Suspicious Sender Addresses and Email Content:
Check sender email addresses carefully for typos or misspellings of legitimate companies. Be wary of generic greetings or an impersonal tone. Look for grammatical errors or unusual phrasing in the email body. Watch out for emails with a strong sense of urgency or pressure to act quickly.Malicious Links and Attachments:
Never click on links or open attachments in emails from unknown senders. Hover over a link to see the actual destination URL before clicking. It might not match the displayed text. Don’t download attachments you weren’t expecting, even from seemingly familiar senders.Phishing for Information:
Phishing emails often try to trick you into revealing personal information like passwords or credit card details. Legitimate companies will never ask for such information via email.Multi-Factor Authentication (MFA) and Strong Passwords:
Although, in this case, scammers bypass MFA, it is still the most preferred way to protect suspicious logins. Enable MFA on all your online accounts whenever possible. This adds an extra layer of security beyond just your password. Use strong, unique passwords for all your online accounts and avoid using the same password for multiple accounts.Staying Informed and Reporting Phishing Attempts:
Keep yourself updated on the latest phishing tactics by reading security blogs or news articles. Report suspicious emails to your email provider or the platform it impersonates. This helps them track and block future phishing attempts..png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·