An emerging ransomware strain in the threat landscape claims to have breached 30 organizations in just four months since it went operational, riding on the coattails of a notorious ransomware syndicate.
First observed in February 2021, "Prometheus" is an offshoot of another well-known ransomware variant called Thanos, which was previously deployed against state-run organizations in the Middle East and North Africa last year.
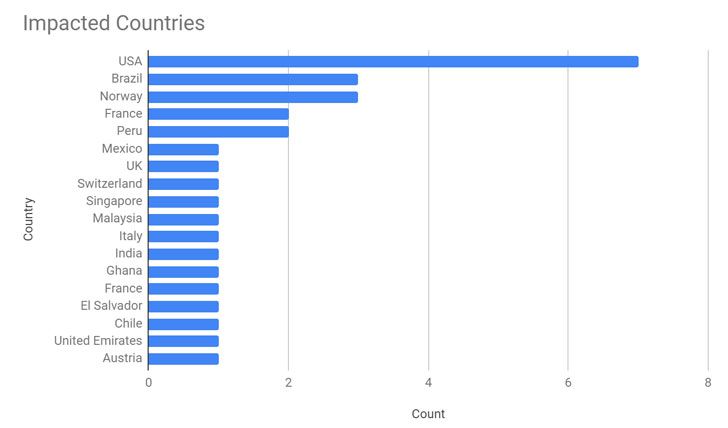
The affected entities are believed to be government, financial services, manufacturing, logistics, consulting, agriculture, healthcare services, insurance agencies, energy and law firms in the U.S., U.K., and a dozen more countries in Asia, Europe, the Middle East, and South America, according to new research published by Palo Alto Networks' Unit 42 threat intelligence team.
Like other ransomware gangs, Prometheus takes advantage of double-extortion tactics and hosts a dark web leak site, where it names and shames new victims and makes stolen data available for purchase, at the same time managing to inject a veneer of professionalism into its criminal activities.
"Prometheus runs like a professional enterprise," Doel Santos, Unit 42 threat intelligence analyst, said. "It refers to its victims as 'customers,' communicates with them using a customer service ticketing system that warns them when payment deadlines are approaching and even uses a clock to count down the hours, minutes and seconds to a payment deadline."
However, only four of those 30 affected organizations opted to pay ransoms to date, the cybersecurity firm's analysis revealed, including a Peruvian agricultural company, a Brazilian healthcare services provider, and two transportation and logistics organizations in Austria and Singapore.
It's worth noting that despite Prometheus' strong links to Thanos, the gang professes to be a "group of REvil," one of the most prolific and infamous ransomware-as-a-service (RaaS) cartels in recent years, which the researchers speculate could be an attempt to deflect attention from Thanos or a deliberate ploy to trick victims into paying up by piggybacking on an established operation.
While the ransomware's intrusion route remains unclear as yet, it's expected that the group purchased access to target networks or staged spear-phishing and brute-force attacks to gain initial access. Following a successful compromise, the Prometheus modus operandi involves terminating backup and security software-related processes on the system to lock the files behind encryption barriers.
"The Prometheus ransomware operators generate a unique payload per victim, which is used for their negotiation site to recover files," Santos said, adding the ransom demand ranges anywhere between $6,000 and $100,000 depending on the victim organization, a price that gets doubled if the victim fails to pay up within the designated time period.
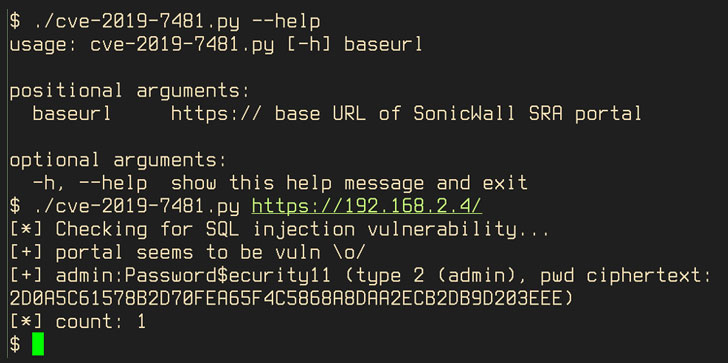
The development also comes as cybercrime groups are increasingly targeting SonicWall devices to breach corporate networks and deploy ransomware. A report published by CrowdStrike this week found evidence of remote access vulnerabilities (CVE-2019-7481) in SonicWall SRA 4600 VPN appliances being exploited as an initial access vector for ransomware attacks targeting organizations worldwide.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
245
3 years ago
245 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·