BOOK THIS SPACE FOR AD
ARTICLE ADA Tesla employee was reportedly approached by a Russian national and asked to install malware on the company’s systems.
Tesla co-founder and CEO Elon Musk has confirmed reports that the Tesla Gigafactory Nevada was a target of a cyberattack earlier in August, which was subsequently thwarted by the Federal Bureau of Investigation.
Tesla Gigafactory Nevada is a lithium-ion battery and electric vehicle factory near Reno, Nevada. The facility, which is owned and operated by Tesla, supplies the battery packs for Tesla electric vehicles and stationary storage systems.
According to a Thursday report by Teslarati, an independent Tesla-focused blog, an employee at the Nevada factory was allegedly approached by a Russian national who offered up $1 million to infect the company with malware and compromise its networks. But the employee instead reported the incident to Tesla officials, who alerted the FBI, the report said.
“This was a serious attack,” Musk, co-founder and CEO of Tesla, tweeted in response to a Teslarati post on Twitter regarding the incident, Thursday.
Much appreciated. This was a serious attack.
— Elon Musk (@elonmusk) August 27, 2020
Teslarati’s report aligns with a criminal complaint filed Aug. 23 in U.S. District Court in Nevada (Threatpost has reached out to the DoJ to confirm that the complaint is related). The complaint accused Egor Igorevich Kriuchkov of attempting to recruit a worker to introduce malware at an unnamed company.
“The purpose of the conspiracy was to recruit an employee of a company to surreptitiously transmit malware provided by the coconspirators into the company’s computer system, exfiltrate data from the company’s network, and threaten to disclose the data online unless the company paid the coconspirators’ ransom demand,” according to the Department of Justice’s complaint.
The complaint outlined a detailed recruitment effort by Kriuchkov when it came to attempting to persuade the employee to install the malware.
Kriuchkov first contacted the Tesla employee via WhatsApp (with his number being provided via a mutual acquaintance). The two later met for a social trip, along with some colleagues, between Aug. 1 to Aug. 3, where they took a trip to Lake Tahoe.
On this trip, the complaint noted, Kriuchkov declined to be in any photos and also paid for all the group’s activities on the trip, claiming he had gambled at the hotel and won some money. These are two tell-tale signs of someone involved in criminal activity who is trying to recruit others, the complaint said.
“The indictment contains many details about the tradecraft the Russian national coached the employee on, such as using WhatsApp and airplane mode on their phone,” Katie Nickels, director of intelligence at Red Canary said via email. “We often would connect this type of tradecraft with fairly advanced adversaries, often those conducting espionage – yet there is no mention of espionage in this indictment.”
In a follow up meeting with the Tesla employee, Kriuchkov allegedly later explained that he worked for an unnamed group that would pay a large sum of money (later negotiated to up to $1 million) for the employee to install malware on Tesla’s systems.
The plan allegedly unveiled by Kriuchkov was to launch an external Distributed Denial of Service (DDoS) attack against the company, which would serve to preoccupy the company’s computer security staff and conceal a second cyberattack. This second attack would utilize the malware to exfiltrate data from the computer network and into the possession of the cybercriminals behind the attack. These cybercriminals would later contact the company and threaten to make the data public if the company does not pay a large ransom.
After contacting officials about the incident, the employee pretended to go along with the plan and wore a wire during future meetings with Kriuchkov, in cooperation with the FBI.
Finally, after being contacted by the FBI, Kriuchkov drove overnight from Reno, Nevada, to Los Angeles in an attempt to fly out of the country. He was then arrested Aug. 22 by the FBI.
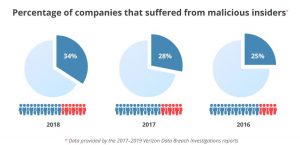 The incident is an example of the threat rogue insiders pose to companies. Insider threats are on the rise according to a Verizon Data Breach Investigations Report. A recent Bloomberg Government report also highlights how work-from-home trends are impacting the threat.
The incident is an example of the threat rogue insiders pose to companies. Insider threats are on the rise according to a Verizon Data Breach Investigations Report. A recent Bloomberg Government report also highlights how work-from-home trends are impacting the threat.
“Kudos to Tesla and the FBI in identifying and thwarting the reported attack, but in most cases, organizations can’t rely on external prior notification or assistance,” Matt Walmsley, EMEA Director at Vectra, said in an email. “Therefore, security teams need to be agile as time is their most precious resource in dealing with ransomware attacks and malicious insider behaviours.”
Threatpost has reached out to Tesla for further comment.
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Resister today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·