BOOK THIS SPACE FOR AD
ARTICLE ADHundreds of U.S. organizations on Thursday received emails purporting to come from the Democratic National Committee, in a new politically charged Emotet spear-phishing attack.
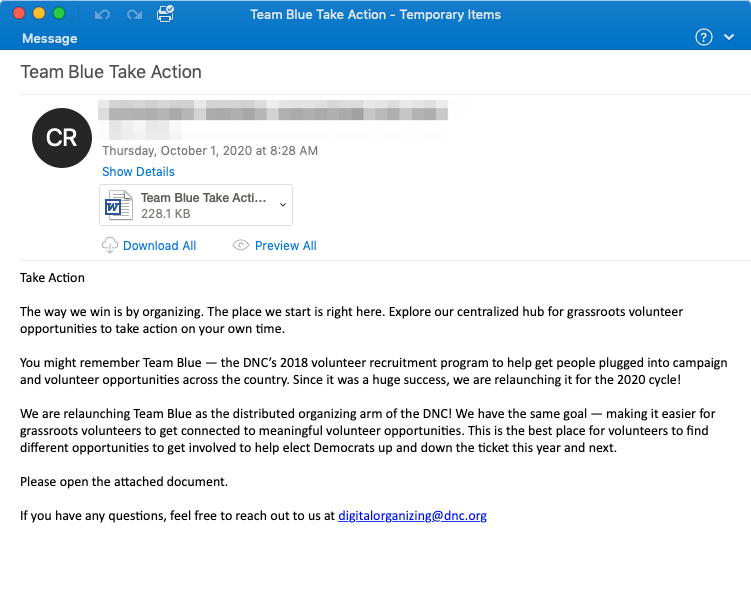
On Thursday, hundreds of U.S. organizations were targeted by an Emotet spear-phishing campaign, which sent thousands of emails purporting to be from the Democratic National Committee and recruiting potential Democratic volunteers.
Emotet has historically utilized a variety of lure themes leveraging current events – from COVID-19 to Greta Thunberg. However, the threat actor behind the malware, TA542, has not directly leveraged political themes in their messaging before. That changed with Thursday’s email campaign, which featured Word Document attachments labeled “Team Blue Take Action,” which actually infected victims with Emotet.
“The shift to using politically themed lures comes days after the first of several 2020 U.S. presidential debates,” said researchers with Proofpoint in a Thursday post. “The debate received widespread media coverage, and as Election Day draws nearer, many voters are likely feeling compelled to volunteer for political causes or for the election in some way.”
The email messages had the subject line “Team Blue Take Action,” with a message body taken directly from a page on the Democratic National Committee’s (DNC) website (democrats.org/team-blue) said researchers. This message body describes Team Blue, which is the DNC’s 2018 volunteer recruitment program – and says that Team Blue is being relaunched for the 2020 campaign. The email then asks the recipient to open the attached document.
This Word Document contains macros, which, if enabled, will download and install Emotet. Currently, researchers said they are also seeing a second stage payload following Emotet infections within this campaign, which either come in the form of the Qbot trojan or The Trick.
Beyond the email subject line “Team Blue Take Action,” researchers also observed other subject lines, including “Valanters 2020,” “List of Works” and more, with varying file names such as “Detailed information.doc” and “Volunteer.doc.”
Though disinformation is a key concern for many as the November U.S. presidential elections draw near, researchers believe that this lure was simply used to convince as many voters – fired up after Tuesday evening’s debate – to click as possible.
“It’s unlikely that this shift is driven by any specific political ideology,” they said. “Like earlier use of COVID-19 or Greta Thunberg lure themes, TA542 is attempting to reach as many intended recipients as possible by capitalizing on a popular topic.”
Emotet started life as a banking trojan in 2014 and has continually evolved to become a full-service threat-delivery mechanism. It can install a collection of malware on victim machines, including information stealers, email harvesters, self-propagation mechanisms and ransomware.
Emotet returned earlier in July after a five-month hiatus, when researchers spotted the malware in a campaign that has spammed Microsoft Office users with hundreds of thousands of malicious emails since Friday. The malware first emerged in 2014, but has since then evolved into a full fledged botnet that’s designed to steal account credentials and download further malware.
Emotet was last seen in February 2020, in a campaign that sent SMS messages purporting to be from victims’ banks. Once victims clicked on the links in the text messages, they are asked to hand over their banking credentials and download a file that infects their systems with the Emotet malware. Also in February, researchers uncovered an Emotet malware sample with the ability to spread to insecure Wi-Fi networks that are located nearby to an infected device.
On October 14 at 2 PM ET Get the latest information on the rising threats to retail e-commerce security and how to stop them. Register today for this FREE Threatpost webinar, “Retail Security: Magecart and the Rise of e-Commerce Threats.” Magecart and other threat actors are riding the rising wave of online retail usage and racking up big numbers of consumer victims. Find out how websites can avoid becoming the next compromise as we go into the holiday season. Join us Wednesday, Oct. 14, 2-3 PM ET for this LIVE webinar.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·